This free Notion document contains the best 100+ resources you need for building a successful startup, divided in 4 categories: Fundraising, People, Product, and Growth.

This free eBook goes over the 10 slides every startup pitch deck has to include, based on what we learned from analyzing 500+ pitch decks, including those from Airbnb, Uber and Spotify.

This free sheet contains 100 accelerators and incubators you can apply to today, along with information about the industries they generally invest in.

This free sheet contains 100 VC firms, with information about the countries, cities, stages, and industries they invest in, as well as their contact details.

This free sheet contains all the information about the top 100 unicorns, including their valuation, HQ's location, founded year, name of founders, funding amount and number of employees.


12 Types of Business Risks and How to Manage Them
Description

Everything you need to raise funding for your startup, including 3,500+ investors, 7 tools, 18 templates and 3 learning resources.

Information about the countries, cities, stages, and industries they invest in, as well as their contact details.

List of 250 startup investors in the AI and Machine Learning industries, along with their Twitter, LinkedIn, and email addresses.

List of startup investors in the BioTech, Health, and Medicine industries, along with their Twitter, LinkedIn, and email addresses.

List of startup investors in the FinTech industry, along with their Twitter, LinkedIn, and email addresses.
90% of startups fail .
Thanks to the explosion of the digital economy, business founders have plenty of opportunities that they can tap into to build a winning business.
Unfortunately, there is a myriad of challenges your new business has to navigate through. These risks are inevitable, and they are a part of life in the business world.
However, without the right plan, strategy, and instruments, your business might be drowned by these challenges.
Therefore, we have created this guide to show you how can your business utilize risk management to succeed in 2022.
There are many types of startup and business risks that entrepreneurs can expect to encounter in 2022. Most of these threats are prevalent in the infancy stages of a business.
To know what you’ll be up against, here is a breakdown of the 12 most common threats.
12 Business Risks to Plan For
1) economic risks.
Failure to acquire adequate funding for your business can damage the chances of your business succeeding.
Before a new business starts making profits, it needs to be kept afloat with money. Bills will pile up, suppliers will need payments, and your employees will be expecting their salaries.
To avoid running into financial problems sooner or later, you need to acquire enough funds to shore up your business until it can support itself.
On the side, world and business country's economic situation can change either positively or negatively, leading to a boom in purchases and opportunities or to a reduction in sales and growth.
If your business is up and running, a great way to limit the effect of negative economic changes is to maintain steady cash flow and operate under the lean business method.
Here's an article from a founder explaining how he set up a lean budget on his $400k/year online business.
2) Market Risks
Misjudging market demand is one of the primary reasons businesses fail .
To avoid falling into this trap, conduct detailed research to understand whether you will find a ready market for what you want to sell at the price you have set.
Ensure your business has a unique selling point, and make sure what you offer brings value to the buyers.
To know whether your product will suit the market, do a survey, or get opinions from friends and potential customers.
Building a Minimum Viable Product of that business idea you've had is the recommendations made by most entrepreneurs.
This site, for example, was built in just 3 weeks and launched into the market to see if there was any interest in the type of content we offered.
The site was ugly, had little content and lacked many features. Yet, +7,700 users visited it within the first week, which made us realize we should keep working on this.

90% of startups fail. Learn how to not to with our weekly guides and stories. Join 40,000+ founders.
3) Competitive Risks
Competition is a major business killer that you should be wary of.
Before you even start planning, ask yourself whether you are venturing into an oversaturated market.
Are there gaps in the market that you can exploit and make good money?
If you have an idea that can give you an edge, register it. This will prevent others from copying your product, re-innovating it, and locking you out of what you started.
Competitive risks are also those actions made by competitors that prevent a business from earning more revenue or having higher margins.
4) Execution Risks
Having an idea, a business plan, and an eager market isn’t enough to make your startup successful.
Most new companies put a lot of effort into the initial preparation and forget that the execution phase is equally important.
First, test whether you can develop your products within budget and on time. Also, check whether your product will function as intended and whether it’s possible to distribute it without taking losses.
5) Strategic Risks
Business strategies can lead to the growth or decline of a company.
Every strategy involves some risk, as time & resources are generally involved to put them into practice.
Strategic risk in the chance that an implemented strategy, therefore, results in losses.
If, for example, the Marketing Department of a company implements a content marketing strategy and a lot of months, time & money later the business doesn't see any ROI, this becomes a strategic risk.
6) Compliance Risks
Compliance risks are those losses and penalties that a business suffers for not complying with countries' and states' regulations & laws.
There are some industries that are highly-regulated so the compliance risks of businesses within them are super high.
For example, in May 2018, the EU Commission implemented the General Data Protection Regulation (GDPR), a law in privacy and data protection in the EU, which affected millions of websites.
Those websites that weren't adapted to comply with this new rule, were fined.
7) Operational Risks
Operational risks arise when the day-to-day running of a company fail to perform.
When processes fail or are insufficient, businesses lose customers and revenue and their reputation gets ruined.
One example can be customer service processes. Customers are becoming every day less willing to wait for support (not to mention, receive bad quality one).
If a business customer service team fails or delays to solve customer's issues, these might find their solution in the business competitors.
8) Reputational Risks
Reputational risks arise when a business acts in an immoral and discourteous way.
This led to customer complaints and distrust towards the business, which means for the company a big loss of sales and revenue.
With the rise of social networks, reputational risks have become one of the main concerns for businesses.
Virality is super easy among Twitter so a simple unhappy customer can lead to a huge bad press movement for the company.
A recent example is the Away issue with their toxic work environment, as a former employee reported in The Verge .
The issue brought lots of critics within social networks which eventually led the CEO, Steph Korey, to step aside from the startup ( she seems to be back, anyway 🤷♂️! ).
9) Country Risks
When a business invests in a new country, there is a high probability it won't work.
A product that is successful in one market won't necessarily be in another one, especially when people within them are so different in cultures, climates, tastes backgrounds, etc.
Country risk is the existing failure probability businesses investing in new countries have to deal with.
Changes in exchange rates, unstable economic situations and moving politics are three factors that make these country risks be even more delicate.
10) Quality Risks
When a business develops a product or service that fails to meet customers' needs and quality expectations, the chance these customers will ever buy again is low.
In this way, the business loses future sales and revenue. Not to mention that some customers will ask for refunds, increasing business costs, as well as publicly criticize the company's products, leading to bad reputation (and a viral cycle that means even less $$ for the business).
11) Human Risk
Hiring has its benefits but also its risks.
Employees themselves involve a huge risk for a business, as they become to represent the company through how they work, mistakes committed, the public says and interactions with customers & suppliers,
A way to deal with human risk is to train employees and keep a motivated workforce. Yet, the risk will continue to exist.
12) Technology Risk
Security attacks, power outrage, discontinued hardware, and software, among other technology issues, are the events that form part of the technology risk.
These issues can lead to a loss of money, time and data, which has many connections with the previously mentioned risks.
Back-ups, antivirus, control processes, and data breach plans are some of the ways to deal with this risk.
How Businesses Can Use Risk Management To Grow Business
To mitigate any future threats, you need to prepare a comprehensive risk management plan.
This plan should detail the strategy you will use to deal with the specific challenges your business will encounter. Here’s what to do.
1) Identify Risks
Every business encounters a different set of challenges.
Before mapping the risks, analyze your business and note down its key components such as critical resources, important services or products, and top talent.
2) Record Risks
Once risks have been identified, you need to assess and document the threats that can affect each component.
Identify any warning signs or triggers of that recorded risk, also.
3) Anticipate
The best way to beat a threat is to detect and prepare for it in advance.
Once you know your business can be affected by a certain scenario, develop steps that you will take to stop the risk or to blunt its effects.
4) Prioritize Risks
Not all types of business risk have the same effect. Some can bring your startup to its knees, while others will only cause minimal effects.
To keep your business alive, start by putting in place measures that protect the vital functions from the most severe and most probable risks.
5) Have a Backup Plan
For every risk scenario, have at least two plans for countering the threat before it arrives.
The strategy you put in place should be in line with the current technology and trends.
Ensure your communicate these measures with all your team members.
6) Assign Responsibilities
When communicating measures with the team, assign responsibilities for each member in case any of the recorded risks affect the business.
These members should also be responsible for controlling the risks every certain time and maintaining records about them.
What is a Business Risk?
The term "business risk" refers to the exposure businesses have to factors that can prevent them from achieving their set financial goals.
This exposure can come from a variety of situations, but they can be classified into two:
- Internal factors: The risk comes from sources within the company, and they tend to be related to human, technological, physical or operational factors, among others.
- External factors: The risk comes from regulations/changes affecting the whole country/economy.
Any of these factors led to the business being unable to return investors and stakeholders the adequate amounts.
What Is Risk Management?
Risk management is a practice where an entrepreneur looks for potential risks that their business may face, analyzes them, and takes action to counter them.
The steps you take can eliminate the threat, control it, or limit the effects.
A risk is any scenario that harms your business. Risks can emanate from a wide variety of sources such as financial problems, management errors, lawsuits, data loss, cyber-attacks, natural calamities, and theft.
The risk landscape changes constantly, therefore you need to know the latest threats.
By setting up a risk management plan, your business can save money and time, which in some cases can be the determinant to keep your startup in business.
Not to mention, on the side, that risk management plans tend to make managers feel more confident to carry out business decisions, especially the risky ones, which can put their startups in a huge competitive advantage.
Wrapping Up
Becoming your own boss is one of the most rewarding things you can do.
However, launching a business is not a walk in the park; risks and challenges lurk around every corner.
If you are planning to establish a new business come 2022, make sure you secure its future by creating a broad risk management plan.

90% of startups fail. Learn how not to with our weekly guides and stories. Join +40,000 other startup founders!
An all-in-one newsletter for startup founders, ruled by one philosophy: there's more to learn from failures than from successes.
100+ resources you need for building a successful startup, divided into 4 categories: Fundraising, People, Product, and Growth.
What is business risk?

You know about death and taxes. What about risk? Yes, risk is just as much a part of life as the other two inevitabilities. This became all the more apparent during COVID-19, as each of us had to assess and reassess our personal risk calculations as each new wave of the pandemic— and pandemic-related disruptions —washed over us. It’s the same in business: executives and organizations have different comfort levels with risk and ways to prepare against it.
Where does business risk come from? To start with, external factors can wreak havoc on an organization’s best-laid plans. These can include things like inflation , supply chain disruptions, geopolitical upheavals , unpredictable force majeure events like a global pandemic or climate disaster, competitors, reputational issues, or even cyberattacks .
But sometimes, the call is coming from inside the house. Companies can be imperiled by their own executives’ decisions or by leaks of privileged information, but most damaging of all, perhaps, is the risk of missed opportunities. We’ve seen it often: when companies choose not to adopt disruptive innovation, they risk losing out to more nimble competitors.
The modern era is rife with increasingly frequent sociopolitical, economic, and climate-related shocks. In 2019 alone, for example, 40 weather disasters caused damages exceeding $1 billion each . To stay competitive, organizations should develop dynamic approaches to risk and resilience. That means predicting new threats, perceiving changes in existing threats, and developing comprehensive response plans. There’s no magic formula that can guarantee safe passage through a crisis. But in situations of threat, sometimes only a robust risk-management plan can protect an organization from interruptions to critical business processes. For more on how to assess and prepare for the inevitability of risk, read on.
Learn more about McKinsey’s Risk and Resilience Practice.
What is risk control?
Risk controls are measures taken to identify, manage, and eliminate threats. Companies can create these controls through a range of risk management strategies and exercises. Once a risk is identified and analyzed, risk controls can be designed to reduce the potential consequences. Eliminating a risk—always the preferable solution—is one method of risk control. Loss prevention and reduction are other risk controls that accept the risk but seek to minimize the potential loss (insurance is one method of loss prevention). A final method of risk control is duplication (also called redundancy). Backup servers or generators are a common example of duplication, ensuring that if a power outage occurs no data or productivity is lost.
But in order to develop appropriate risk controls, an organization should first understand the potential threats.
What are the three components to a robust risk management strategy?
A dynamic risk management plan can be broken down into three components : detecting potential new risks and weaknesses in existing risk controls, determining the organization’s appetite for risk taking, and deciding on the appropriate risk management approach. Here’s more information about each step and how to undertake them.
1. Detecting risks and controlling weaknesses
A static approach to risk is not an option, since an organization can be caught unprepared when an unlikely event, like a pandemic, strikes. So it pays to always be proactive. To keep pace with changing environments, companies should answer the following three questions for each of the risks that are relevant to their business.
- How will a risk play out over time? Risks can be slow moving or fast moving. They can be cyclical or permanent. Companies should analyze how known risks are likely to play out and reevaluate them on a regular basis.
- Are we prepared to respond to systemic risks? Increasingly, risks have longer-term reputational or regulatory consequences, with broad implications for an industry, the economy, or society at large. A risk management strategy should incorporate all risks, including systemic ones.
- What new risks lurk in the future? Organizations should develop new methods of identifying future risks. Traditional approaches that rely on reviews and assessments of historical realities are no longer sufficient.
2. Assessing risk appetite
How can companies develop a systematic way of deciding which risks to accept and which to avoid? Companies should set appetites for risk that align with their own values, strategies, capabilities, and competitive environments—as well as those of society as a whole. To that end, here are three questions companies should consider.
- How much risk should we take on? Companies should reevaluate their risk profiles frequently according to shifting customer behaviors, digital capabilities, competitive landscapes, and global trends.
- Are there any risks we should avoid entirely? Some risks are clear: companies should not tolerate criminal activity or sexual harassment. Others are murkier. How companies respond to risks like economic turmoil and climate change depend on their particular business, industry, and levels of risk tolerance.
- Does our risk appetite adequately reflect the effectiveness of our controls? Companies are typically more comfortable taking risks for which they have strong controls in place. But the increased threat of severe risks challenges traditional assumptions about risk control effectiveness. For instance, many businesses have relied on automation to increase speed and reduce manual error. But increased data breaches and privacy concerns can increase the risk of large-scale failures. Organizations, therefore, should evolve their risk profiles accordingly.
3. Deciding on a risk management approach
Finally, organizations should decide how they will respond when a new risk is identified. This decision-making process should be flexible and fast, actively engaging leaders from across the organization and honestly assessing what has and hasn’t worked in past scenarios. Here are three questions organizations should be able to answer.
- How should we mitigate the risks we are taking? Ultimately, people need to make these decisions and assess how their controls are working. But automated control systems should buttress human efforts. Controls guided, for example, by advanced analytics can help guard against quantifiable risks and minimize false positives.
- How would we respond if a risk event or control breakdown happens? If (or more likely, when) a threat occurs, companies should be able to switch to crisis management mode quickly, guided by an established playbook. Companies with well-rehearsed crisis management capabilities weather shocks better, as we saw with the COVID-19 pandemic.
- How can we build true resilience? Resilient companies not only better withstand threats—they emerge stronger. The most resilient firms can turn fallout from crises into a competitive advantage. True resilience stems from a diversity of skills and experience, innovation, creative problem solving, and the basic psychological safety that enables peak performance.
Change is constant. Just because a risk control plan made sense last year doesn’t mean it will next year. In addition to the above points, a good risk management strategy involves not only developing plans based on potential risk scenarios but also evaluating those plans on a regular basis.
Learn more about McKinsey’s Risk and Resilience Practice.
What are five actions organizations can take to build dynamic risk management?
In the past, some organizations have viewed risk management as a dull, dreary topic, uninteresting for the executive looking to create competitive advantage. But when the risk is particularly severe or sudden, a good risk strategy is about more than competitiveness—it can mean survival. Here are five actions leaders can take to establish risk management capabilities .
- Reset the aspiration for risk management. This requires clear objectives and clarity on risk levels and appetite. Risk managers should establish dialogues with business leaders to understand how people across the business think about risk, and share possible strategies to nurture informed risk-versus-return decision making—as well as the capabilities available for implementation.
- Establish agile risk management practices. As the risk environment becomes more unpredictable, the need for agile risk management grows. In practice, that means putting in place cross-functional teams empowered to make quick decisions about innovating and managing risk.
- Harness the power of data and analytics. The tools of the digital revolution can help companies improve risk management. Data streams from traditional and nontraditional sources can broaden and deepen companies’ understandings of risk, and algorithms can boost error detection and drive more accurate predictions.
- Develop risk talent for the future. Risk managers who are equipped to meet the challenges of the future will need new capabilities and expanded domain knowledge in model risk management , data, analytics, and technology. This will help support a true understanding of the changing risk landscape , which risk leaders can use to effectively counsel their organizations.
- Fortify risk culture. Risk culture includes the mindsets and behavioral norms that determine an organization’s relationship with risk. A good risk culture allows an organization to respond quickly when threats emerge.
How do scenarios help business leaders understand uncertainty?
Done properly, scenario planning prompts business leaders to convert abstract hypotheses about uncertainties into narratives about realistic visions of the future. Good scenario planning can help decision makers experience new realities in ways that are intellectual and sensory, as well as rational and emotional. Scenarios have four main features that can help organizations navigate uncertain times.
- Scenarios expand your thinking. By developing a range of possible outcomes, each backed with a sequence of events that could lead to them, it’s possible to broaden our thinking. This helps us become ready for the range of possibilities the future might hold—and accept the possibility that change might come more quickly than we expect.
- Scenarios uncover inevitable or likely futures. A broad scenario-building effort can also point to powerful drivers of change, which can help to predict potential outcomes. In other words, by illuminating critical events from the past, scenario building can point to outcomes that are very likely to happen in the future.
- Scenarios protect against groupthink. In some large corporations, employees can feel unsafe offering contrarian points of view for fear that they’ll be penalized by management. Scenarios can help companies break out of this trap by providing a “safe haven” for opinions that differ from those of senior leadership and that may run counter to established strategy.
- Scenarios allow people to challenge conventional wisdom. In large corporations in particular, there’s frequently a strong bias toward the status quo. Scenarios are a nonthreatening way to lay out alternative futures in which assumptions underpinning today’s strategy can be challenged.
Learn more about McKinsey’s Strategy & Corporate Finance Practice.
What’s the latest thinking on risk for financial institutions?
In late 2021, McKinsey conducted survey-based research with more than 30 chief risk officers (CROs), asking about the current banking environment, risk management practices, and priorities for the future.
According to CROs, banks in the current environment are especially exposed to accelerating market dynamics, climate change, and cybercrime . Sixty-seven percent of CROs surveyed cited the pandemic as having significant impact on employees and in the area of nonfinancial risk. Most believed that these effects would diminish in three years’ time.

Looking for direct answers to other complex questions?
Climate change, on the other hand, is expected to become a larger issue over time. Nearly all respondents cited climate regulation as one of the five most important forces in the financial industry in the coming three years. And 75 percent were concerned about climate-related transition risk: financial and other risks arising from the transformation away from carbon-based energy systems.
And finally, cybercrime was assessed as one of the top risks by most executives, both now and in the future.
Learn more about the risk priorities of banking CROs here .
What is cyber risk?
Cyber risk is a form of business risk. More specifically, it’s the potential for business losses of all kinds in the digital domain—financial, reputational, operational, productivity related, and regulatory related. While cyber risk originates from threats in the digital realm, it can also cause losses in the physical world, such as damage to operational equipment.
Cyber risk is not the same as a cyberthreat. Cyberthreats are the particular dangers that create the potential for cyber risk. These include privilege escalation (the exploitation of a flaw in a system for the purpose of gaining unauthorized access to resources), vulnerability exploitation (an attack that uses detected vulnerabilities to exploit the host system), or phishing. The risk impact of cyberthreats includes loss of confidentiality, integrity, and availability of digital assets, as well as fraud, financial crime, data loss, or loss of system availability.
In the past, organizations have relied on maturity-based cybersecurity approaches to manage cyber risk. These approaches focus on achieving a particular level of cybersecurity maturity by building capabilities, like establishing a security operations center or implementing multifactor authentication across the organization. A maturity-based approach can still be helpful in some situations, such as for brand-new organizations. But for most institutions, a maturity-based approach can turn into an unmanageably large project, demanding that all aspects of an organization be monitored and analyzed. The reality is that, since some applications are more vulnerable than others, organizations would do better to measure and manage only their most critical vulnerabilities.
What is a risk-based cybersecurity approach?
A risk-based approach is a distinct evolution from a maturity-based approach. For one thing, a risk-based approach identifies risk reduction as the primary goal. This means an organization prioritizes investment based on a cybersecurity program’s effectiveness in reducing risk. Also, a risk-based approach breaks down risk-reduction targets into precise implementation programs with clear alignment all the way up and down an organization. Rather than building controls everywhere, a company can focus on building controls for the worst vulnerabilities.
Here are eight actions that comprise a best practice for developing a risk-based cybersecurity approach:
- fully embed cybersecurity in the enterprise-risk-management framework
- define the sources of enterprise value across teams, processes, and technologies
- understand the organization’s enterprise-wide vulnerabilities—among people, processes, and technology—internally and for third parties
- understand the relevant “threat actors,” their capabilities, and their intent
- link the controls in “run” activities and “change” programs to the vulnerabilities that they address and determine what new efforts are needed
- map the enterprise risks from the enterprise-risk-management framework, accounting for the threat actors and their capabilities, the enterprise vulnerabilities they seek to exploit, and the security controls of the organization’s cybersecurity run activities and change program
- plot risks against the enterprise-risk appetite; report on how cyber efforts have reduced enterprise risk
- monitor risks and cyber efforts against risk appetite, key cyber risk indicators, and key performance indicators
How can leaders make the right investments in risk management?
Ignoring high-consequence, low-likelihood risks can be catastrophic to an organization—but preparing for everything is too costly. In the case of the COVID-19 crisis, the danger of a global pandemic on this scale was foreseeable, if unexpected. Nevertheless, the vast majority of companies were unprepared: among billion-dollar companies in the United States, more than 50 filed for bankruptcy in 2020.
McKinsey has described the decisions to act on these high-consequence, low-likelihood risks as “ big bets .” The number of these risks is far too large for decision makers to make big bets on all of them. To narrow the list down, the first thing a company can do is to determine which risks could hurt the business versus the risks that could destroy the company. Decision makers should prioritize the potential threats that would cause an existential crisis for their organization.
To identify these risks, McKinsey recommends using a two-by-two risk grid, situating the potential impact of an event on the whole company against the level of certainty about the impact. This way, risks can be measured against each other, rather than on an absolute scale.
Organizations sometimes survive existential crises. But it can’t be ignored that crises—and missed opportunities—can cause organizations to fail. By measuring the impact of high-impact, low-likelihood risks on core business, leaders can identify and mitigate risks that could imperil the company. What’s more, investing in protecting their value propositions can improve an organization’s overall resilience.
Articles referenced:
- “ Seizing the momentum to build resilience for a future of sustainable inclusive growth ,” February 23, 2023, Børge Brende and Bob Sternfels
- “ Data and analytics innovations to address emerging challenges in credit portfolio management ,” December 23, 2022, Abhishek Anand , Arvind Govindarajan , Luis Nario and Kirtiman Pathak
- “ Risk and resilience priorities, as told by chief risk officers ,” December 8, 2022, Marc Chiapolino , Filippo Mazzetto, Thomas Poppensieker , Cécile Prinsen, and Dan Williams
- “ What matters most? Six priorities for CEOs in turbulent times ,” November 17, 2022, Homayoun Hatami and Liz Hilton Segel
- “ Model risk management 2.0 evolves to address continued uncertainty of risk-related events ,” March 9, 2022, Pankaj Kumar, Marie-Paule Laurent, Christophe Rougeaux, and Maribel Tejada
- “ The disaster you could have stopped: Preparing for extraordinary risks ,” December 15, 2020, Fritz Nauck , Ophelia Usher, and Leigh Weiss
- “ Meeting the future: Dynamic risk management for uncertain times ,” November 17, 2020, Ritesh Jain, Fritz Nauck , Thomas Poppensieker , and Olivia White
- “ Risk, resilience, and rebalancing in global value chains ,” August 6, 2020, Susan Lund, James Manyika , Jonathan Woetzel , Edward Barriball , Mekala Krishnan , Knut Alicke , Michael Birshan , Katy George , Sven Smit , Daniel Swan , and Kyle Hutzler
- “ The risk-based approach to cybersecurity ,” October 8, 2019, Jim Boehm , Nick Curcio, Peter Merrath, Lucy Shenton, and Tobias Stähle
- “ Value and resilience through better risk management ,” October 1, 2018, Daniela Gius, Jean-Christophe Mieszala , Ernestos Panayiotou, and Thomas Poppensieker

Want to know more about business risk?
Related articles.

What matters most? Six priorities for CEOs in turbulent times

Creating a technology risk and cyber risk appetite framework

Risk and resilience priorities, as told by chief risk officers

Risk Management, Risk Analysis, Templates and Advice
- #1 Mind Mapping Tool
- Collaborate Anywhere
- Stunning Presentations
- Simple Project Management
- Innovative Project Planning
- Creative Problem Solving

The Top 50 Business Risks And How To Manage them!
Risk is simply uncertainty of outcome whether positive or negative ( PRINCE2, 2002, p239 ). Business risk is uncertainty around strategy, profits, compliance, environment, health and safety and so on. stakeholdermap.com

The Top 50 Business Risks
| Business Risk description | Actions that could be taken to manage the risk |
|---|---|
| 1. Assets - to buildings, assets e.g. fire, flooding | |
| 2. Bad debt | |
| 3. Bankruptcy of suppliers or clients | |
| 4. Brand fatigue | |
| 5. - poor or becoming less effective | |
| 6. Cashflow | |
| 7. Client attrition |
| Risk description | Actions that could be taken to manage the risk |
|---|---|
| 8. Competition: aggressive | |
| 9. Competition: better intelligence | |
| 10. Competition: legal action | of legal action |
| 11. Compliance with regulations, laws etc | team |
| 12. Copyright theft - theft of your copyright or action against your business | |
| 13. Cost of components - increase or decrease | |
| 14. Customer satisfaction low |
| Risk description | Actions that could be taken to manage the risk |
|---|---|
| 15. Data security | |
| 16. Difficult-to-sell product | materials, sales plays, provide additional sales training |
| 17. Environment - natural or business environment | to employees of extreme weather - ensure safe temperatures at work, access to water, home working in bad weather, support with travel, accomodation etc to facilities, buildings, , materials - insurance e.g. buildings and contents, invest in storm protection, fire prevention etc |
| 18. Espionage (commercial) | |
| 19. Exchange rates e.g. forex | and buy or sell currency in the spot market |
| 20. Failure of utilities e.g. water, electricity | |
| 21. Health and safety | and complete a |
| Risk description | Actions that could be taken to manage the risk |
| 22. Lack of office space | |
| 23. Lack of skills/expertise | |
| 24. Loss of key skills | |
| 25. Loss of political support | |
| 26. Machinery failure | |
| 27. Market acceptance | |
| 28. Market changes e.g. movements in stock prices, interest rates, commodity prices. | |
| 29. Natural disaster | |
| 30. New markets - distract or provide opportunity | |
| 31. Operational risk e.g. risk to day-to-day | |
| 32. Patent theft/infringement - of your patents or competitor against your business | |
| 33. Poor management | |
| 34. Political instability e.g. coup, or political unrest | |
| 35. Profit - loss of profit or missing profit projections |
| Risk description | Actions that could be taken to manage the risk |
| 36. Recession | |
| 37. Regulatory compliance - difficulty in compliance or failure to comply | |
| 38. Reputation - negatively impacted | |
| 39. Revenue forecast missed | |
| 40. Seasonal risk | |
| 41. Staff sickness/absence | |
| 42. Supply chain failure/delays | procedures |
| 43. Technology - advances provide opportunity or threaten existing products | |
| 44. Technology breakdown e.g. server outage | |
| 45. Theft - of product, information from shop floor | |
| 46. Time-to-market | |
| 47. Transportation delay or damage | |
| 48. Under-resourcing | needed over peak periods e.g. Amazon warehouse model from repetitive time-consuming work |
| 49. Unexpected demand - supply issues | |
| 50. War - military conflicts |
Download the full list of Business Risks
Word download - the top 50 business risks (word), pdf download - the top 50 business risks (pdf), 20 common project risks - example risk register, checklist of 30 construction risks, overall project risk assessment template, simple risk register - excel template, business risk - references and further reading, read more on risk management.
- Risk Assessment
- Construction Risk Management
- Risk Management Glossary
- Risk Management Guidelines
- Risk Identification
- NHS Risk Register
- Risk Register template
- Risk Management Report
- Risk Responses
- Prince2 Risk Register
- Prince2 Risk Management Strategy
Share this Image


Risk Mitigation Strategies: Types & Examples (+ Free Template)

Effective enterprise risk management is more important than ever. A recent 2023 State of Risk Oversight Report by NC State University shows that while two-thirds of business leaders (out of 454 respondents) acknowledge escalating risks, only a third are geared up to tackle them.
This points to a serious disconnect between the organization’s needs and its risk management strategy. No plan is bulletproof, but effective preparation and monitoring will help you minimize risks and their impact on business.
In this article, we explore the different risk mitigation strategies and how you can implement them to protect your organization’s performance and stability.

What Is Risk Mitigation?
Risk mitigation is a proactive business strategy to identify, assess, and mitigate potential threats or uncertainties that could harm an organization’s objectives, assets, or operations. It entails specific action plans to reduce the likelihood or impact of these identified risks.
Conversely, risk management is a broader, more comprehensive process that involves various stages like risk identification, assessment, response, and monitoring.
While risk mitigation focuses on direct actions to eliminate or diminish threats, risk management encompasses the entire life cycle of dealing with risks.
They may sound similar, but risk mitigation is a subset and vital component of the risk management process.
%20(1).png)
Why Is Risk Mitigation Important?
The stakes are high, according to the 2023 State of Risk Oversight Report. We're seeing near-record levels of risk events and complexities across organizations.
So what does a robust risk mitigation plan offer you? For starters, it's not about ignoring risks, but rather tackling them head-on with actionable steps. This ensures you have a business continuity plan in the face of disruptions.
An effective risk mitigation process also provides a clearer picture of potential obstacles, which helps with strategic decision-making. This helps manage operational risks and create a resilient supply chain . It also assures employees that they are working with a company that prioritizes job security.
But risk mitigation isn't all defense—it also sets you up to seize growth opportunities. By identifying and minimizing risks, you can make calculated moves that optimize your business portfolio .
What Are The Types Of Risks?
Your risk mitigation strategies should be tailored to your business, which means it can't be a carbon copy of another organization's risk mitigation strategy. The risks you face will vary based on your industry, sector, and other unique factors.

Some of the most common types of risks include:
- Competitor risk: Threats from rival organizations.
- Economic risk: Vulnerabilities due to economic fluctuations.
- Political risk: Impact of political factors.
- Financial risk: Exposure to financial uncertainties.
- Operational risk: Daily hazards in operations , including cybersecurity risks.
📚You can learn more about risk types and strategies to mitigate them in this article .
What Are The Risk Mitigation Strategies?
Described below are the most common risk mitigation strategies.
Tip: You should always start with a complete risk analysis to pick the right strategy for your business.
Risk avoidance strategy
The most straightforward way to deal with risks is to remove them entirely. This involves steering clear of any actions or situations that could harm your business. But be cautious: sidestepping one risk might require sacrificing other resources.
A large technology company plans to launch a new product in an international market, but a risk assessment uncovers considerable regulatory and political obstacles.
Opting for a risk avoidance strategy, the company chooses not to enter the new market, eliminating these high-stakes risks. Instead, it reallocates resources to bolster existing markets or pursue other low-risk opportunities.
While this approach removes immediate risks, it also sacrifices the potential revenue and growth the new product could have generated in that market.
Risk transfer strategy
Sometimes you can pass risks on to someone else. This usually involves using contracts, insurance, or outsourcing . This is a good strategy if it's cheaper to pay another company to take on the risk than to deal with it yourself.
💡 Examples:
- Work with a third-party logistics provider (3PL) for your shipping and delivery needs. The contract often includes clauses that transfer the risk of damaged or lost goods during transit to the 3PL. Upon damaged products, the 3PL is liable to compensate your business for the losses.
- Pay an insurance company a small fee to avoid the full financial implications of unforeseen events like accidents.
📚 Recommended read: Unlocking The Power Of Logistics Strategy To Achieve Supply Chain Excellence
Risk acceptance strategy
Sometimes taking a risk is a good choice, especially if the potential reward is high or the likelihood of problems is low. Each business has its own comfort level for risk and uses that to decide which risks are worth taking. It’s also better to accept risks if the costs of avoiding them are too high.
Many startups know they have a high chance of failing early on. But they're willing to take that risk because the possible rewards, like growth and profit, make it worthwhile.
If you’re following this strategy, you must constantly monitor the threat level. If it rises above acceptable risk levels, or if your risk appetite changes, you might need to switch to a different strategy to protect your business.
Risk reduction strategy
In cases where you can’t avoid or accept the risks, it’s best to pursue measures to reduce their impact altogether. Risk reduction involves implementing proactive and concrete actions to make a potential problem less severe.
💡 Examples:
- An oil drilling company in a hurricane-prone region may invest in advanced high-tech weather systems to better predict stores. This move will help them to prepare in advance and reduce the likelihood of costly disruptions due to natural disasters.
- If you identified that you’ll run out of funds to complete a project, you could switch to more affordable materials or scale back the project size. You could also look for extra funding. Each option helps lower the risk of running out of money before completing the project.
Risk monitoring strategy
Risks are an ongoing fact of doing business and carefully monitoring them will ensure that mitigation measures remain effective. Risk monitoring involves regular evaluations and adjustments to strategies to address changing circumstances.
💡 Example:
A manufacturing company can continually monitor supply chain risks like supplier reliability, geopolitical issues, and market trends. If there are potential disruptions, they can take timely actions to adjust sourcing strategies or secure alternative suppliers.
What Are The Steps To Mitigate Risks?
The following steps will help you identify risks and implement a responsive risk mitigation strategy:
1. Understand what you’re up against
Systematically examine all the possible risks to your business by conducting an internal and external analysis. You can use the SWOT analysis to identify the current and future state of your business. Pay attention to the “Threats” quadrant that highlights potential risks.
.jpg)
You can also use other strategic analysis tools like PESTLE Analysis or Porter’s 5 Forces to analyze the business’s external environment for any potential threats.
💡Involve key stakeholders to gain a diverse perspective and access to insights that may not be immediately apparent. They can help you see what’s happening on the front lines so you can assess risks accurately.
2. Assess and prioritize the risks
After listing all the possible risks, it’s time to analyze the probability of their occurrence and the potential negative impact. You can use a risk matrix to help you assess and prioritize risks based on their likelihood and impact. This will help you focus your resources on the most critical risks.

💡While the risk matrix is easy to read and use, it often relies on qualitative judgments. This can sometimes result in poor resource allocation. To avoid this, whenever possible, convert risks into monetary terms. This provides a more accurate picture of how each risk could financially impact your business.
3. Prepare a plan to execute your risk mitigation initiatives
Once you’ve identified and categorized the potential risks to your business, it’s time to create an action plan. For each identified risk, decide on the most suitable approach: will you avoid, mitigate, transfer, or simply accept it?
Once you've determined your approach for each risk, allocate the needed resources. This includes people, money, and time devoted to implementing the chosen risk mitigation strategies . Have a backup with contingency plans for risks that may not be fully addressed by your initial strategies.
💡You can use Cascade’s Risk Mitigation Strategy Plan Template to cover all the key elements of an effective strategy.
4. Execute your strategy and monitor risks
Risks are always changing. That's why you need to continuously keep an eye on them to make sure your mitigation plans are up-to-date. Establish regular check-ins, such as daily or weekly meetings, to quickly assess the status of your risk mitigation strategies.
To make this process even more efficient, use specific metrics tied to the risks you're managing. Set up triggers that alert you when it's time to take extra steps.
💡Look for strategy execution tools like Cascade that integrate seamlessly with various business platforms. This allows you to bring all your key business data together in a centralized hub, making it easier to stay on top of risks and adjust your strategies as needed.
5. Update risk and adapt your plan
As your business landscape evolves—whether due to market shifts, technological upgrades, or internal developments—your risk mitigation plan must keep pace. Not only can new risks arise, but the importance of existing risks can change as well.
To make these adjustments more data-driven, you can use Cascade's reports .
.png)
These reports help you pinpoint any threats, monitor risks, and keep your team aligned with updated priorities. By constantly refining your plan, you ensure it remains effective in a shifting environment.
Mitigate Risks And Master Chaos With Cascade 🚀
To be resilient and successful, it's crucial to spot and neutralize threats before they escalate. Instead of being reactive, the key is to be proactive—maintaining financial stability, safeguarding your reputation, and staying ahead of the competition.
With features like alignment and collaboration, real-time analytics, and data tracking in one place, Cascade empowers you to detect and manage risks with confidence.
Our strategy execution platform integrates various data sources, giving you centralized visibility over your execution engine. This insight enables you to clear dependencies and mitigate potential risks faster to improve your odds of success.
Curious? Sign up for free or book a 1:1 with Cascade strategy expert .
More related resilience and risk management strategy templates:
- 16 Business Continuity Plan Templates For Every Business
- Operational Risk Assessment Template
- Healthcare Risk Assessment Template
- Compliance Risk Management Plan Template
- Risk Response Plan Template
Popular articles

11 Best Strategic Frameworks For Your Organization + Free eBook

Strategic Analysis Complete Guide: Definition, Tools & Examples

6 Steps To Successful Strategy Execution & Best Practices
.png)
How To Create A Culture Of Strategy Execution
Your toolkit for strategy success.

- My Account My Account
- Cards Cards
- Banking Banking
- Travel Travel
- Rewards & Benefits Rewards & Benefits
- Business Business

Curated For You
Advertisement

Related Content
Types of business risks and ideas for managing them.

Published: July 06, 2023
Updated: July 05, 2024
There are several types of business risks that can threaten a company’s ability to achieve its goals. Learn some of the most common risks for businesses and ideas for how to manage them.
Business risks can include financial, cybersecurity, operational, and reputational risks, all of which can seriously impact a company’s strategic plans if business leaders don’t take action to mitigate them.
What’s most important is that business owners are aware of the risks that could shake up their operations. That way, they can take steps to prevent them or minimize their impact if they occur. Here’s a look at some common business risks.
Financial Risks
Companies must generate sufficient cash flow to make interest payments on loans and to meet other debt-related obligations on time. Financial risk refers to the flow of money in the business and the possibility of a sudden financial loss. A company may be at financial risk if it doesn’t have enough cash to properly manage its debt payments and becomes delinquent on its loans.
Businesses with relatively higher levels of debt financing are considered at higher financial risk, since lenders often see them as having a greater chance of not meeting payment obligations and becoming insolvent. Types of financial risk include:
- Credit risk: When a company extends credit to customers, there is the possibility that those customers may stop making payments, which reduces revenue and earnings. A company also faces credit risk when a lender extends business credit to make purchases. If the company doesn’t have enough money to pay back those loans, it will default.
- Currency risk: Currency risk, also known as exchange-rate risk, can arise from the change in price of one currency in relation to another. For example, if a U.S. company agrees to sell its products to a European company for a certain amount of euros, but the value of the euro rises suddenly at the time of delivery and payment, the U.S. business loses money because it takes more dollars to buy euros.
- Liquidity risk: A company faces liquidity risk when it cannot convert its assets into cash. This type of business risk often occurs when a company suddenly needs a substantial amount of cash to meet its short-term debt obligations. For example, a manufacturing company may not be able to sell outdated machines to generate cash if no buyers come forward.
Cybersecurity Risks
As more businesses use online channels for sales and e-commerce payments, as well as for collecting and storing customer data, they are exposed to greater opportunities for hacking, creating security risks for companies and their stakeholders. Both employees and customers expect companies to protect their personal and financial information, but despite ongoing efforts to keep this information safe, companies have experienced data breaches, identity theft, and payment fraud incidents.
When these incidents happen, consumer confidence and trust in companies can take a dive.
Not only do security breaches threaten a company’s reputation, but the company is sometimes financially liable for damages.
Ideas for managing security risks:
- Investing in fraud detection tools and software security solutions .
- Educating employees about how they can do their part to keep the company’s data safe. Basic guidance includes not clicking suspicious links in emails or sharing sensitive data without encrypting it first.
Operational Risks
A business is considered to have operational risk when its day-to-day activities threaten to decrease profits. Operational risks can result from employee errors, such as undercharging customers. Additionally, a natural disaster like a tornado, hurricane, or flood might damage a company’s buildings or other physical assets, disrupting its daily operations.
Of course, one of the starkest examples of negative impacts to companies' production and supply chain operations is the Coronavirus pandemic. In an April 2022 Small Business Pulse Survey conducted by the U.S. Census Bureau, roughly 65 percent of respondents reported that the pandemic had either a moderate negative effect or a large negative effect on their business.
- Making time for necessary employee training to minimize internal mistakes.
- Developing contingency plans to shield against external events that may impact operations. For example, a restaurant impacted by a natural disaster might be able to partner with another local restaurant, bar, or coffee shop to use their kitchen and sell to-go items.
Reputational Risks
Reputational risk can include a product safety recall, negative publicity, and negative reviews online from customers. Companies that suffer reputational damage can even see an immediate loss of revenue, as customers take their business elsewhere. Companies may experience additional impacts, including losing employees, suppliers, and other partners.
Ideas for managing reputational risks:
- Pay attention to what customers and employees say about the company both online and offline.
- Commit not only to providing a quality product or service, but also to ensuring that workers are trained to deliver excellent customer service and to resolve customer complaints, offer refunds, and issue apologies when necessary.
The Takeaway
Business owners face a variety of business risks, including financial, cybersecurity, operational, and reputational. However, they can take proactive measures to prevent or mitigate risk while continuing to seize opportunities for growth . To learn more about the benefits of risk management planning read, "5 Hidden Benefits of Risk Management."
Frequently Asked Questions
1. what are the main types of business risks.
There are several types of business risks: • Financial Risks • Cybersecurity Risks • Operational Risks • Reputational Risks
2. What are common examples of business risks?
• Financial risks can include cash flow problems, inability to meet financial obligations, or taking on too much debt. • Cybersecurity risks are risks associated with data breaches, hacks, or cyber-attacks. • Operational risks include supply chain disruptions, natural disasters, or IT failures. • Reputational risks can occur when a company's reputation is damaged by negative publicity, scandal, or other events.
3. How can you identify a business risk?
There are a few key ways to identify business risks:
• Reviewing financial statements and performance indicators: This can help you identify risks related to cash flow, profitability, or solvency. • Conducting a SWOT analysis: A SWOT analysis (Strengths, Weaknesses, Opportunities, Threats) can also be a helpful tool for identifying risks and brainstorming ways to mitigate them. • Identifying key dependencies: Key dependencies are things that your business relies on to function, and if they were to fail or be disrupted, it could have a serious impact on your business. • Carrying out root cause analysis: Conducting root cause analysis can help you to identify what underlying factors could lead to a problem or issue.
A version of this article was originally published September 01, 2022.
Photo: Getty Images
Trending Content
- Search Search Please fill out this field.
Identifying Risks
Physical risks, location risks, human risks, technology risks, strategic risks, making a risk assessment, insuring against risks, risk prevention, the bottom line.
- Business Essentials
Identifying and Managing Business Risks
:max_bytes(150000):strip_icc():format(webp)/522293_3816099810338_52357726_n1__marc_davis-5bfc2625c9e77c0058760671.jpg)
Running a business comes with many types of risk. Some of these potential hazards can destroy a business, while others can cause serious damage that is costly and time-consuming to repair. Despite the risks implicit in doing business, CEOs and risk management officers can anticipate and prepare, regardless of the size of their business.
Key Takeaways
- Some risks have the potential to destroy a business or at least cause serious damage that can be costly to repair.
- Organizations should identify which risks pose a threat to their operations.
- Potential threats include location hazards such as fires and storm damage, a l cohol and drug abuse among personnel, technology risks such as power outages, and strategic risks such as investment in research and development.
- A risk management consultant can recommend a strategy including staff training, safety checks, equipment and space maintenance, and necessary insurance policies.
If and when a risk becomes a reality, a well-prepared business can minimize the impact on earnings, lost time and productivity, and negative impact on customers. For startups and established businesses, the ability to identify risks is a key part of strategic business planning . Risks are identified through a number of ways. Strategies to identify these risks rely on comprehensively analyzing a company's specific business activities. Most organizations face preventable, strategic and external threats that can be managed through acceptance, transfer, reduction, or elimination.
A risk management consultant can help a business determine which risks should be covered by insurance.
Below are the main types of risks that companies face:
Building risks are the most common type of physical risk. Think fires or explosions. To manage building risk, and the risk to employees, it is important that organizations do the following:
- Make sure all employees know the exact street address of the building to give to a 911 operator in case of emergency.
- Make sure all employees know the location of all exits.
- Install fire alarms and smoke detectors.
- Install a sprinkler system to provide additional protection to the physical plant, equipment, documents and, of course, personnel.
- Inform all employees that in the event of emergency their personal safety takes priority over everything else. Employees should be instructed to leave the building and abandon all work-associated documents, equipment and/or products.
Hazardous material risk is present where spills or accidents are possible. The risk from hazardous materials can include:
- Toxic fumes
- Toxic dust or filings
- Poisonous liquids or waste
Fire department hazardous material units are prepared to handle these types of disasters. People who work with these materials, however, should be properly equipped and trained to handle them safely.
Organizations should create a plan to handle the immediate effects of these risks. Government agencies and local fire departments provide information to prevent these accidents. Such agencies can also provide advice on how to control them and minimize their damage if they occur.
Among the location hazards facing a business are nearby fires, storm damage, floods, hurricanes or tornados, earthquakes, and other natural disasters. Employees should be familiar with the streets leading in and out of the neighborhood on all sides of the place of business. Individuals should keep sufficient fuel in their vehicles to drive out of and away from the area. Liability or property and casualty insurance are often used to transfer the financial burden of location risks to a third-party or a business insurance company.
There are other business risks associated with location that are not directly related to hazards, such as city planning. For example, a gas station exists on a major road, and as a result of its location, it receives plenty of business. City planning can eventually restructure the area around the gas station. The city may close the road the gas station is on, build other infrastructure that would make the gas station inaccessible, or overall just not take the gas station into consideration with any redevelopment. This would leave the gas station with no traffic to serve.
Alcohol and drug abuse are major risks to personnel in the workforce. Employees suffering from alcohol or drug abuse should be urged to seek treatment, counseling, and rehabilitation if necessary. Some insurance policies may provide partial coverage for the cost of treatment.
Protection against embezzlement , theft and fraud may be difficult, but these are common crimes in the workplace. A system of double-signature requirements for checks, invoices, and payables verification can help prevent embezzlement and fraud. Stringent accounting procedures may discover embezzlement or fraud. A thorough background check before hiring personnel can uncover previous offenses in an applicant's past. While this may not be grounds for refusing to hire an applicant, it would help HR to avoid placing a new hire in a critical position where the employee is open to temptation.
Illness or injury among the workforce is a potential problem. To prevent loss of productivity, assign and train backup personnel to handle the work of critical employees when they are absent due to a health-related concern. Other human-related risks under public attention could be associated with their behaviors and values. Misbehavior of management related to bias, racism, sexism, harassment, corruption, discrimination, pollutive actions, and carelessness about the environment are all actions that represent risk for the companies where these managers work.
A power outage is perhaps the most common technology risk. Auxiliary gas-driven power generators are a reliable back-up system to provide electricity for lighting and other functions. Manufacturing plants use several large auxiliary generators to keep a factory operational until utility power is restored.
Computers may be kept up and running with high-performance back-up batteries. Power surges may occur during a lightning storm (or randomly), so organizations should furnish critical business systems with surge-protection devices to avoid the loss of documents and the destruction of equipment.
Cloud storage is another source of risks nowadays. The process involves backing up data with Amazon Web Services, for example, using Azure, IBM, and Oracle, for instance. This is a huge undertaking that should be considered given the reliance on cloud-based data to run most businesses now. It is important to establish both offline and online data backup systems to protect critical documents.
Although telephone and communications failure are relatively uncommon, risk managers may consider providing emergency-use company cell phones to personnel whose use of the phone or internet is critical to their business.
Strategy risks are not altogether undesirable. Financial institutions such as banks or credit unions take on strategy risk when lending to consumers, while pharmaceutical companies are exposed to strategy risk through research and development for a new drug. Each of these strategy-related risks is inherent in an organization's business objectives. When structured efficiently, the acceptance of strategy risks can create highly profitable operations.
Companies exposed to substantial strategy risk can mitigate the potential for negative consequences by creating and maintaining infrastructures that support high-risk projects. A system established to control the financial hardship that occurs when a risky venture fails often includes diversification of current projects, healthy cash flow, or the ability to finance new projects in an affordable way, and a comprehensive process to review and analyze potential ventures based on future return on investment .
After the risks have been identified , they must be prioritized in accordance with an assessment of their probability. The first step is to establish a probability scale for the purposes of risk assessment .
For example, risks may:
- Be very likely to occur
- Have some chance of occurring
- Have a small chance of occurring
- Have very little chance of occurring
Other risks must be prioritized and managed in accordance with their likelihood of occurring. Actuarial tables —statistical analysis of the probability of any risk occurring and the potential financial damage ensuing from the occurrence of those risks—may be accessed online and can provide guidance in prioritizing risk.
Insurance is a principle safeguard in managing risk, and many risks are insurable. Fire insurance is a necessity for any business that occupies a physical space, whether owned outright or rented, and should be a top priority. Product liability insurance, as an obvious example, is not necessary for a service business.
Some risks are an inarguably high priority, for example, the risk of fraud or embezzlement where employees handle money or perform accounting duties in accounts payable and receivable. Specialized insurance companies will underwrite a cash bond to provide financial coverage in the event of embezzlement, theft or fraud.
When insuring against potential risks, never assume a best-case scenario. Even if employees have worked for years with no problems and their service has been exemplary, insurance against employee error may be a necessity. The extent of insurance coverage against injury will depend on the nature of your business. A heavy manufacturing plant will, of course, require more extensive coverage for employees. Product liability insurance is also a necessity in this context.
If a business relies heavily on computerized data—customer lists and accounting data, for example—exterior backup and insurance coverage is necessary. Finally, hiring a risk management consultant may be a prudent step in the prevention and management of risks.
The best risk insurance is prevention. Preventing the many risks from occurring in your business is best achieved through employee training, background checks, safety checks, equipment maintenance and maintenance of the physical premises. A single, accountable staff member with managerial authority should be appointed to handle risk management responsibilities. A risk management committee may also be formed with members assigned specific tasks with a requirement to report to the risk manager.
The risk manager, in conjunction with a committee, should formulate plans for emergency situations such as:
- Hazardous materials accidents or the occurrence of other emergencies
Employees must know what to do and where to exit the building or office space in an emergency. A plan for the safety inspection of the physical premises and equipment should be developed and implemented regularly including the training and education of personnel when necessary. A periodic, stringent review of all potential risks should be conducted. Any problems should be immediately addressed. Insurance coverage should also be periodically reviewed and upgraded or downgraded as needed.
Prevention is the best insurance against risk. Employee training, background checks, safety checks, equipment maintenance, and maintenance of physical premises are all crucial risk management strategies for any business.
While business risks abound and their consequences can be destructive, there are ways and means to ensure against them, to prevent them, and to minimize their damage, if and when they occur. Finally, hiring a risk management consultant may be a worthwhile step in the prevention and management of risks.
:max_bytes(150000):strip_icc():format(webp)/strategic-management-ADD-Source-7c12087694c9443a99743b612dd1c5d5.jpg)
- Terms of Service
- Editorial Policy
- Privacy Policy
How to Highlight Risks in Your Business Plan

Tallat Mahmood
5 min. read
Updated October 25, 2023

One of the areas constantly dismissed by business owners in their business plan is an articulation of the risks in the business.
This either suggests you don’t believe there to be any risks in your business (not true), or are intentionally avoiding disclosing them.
Either way, it is not the best start to have with a potential funding partner. In fact, by dismissing the risks in your business, you actually make the job of a lender or investor that much more difficult.
Why a funder needs to understand your business’s risks:
Funding businesses is all about risk and reward.
Whether it’s a lender or an investor, their key concern will be trying to balance the risks inherent in your business, versus the likelihood of a reward, typically increasing business value. An imbalance occurs when entrepreneurs talk extensively about the opportunities inherent in their business, but ignore the risks.
The fact is, all funders understand that risks exist in every business. This is just a fact of running a business. There are risks that exist with your products, customers, suppliers, and your team. From a funder’s perspective, it is important to understand the nature and size of risks that exist.
- There are two main reasons why funders want to understand business risks:
Firstly, they want to understand whether or not the key risks in your business are so fundamental to the investment proposition that it would prevent them from funding you.
Some businesses are not at the right stage to receive external funding and placate funder concerns. These businesses are best off dealing with key risk factors prior to seeking funding.
The second reason why lenders and investors want to understand the risk in your business is so that they can structure a funding package that works best overall, despite the risk.
In my experience, this is an opportunity that many business owners are wasting, as they are not giving funders an opportunity to structure deals suitable for them.
Here’s an example:
Assume your business is seeking equity funding, but has a key management role that needs to be filled. This could be a key business risk for a funder.
Highlighting this risk shows that you are aware of the appointment need, and are putting plans in place to help with this key recruit. An investor may reasonably decide to proceed with funding, but the funding will be released in stages. Some will be released immediately and the remainder will be after the key position has been filled.
The benefit of highlighting your risks is that it demonstrates to investors that you understand the danger the risks pose to your company, and are aware that it needs to be dealt with. This allows for a frank discussion to take place, which is more difficult to do if you don’t acknowledge this as a problem in the first place.
Ultimately, the starting point for most funders is that they want to invest in you, and want to validate their initial interest in you.
Highlighting your business risks will allow the funder to get to the nub of the problem, and give them a better idea of how they may structure their investment in order to make it work for both parties. If they are unsure of the risks or cannot get clear explanations from the team, it is unlikely they will be forthcoming when it comes to finding ways to make a potential deal work.
Brought to you by
Create a professional business plan
Using ai and step-by-step instructions.
Secure funding
Validate ideas
Build a strategy
- The right way to address business risks:
The main reason many business owners don’t talk about business risks with potential funders is because they don’t want to highlight the weaknesses in their business.
This is a fair concern to have. However, there is a right way to address business risk with funders, without turning lenders and investors off.
The solution is to focus on how you mitigate the risks.
In other words, what are the steps you are taking in your business as a direct reaction to the risks that you have identified? This is very powerful in easing funder fears, and in positioning you as someone who has a handle on their business.
For example, if a business risk you had identified was a high level of customer concentration, then a suitable mitigation plan would be to market your products or services targeting new clients, as opposed to focusing all efforts on one client.
Having net profit margins that are lower than average for your market would raise eyebrows and be considered a risk. In this instance, you could demonstrate to funders the steps you are putting in place over a period of time to help increase those margins to at least market norms for your niche.
The process of highlighting risks—and, more importantly, outlining key mitigating actions—not only demonstrates honesty, but also a leadership quality in solving the problems in your business. Lenders and investors want to see both traits.
- The impact on your credibility:
Any lender or investor backs the leadership team of a business first, and the business itself second.
This is because they realize that it is you, the management team, who will ultimately deliver value and grow the business for the benefit for all. As such, it is imperative that they have the right impression about you.
The consequence of highlighting business risks in your business plan with mitigations is that it provides funders a real insight into you as a business leader. It demonstrates that not only do you have an understanding of their need to understand risk in your business, but you also appreciate that minimizing that risk is your job.
This will have a massive impact on your credibility as a business owner and management team. This impact is more acute when compared to the hundreds of businesses they will meet that omit discussing the risks in their business.
The fact is, funders have seen enough businesses and business plans in all sectors to instinctively know what risks to expect. It’s just more telling if they hear it from you first.
- What does this mean for you going forward?
Funders rely on you to deliver on your inherent promise to add value to your business for all stakeholders. The weight of this promise becomes much stronger if they can believe in the character of the team, and that comes from your credibility.
A business plan that discusses business risks and mitigations is a much more complete plan, and will increase your chances of securing funding.
Not only that, but highlighting the risks your business faces also has a long-term impact on your character and credibility as a business leader.
Tallat Mahmood is founder of The Smart Business Plan Academy, his flagship online course on building powerful business plans for small and medium-sized businesses to help them grow and raise capital. Tallat has worked for over 10 years as a small and medium-sized business advisor and investor, and in this period has helped dozens of businesses raise hundreds of millions of dollars for growth. He has also worked as an investor and sat on boards of companies.

Table of Contents
- Why a funder needs to understand your business’s risks:
Related Articles

1 Min. Read
How to Calculate Return on Investment (ROI)

2 Min. Read
How to Use These Common Business Ratios

7 Min. Read
7 Financial Terms Small Business Owners Need to Know

8 Min. Read
How to Forecast Personnel Costs in 3 Steps
The LivePlan Newsletter
Become a smarter, more strategic entrepreneur.
Your first monthly newsetter will be delivered soon..
Unsubscribe anytime. Privacy policy .
The quickest way to turn a business idea into a business plan
Fill-in-the-blanks and automatic financials make it easy.
No thanks, I prefer writing 40-page documents.
Discover the world’s #1 plan building software

Uncovering Hidden Risks: A Comprehensive Guide to Business Plan Risk Analysis
A modern business plan that will lead your business on the road to success must have another critical element. That element is a part where you will need to cover possible risks related to your small business. So, you need to focus on managing risk and use risk management processes if you want to succeed as an entrepreneur.
How can you manage risks?
You can always plan and predict future things in a certain way that will happen, but your impact is not always in your hands. There are many external factors when it comes to the business world. They will always influence the realization of your plans. Not only the realization but also the results you will achieve in implementing the specific plan. Because of that, you need to look at these factors through the prism of the risk if you want to implement an appropriate management process while implementing your business plan.
By conducting a thorough risk analysis, you can manage risks by identifying potential threats and uncertainties that could impact your business. From market fluctuations and regulatory changes to competitive pressures and technological disruptions, no risk will go unnoticed. With these insights, you can develop contingency plans and implement risk mitigation strategies to safeguard your business’s interests.
This guide will provide practical tips and real-life examples to illustrate the importance of proper risk analysis. Whether you’re a startup founder preparing a business plan or a seasoned entrepreneur looking to reassess your risk management approach, this guide will equip you with the knowledge and tools to navigate the complex landscape of business risks.
Why is Risk Analysis Important for Business Planning?
Risk analysis is essential to business planning as it allows you to proactively identify and assess potential risks that could impact your business objectives. When you conduct a comprehensive risk analysis, you can gain a deeper understanding of the threats your business may face and can take proactive measures to mitigate them.
One of the key benefits of risk analysis is that it enables you to prioritize risks based on their potential impact and likelihood of occurrence . This helps you allocate resources effectively and develop contingency plans that address the most critical risks.
Additionally, risk analysis allows you to identify opportunities that may arise from certain risks , enabling you to capitalize on them and gain a competitive advantage.
It is important to adopt a systematic approach to effectively analyze risks in your business plan. This involves identifying risks across various market, operational, financial, and legal areas. By considering risks from multiple perspectives, you can develop a holistic understanding of your business’s potential challenges.
What is a Risk for Your Small Business?
In dictionaries, the risk is usually defined as:
The possibility of dangerous or bad consequences becomes true .
When it comes to businesses, entrepreneurs , or in this case, the business planning process, it is possible that some aspects of the business plan will not be implemented as planned. Such a situation could have dangerous or harmful consequences for your small business.
It is simple. If you don’t implement something you have in your business plan, there will be some negative consequences for your small business.
Here is how you can write the business plan in 30 steps .
Types of Risks in Business Planning
When conducting a business risk assessment for your business plan, it is essential to consider various types of risks that could impact your venture. Here are some common types of risks to be aware of:
1. Market risks
These risks arise from fluctuations in the market, including changes in consumer preferences, economic conditions, and industry trends. Market risks can impact your business’s demand, pricing, and market share.
2. Operational risk
Operational risk is associated with internal processes, systems, and human resources. These risks include equipment failure, supply chain disruptions, employee errors, and regulatory compliance issues.
3. Financial risks
Financial risks pertain to managing financial resources and include factors such as cash flow volatility, debt levels, currency fluctuations, and interest rate changes.
4. Legal and regulatory risks
Legal and regulatory risks arise from changes in laws, regulations, and compliance requirements. Failure to comply with legal and regulatory obligations can result in penalties, lawsuits, and reputational damage.
5. Technological risks
Technological risks arise from rapid technological advancements and the potential disruptions they can cause your business. These risks include cybersecurity threats, data breaches, and outdated technology infrastructure.
Basic Characteristics of Risk
Before you start with the development of your small business risk management process, you will need to know and consider the essential characteristics of the possible risk for your company.
What are the basic characteristics of a possible risk?
The risk for your company is partially unknown.
Your entrepreneurial work will be too easy if it is easy to predict possible risks for your company. The biggest problem is that the risk is partially unknown. Here we are talking about the future, and we want to prepare for that future. So, the risk is partially unknown because it will possibly appear in the future, not now.
The risk to your business will change over time.
Because your businesses operate in a highly dynamic environment, you cannot expect it to be something like the default. You cannot expect the risk to always exist in the same shape, form, or consequence for your company.
You can predict the risk.
It is something that, if we want, we can predict through a systematic process . You can easily predict the risk if you install an appropriate risk management process in your small business.
The risk can and should be managed.
You can always focus your resources on eliminating or reducing risk in the areas expected to appear.

Risk Management Process You Should Implement
The risk management process cannot be seen as static in your company. Instead of that, it must be seen as an interactive process in which information will continuously be updated and analyzed. You and your small business members will act on them, and you will review all risk elements in a specified period.
Adopting a systematic approach to identifying and assessing risks in your business plan is crucial. Here are some steps to consider:
1. Risk Identification
First, you must identify risk areas . Ask and respond to the following questions:
- What are my company’s most significant risks?
- What are the risk types I will need to follow?
In business, identifying risk areas is the process of pinpointing potential threats or hazards that could negatively impact your business’s ability to conduct operations, achieve business objectives, or fulfill strategic goals.
Just as meteorologists use data to predict potential storms and help us prepare, you can use risk identification to foresee possible challenges and create plans to deal with them.
Risk can arise from various sources, such as financial uncertainty, legal liabilities, strategic management errors, accidents, natural disasters, and even pandemic situations. Natural disasters can not be predicted or avoided, but you can prepare if they appear.
For example, a retail business might identify risks like fluctuating market trends, supply chain disruptions, cybersecurity threats, or changes in consumer behavior. As you can see, the main risk areas are related to types of risk: market, financial, operational, legal and regulatory, and technological risks.
You can also use business model elements to start with something concrete:
- Value proposition,
- Customers ,
- Customers relationships ,
- Distribution channels,
- Key resources and
- Key partners.
It is not necessarily that there will be risk in all areas and that the risk will be with the same intensity for all areas. So, based on your business environment, the industry in which your business operates, and the business model, you will need to determine in which of these areas there is a possible risk.
Also, you must stay informed about external factors impacting your business, such as industry trends, economic conditions, and regulatory changes. This will help you identify emerging risks and adapt your risk management strategies accordingly.
The idea for this step is to create a table where you will have identified potential risks in each important area of your business.
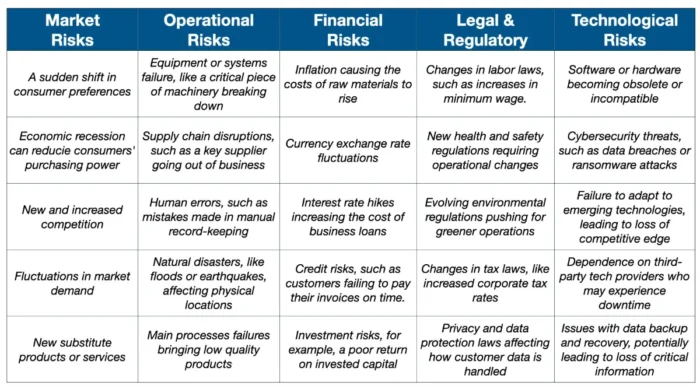
2. Risk Profiling
Conduct a detailed analysis of each identified risk, including its potential impact on your business objectives and the likelihood of occurrence. This will help you develop a comprehensive understanding of the risks you face.
Qualitative Risk Analysis
The qualitative risk analysis process involves assessing and prioritizing risks based on ranking or scoring systems to classify risks into low, medium, or high categories. For this analysis, you can use customer surveys or interviews.
Qualitative risk analysis is quick, straightforward, and doesn’t require specialized statistical knowledge to conduct a business risk assessment. The main negative side is its subjectivity, as it relies heavily on thinking about something or expert judgment.
This method is best suited for initial risk assessments or when there is insufficient quantitative analysis data .
For example, if we consider the previously identified risk of a sudden shift in consumer preferences, a qualitative analysis might rate its likelihood as 7 out of 10 and its impact as 8 out of 10, placing it in the high-priority quadrant of our risk matrix. But, qualitative analysis can also use surveys and interviews where you can ask open questions and use the qualitative research process to make this scaling. This is much better because you want to lower the subjectivism level when doing business risk assessment.
Quantitative Risk Analysis
On the other side, the quantitative risk analysis method involves numerical and statistical techniques to estimate the probability and potential impact of risks. It provides more objective and detailed information about risks.
Quantitative risk analysis can provide specific, data-driven insights, making it easier to make informed decisions and allocate resources effectively. The negative side of this method is that it can be time-consuming, complex, and requires sufficient data.
You can use this approachfor more complex projects or when you need precise data to inform decisions, especially after a qualitative analysis has identified high-priority risks.
For example , for the risk of currency exchange rate fluctuations, a quantitative analysis might involve analyzing historical exchange rate data to calculate the probability of a significant fluctuation and then using your financial data to estimate the potential monetary impact.
Both methods play crucial roles in effectively managing risks. Qualitative risk analysis helps to identify and prioritize risks quickly, while quantitative analysis provides detailed insights for informed decision-making.
3. Business Risk Assessment Matrix
Once you have identified potential risks and analyzed their likelihood and potential impact, you can create a business risk assessment matrix to evaluate each risk’s likelihood and impact. This matrix will help you prioritize risks and allocate resources accordingly.
A business risk assessment matrix, sometimes called a probability and impact matrix, is a tool you can use to assess and prioritize different types of risks based on their likelihood (probability) and potential damage (impact). Here’s a step-by-step process to create one:
- Step 1: Begin by listing out your risks . For our example, let’s consider four of the risks we identified earlier: a sudden shift in consumer preferences (Market Risk), currency exchange rate fluctuations (Financial Risk), an increase in the minimum wage (Legal), and cybersecurity threats (Technological Risk).
- Step 2: Determine the likelihood of each risk occurring . In the process of risk profiling, we’ve determined that a sudden shift in consumer preferences is highly likely, currency exchange rate fluctuations are moderately likely, an increase in the minimum wage, and cybersecurity threats are less likely but still possible.
- Step 3: Assess the potential impact of each risk on your business if it were to occur . In our example, we might find that a sudden shift in consumer preferences could have a high impact, currency exchange rate fluctuations a moderate impact, an increase in minimum wage minor impact, and cybersecurity threats a high impact.
- Step 4: Plot these risks on your risk matrix . The vertical axis represents the likelihood (high to low), and the horizontal axis represents the consequences (high to low).
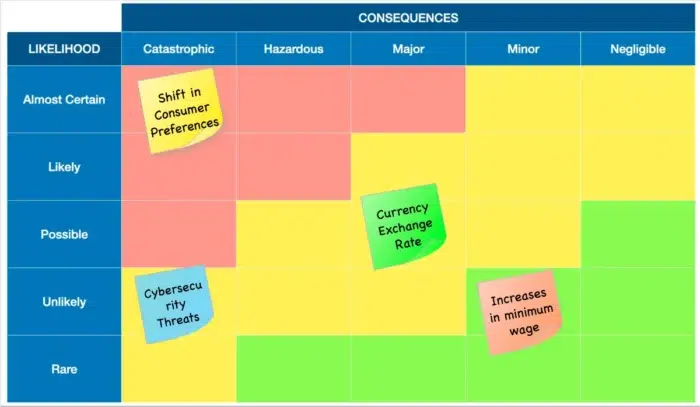
By visualizing these risks in a risk assessment matrix format, you can more easily identify which risks require immediate attention and which ones might need long-term strategies.
4. Develop Risk Indicators for Each Risk You Have Identified
The question is, how will you measure the business risks for your company?
Risk indicators are metrics used to measure and predict potential threats to your business. Simply, a risk indicator is a measure that should tell you whether the risk appears or not in a particular area you have defined previously. They act like a business’s early warning system. When these indicators change, it’s a signal that the risk level may be increasing.
For example, for distribution channels, an indicator can be a delay in delivery for a minimum of three days. This indicator will tell you something is wrong with that channel, and you must respond appropriately.
Now, let’s consider some risk indicators for the risks we have already identified and analyzed:
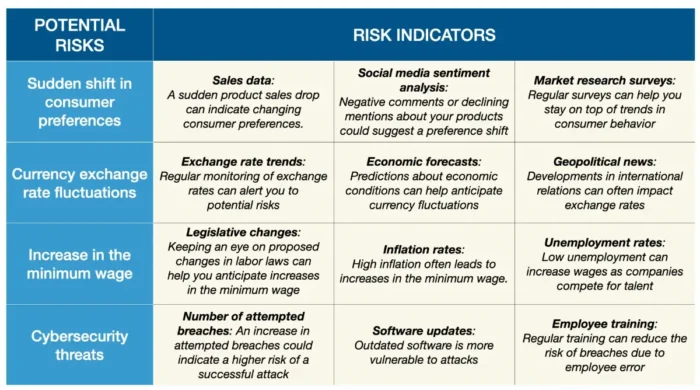
If you conduct all the steps until now, you can have a similar table with risk indicators in your business plan. You should monitor these indicators regularly, and if you notice a significant change, such as a drop in sales or an increase in attempted breaches, it’s time to investigate and take some action steps. This might involve updating your product line, hedging against currency risk, budgeting for higher wages, or improving your cybersecurity measures.
Remember, risk indicators can’t predict the future with certainty. But they can give you valuable insights that can help you prepare for potential threats.
5. Define Possible Action Steps
The question is, what can you do regarding the risk if the risk indicator tells you that there is a potential risk?
Once the risk has appeared and is located, it is time to take concrete action steps. The goals of this step are not only to reduce or eliminate the impact of the risk for your company but also to prevent them in the future and reduce or eliminate their influence on the business operations or the execution of your business plan.
For example, for distribution channels with delivery delayed more than three days, possible activities can be the following:
- Apologizing to the customers for the delay,
- Determining the reasons for the delay,
- Analysis of the reasons,
- Removing the reasons,
- Consideration of alternative distribution channels, etc.
In this part of the business plan for each risk area and indicator, try to standardize all possible actions. You can not expect that they will be final. But, you can cover some basic guidelines that must be implemented if the risk appears. Here is an example of how this part will look in your business plan related to risks we have already identified through the risk assessment process.

6. Monitoring
Because this risk management process is dynamic , you must apply the monitoring process. In such a way, you can ensure the elimination of a specific kind of risk in the future, and you will allocate your resources to new possible risks.
After implementing the actions, you need to ask yourself the following questions:
- Are the actions taken regarding the risk the proper measures?
- Can you improve something regarding the risk management process? Is there a need for new risk indicators?
Techniques and Tools for Business Plan Risk Assessment
Various risk analysis methods, techniques, and tools are available to conduct an effective risk analysis for your business plan. Here are some commonly used ones:
1. SWOT analysis
A SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis can help you identify internal strengths and weaknesses and external opportunities and threats. This analysis provides valuable insights into possible business risks and opportunities.
2. PESTEL analysis
A PESTEL (Political, Economic, Sociocultural, Technological, Environmental, Legal) analysis assesses the external factors that could impact your business. This analysis will help you identify risks and opportunities arising from these factors.
3. Scenario analysis
Consider different scenarios that could impact your business, such as best-case, worst-case, and most likely scenarios, as a part of your risk assessment process. You can anticipate potential risks and develop appropriate response strategies by analyzing these scenarios.
4. Monte Carlo simulation
Monte Carlo simulation uses random sampling and probability distributions to model various scenarios and assess their potential impact on your business. This technique provides you with a more accurate understanding of risk exposure.
5. Risk register
A risk register is a risk analysis tool that helps you record and track identified risks and their relevant details, such as impact, likelihood, mitigation strategies, and responsible parties. This tool ensures that risks are appropriately managed and monitored.
6. Business Impact Analysis (BIA)
Business impact analysis helps you understand the potential effects of various disruptions on your business operations and objectives. It’s about identifying what could go wrong and understanding how it could impact your bottom line. So, you can conduct business impact analysis as a part of your risk assessment inside your business plan.
7. Failure Mode and Effects Analysis (FMEA)
Using FMEA in your risk assessment process, you can proactively address potential problems, ensuring your business operations run as smoothly as you planned. It’s all about preparing for the worst while striving for the best.
8. Risk-Benefit Analysis (RBA)
The risk-benefit analysis allows you to make informed decisions, balancing the potential for gain against the potential for loss. It helps you choose the best path, even when the way forward isn’t entirely clear. This tool is a systematic approach to understanding the specific business risk and benefits associated with a decision, process, or project.
9. Cost-Benefit Analysis
By conducting a cost-benefit analysis as a part of your risk assessments, you can make data-driven decisions that consider both the possible risks (costs) and rewards (benefits). This approach provides a clear picture of the potential return on investment, enabling more effective and confident decision-making.
These techniques and tools allow you to conduct a comprehensive risk analysis for your business plan.
Mitigating and Managing Risks in a Business Plan
Identifying risks in your business plan is only the first step. To ensure the success of your venture, it is crucial to develop effective risk mitigation and management strategies. Here are some critical steps to consider:
- Risk avoidance : Some risks may be too high to justify taking. In such cases, consider avoiding these risks altogether by adjusting your business plan or exploring alternative strategies.
- Risk transfer : Transferring risks to third parties, such as insurance companies or outsourcing partners, can help mitigate their impact on your business. Evaluate opportunities for risk transfer and consider appropriate insurance coverage.
- Risk reduction : Implement measures to reduce the likelihood and impact of identified risks. This may involve improving internal processes, implementing safety protocols, or diversifying your supplier base .
- Risk acceptance : Some risks may be unavoidable or negatively impact your business. In such cases, accepting the risks and developing contingency plans can help minimize their impact.
In conclusion, a comprehensive risk analysis is essential for identifying, assessing, and managing different types of risk that could impact your success.
Conducting a thorough risk analysis can safeguard your business’s interests, capitalize on opportunities, and increase your chances of long-term success.

Related Posts

How to Write a Business Plan in 36 Steps

Risk Tolerance in Entrepreneurship: A Guide to Successful Business

Business Goals Questions to Develop SMART Goals

Risk Management Guide: Everything You Need to Know About Business Risk
Start typing and press enter to search.

- Share on Twitter
- Share on LinkedIn
- Share on Facebook
- Share on Pinterest
- Share through Email
How To Create A Risk Management Plan + Template & Examples
Emily has been working in project management for over 13 years. In this time, she has worked using a variety of project management methodologies and has been a strategic project manager, facilitator, and Scrum master. She is also an avid coach and trainer, who wants to ensure the development of the next generation of project professionals through training, knowledge sharing and team building.
Sarah is a project manager and strategy consultant with 15 years of experience leading cross-functional teams to execute complex multi-million dollar projects. She excels at diagnosing, prioritizing, and solving organizational challenges and cultivating strong relationships to improve how teams do business. Sarah is passionate about productivity, leadership, building community, and her home state of New Jersey.
Dramatically reduce your chances of project failure with a risk management plan: learn how to create one for your projects, get some examples, and download our template!

A clear and detailed risk management plan helps you assess the impact of project risks and understand the potential outcomes of your decisions. It can be a useful tool to support decision making in the face of uncertainty.
However, I have seen projects fail because stakeholders did not take the risk management plan seriously or because the project failed to implement a risk management strategy.
Read on to learn how you can avoid these mistakes for your projects.
What Is A Risk Management Plan?
A risk management plan, or RMP, is a document describing how your project team will monitor and respond to unexpected or uncertain events that could impact the project.
The risk management plan:
- analyzes the potential risks that exist in your organization or project
- identifies how you will respond to those risks if they arise
- assigns a responsible person to monitor each risk and take action, if needed.
Team members and stakeholders should collaborate to create a project risk management plan after starting to develop a project management plan but before the project begins.
What’s Covered In A Risk Management Plan?
The fidelity of your risk management plan will vary depending on the nature of your project and the standard operating procedures that your organization uses.
A project risk management plan seeks to answer:
- What is this project, and why does it matter?
- Why is risk management important for the project’s success?
- What will the team do to identify, log, assess, and monitor risks throughout the project?
- What categories of risk will we manage?
- What methodology will be used for risk identification and to evaluate risk severity?
- What is expected of the people who own the risks?
- How much risk is too much risk?
- What are the risks, and what are we going to do about them?
Depending on the project, this document could be hundreds of pages—or it could be less than a dozen. So how do you decide how much detail to provide? Here are two illustrative examples (but by no means are they the only ways to do it!).
PS. If you’re looking for additional information, we also did a workshop on managing risk that’s available for DPM members .
2 Types Of Risk Management Plans
In this section, we’ll cover 2 common types of risk management plans—a RAID log and a risk matrix.
#1: Simpler Version—Lightweight RAID Log
In its most minimal form, a risk management plan could be a handful of pages describing:
- how and when to assess risk
- the roles and responsibilities for risk owners
- at what point the project risk should trigger an escalation.

Instead of a formal risk register designed to calculate risk severity, a lightweight risk management approach may simply involve maintaining a risk list in your weekly status report .
This list (also known as a RAID log) tracks risks, assumptions, issues, and dependencies so that the project team and sponsor can review and further discuss.
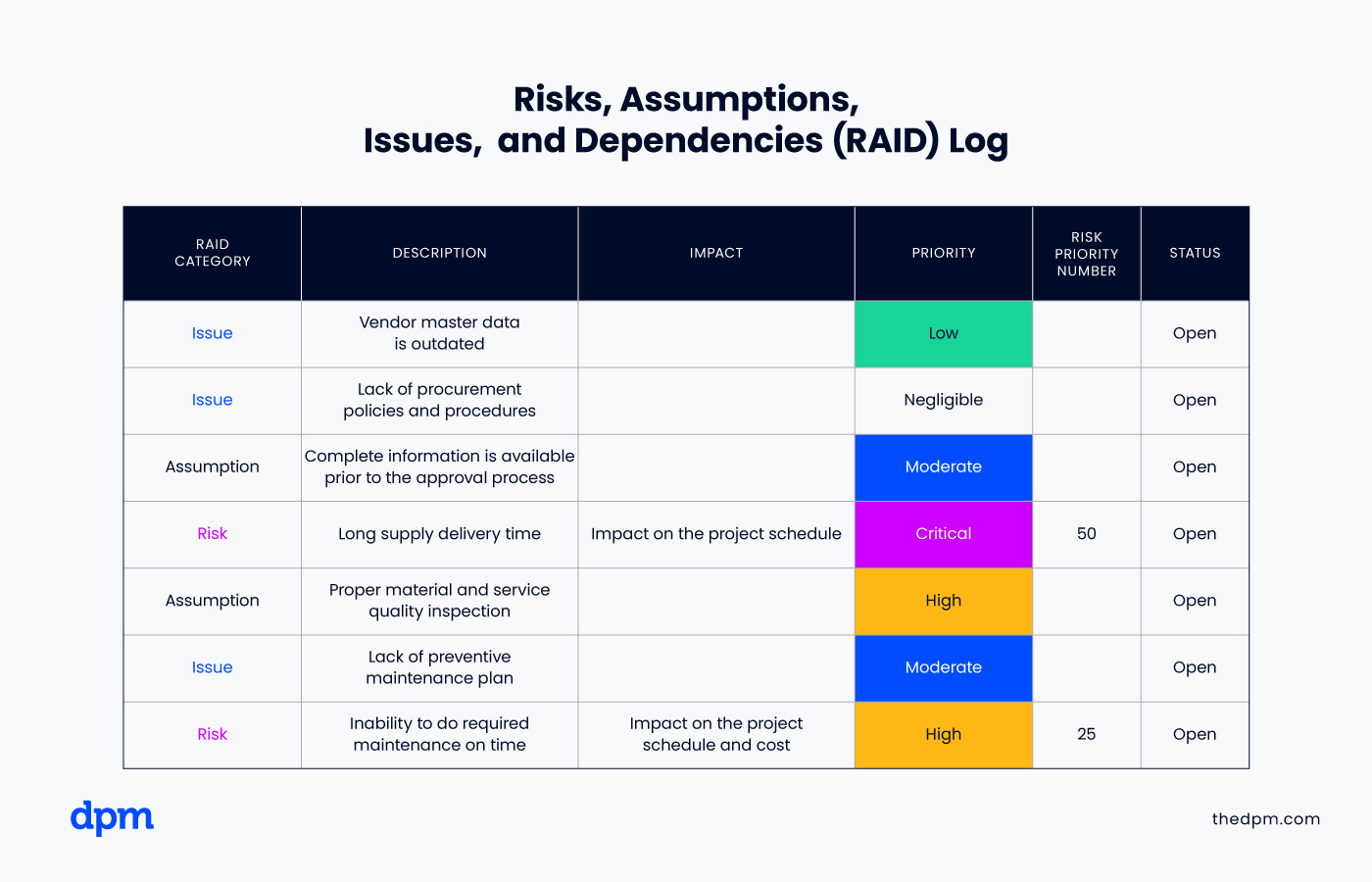
When to use it : this approach could be useful for a small non-technical project being executed by a team of 3-4 people in an organization that does not have a standard approach to risk management.

Sign up to get weekly insights, tips, and other helpful content from digital project management experts.
- Your email *
- Yes, I want to sign up to receive regular emails filled with tips, expert insights, and more to build my PM practice.
- By submitting you agree to receive occasional emails and acknowledge our Privacy Policy . You can unsubscribe at any time. Protected by reCAPTCHA; Google Privacy Policy and Terms of Service apply.
- Name This field is for validation purposes and should be left unchanged.
#2: Complex Version—Risk Matrix
When an organization already has a culture of risk management, there may be a template to follow that demands a high level of detail. These details may include a full description of the methodology that the organization will follow to perform qualitative and quantitative risk analysis, along with an impact matrix.
An impact matrix, or risk assessment matrix, shows the relationship between risk factors in calculating risk severity. Risks that are high-probability and high-impact are the most severe.
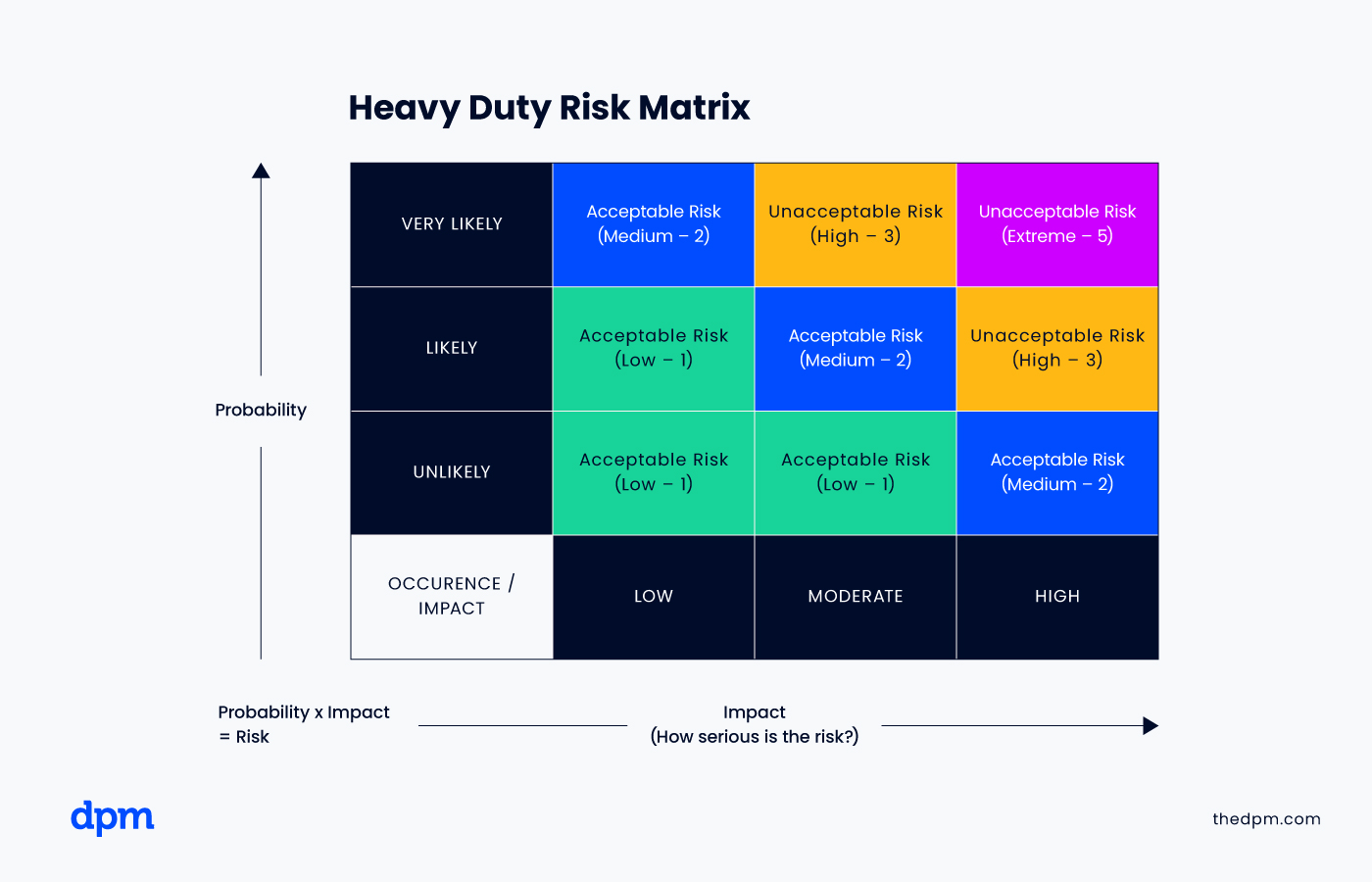
An organization may design its risk register template to prioritize and assign a numerical severity score to measure the level of risk.
Additionally, you may need to create a risk breakdown structure to decompose higher-level risk categories into smaller, more specific risk subcategories
When to use it : making a detailed risk management plan isn’t about creating complexity for complexity’s sake—you and your team will be glad to have this level of detail on a large enterprise project that involves larger teams, multiple stakeholders, and high stakes that could have a significant impact on the business.
The concept of enterprise project management has evolved to include digital tools and methodologies.
In terms of tooling, there are some great options available for managing risk on your project. Many organizations favor spreadsheets as part of an enterprise business software bundle, but there are also some providers that support risk management planning specifically.
Two examples of risk management software are Wrike and monday.com . These tools integrate the entire risk management process with the wider project management plan.
The most important consideration is not the tool used, but rather the discussions you’ll have with your team and your project sponsor about how to navigate risks to increase the likelihood of project success.
How To Make A Risk Management Plan
Below is a step-by-step guide to developing your own version of a risk management plan. Keep in mind that the nature of these steps may vary depending on the type of project involved, so don’t be afraid to tailor these steps to meet project and organizational needs.
The first 2 steps in the process are preparing supporting documentation and setting the context.

Next, decide how you want to identify & assess risks, and continuously identify those risks.
The next steps in the risk management process include assigning risk owners, populating your risk register, and then publishing it.

Make sure to monitor and assess risks throughout the project, and once the project is over, archive the risk management plan in a way that it can be reused for future projects.
1. Prepare supporting documentation
You’ll want to review existing project management documentation to help you craft your risk management plan. This documentation includes:
- Project Charter: among other things, this document establishes the project objectives , the project sponsor, and you as the project manager. Frankly, it gives you the right to create a project management plan and then a risk management plan within that. If formal project charters aren’t used at your organization, you should at least have this documented in an email or a less formal brief.
- Project Management Plan: not to be confused with the project strategy , this document outlines how you’ll manage, monitor, and control your project, including what methodology to use, how to report progress, how to escalate issues, etc. Your risk management plan should act as a subcomponent of the project management plan.
- Stakeholder Register: it’s good to have a solid idea of who the project stakeholders are before assessing risk. Each of these stakeholder groups presents a different set of risks when it comes to people, processes, and technology. You can also invite stakeholders to identify risks throughout the project and even nominate them as risk owners!
2. Set the context
Once you have your supporting documentation available, use it to frame up the discussion around your risk management plan. Specifically, take the project description and objectives from the project charter and use them to outline the business value of the project and the negative impacts that would result should the project fail .
The introduction to your risk management plan should explain the intent of this document and its relationship to the overarching project management plan. Use this context to drive a conversation about risk management with your team and your project sponsor.
3. Decide with your team how to identify and assess risks
Different methodologies are appropriate for different types of projects. The methods you choose also need to be sustainable for the team to perform throughout the project.
The key here is to have the right discussions and gather input to build consensus with your team and your stakeholders early in the project life cycle. Use these discussions to agree on risk categories, risk response plans, and ways to calculate risk severity.

4. Continuously identify risks
Once you’ve decided on the methodology to use, now the real fun begins—thinking about the things that could go astray during your project!
A great way to do this is to hold a risk workshop—a group session involving your team, key stakeholders, project sponsor, and subject matter experts to identify, evaluate, and plan responses to risks.
In the example below, I have used a simple overview from a sample project. During the workshop, you’d discuss everything in columns E-R and make sure that you have clear, SMART outcomes to put in each of the boxes. (SMART stands for specific, measurable, action-oriented, realistic, and timebound.)
I like to keep a copy of the risk register on my desk during the workshop to make sure that each column is discussed and populated appropriately. After the workshop, add any supporting details to finalize the document.
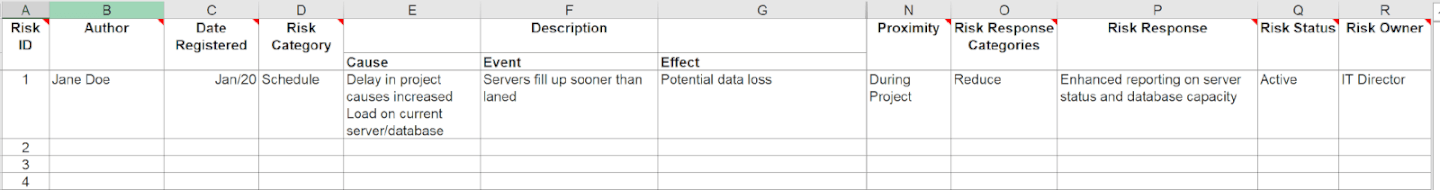
The project manager’s role during a risk workshop is to facilitate the meeting effectively. This involves brainstorming with stakeholders to evaluate both known risks and possible risks that may not have been considered. It could look something like this:
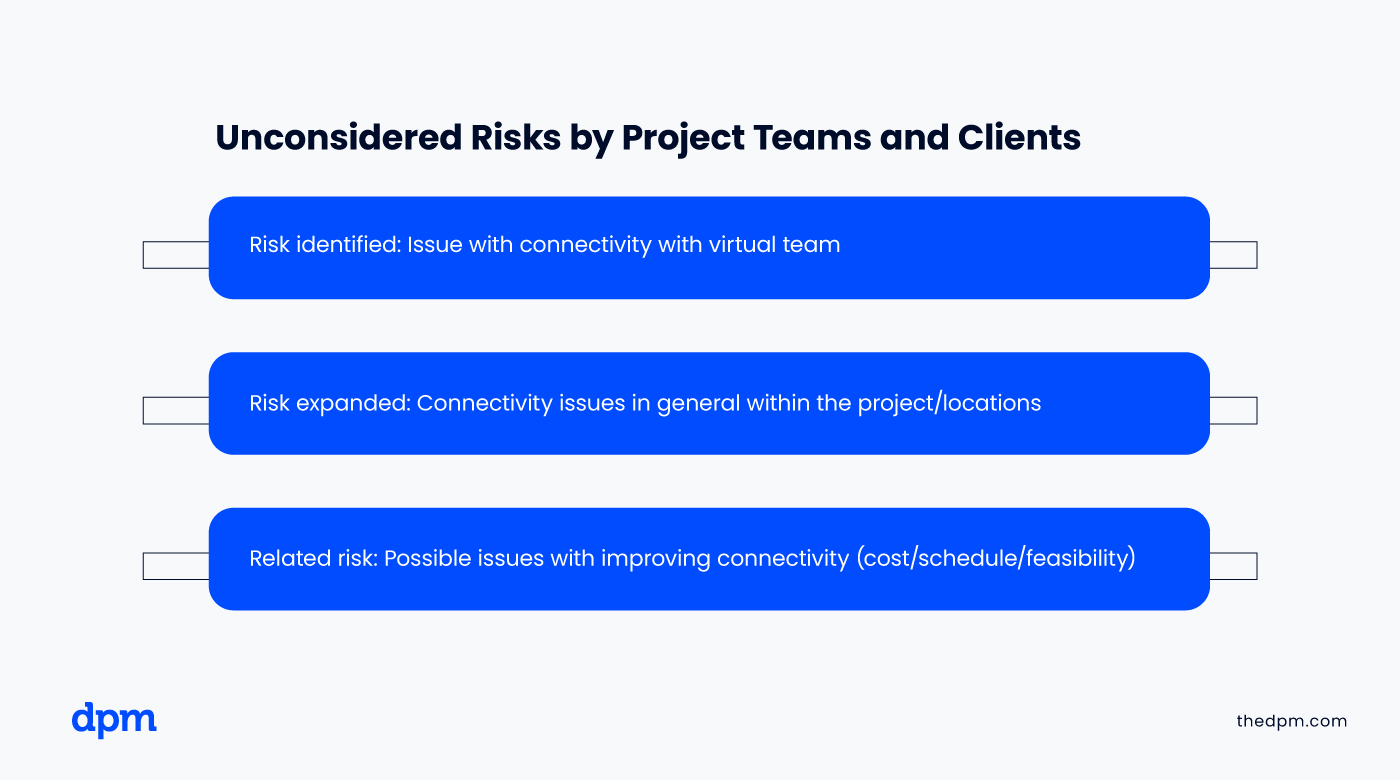
At the end of the workshop, your goal is to come away with stakeholder alignment on project risks, the desired risk response, and the expected impact of the risks. Stakeholder buy-in is critical for a successful risk response, so time in the workshop is likely to be time well-spent.
5. Assign risk owners
As you identify risks, you should work with the team to assign owners (including yourself). Project managers are responsible for risk management too!
That being said, the project manager can’t own everything. Assigning risk owners can be the most difficult area of risk management to finalize because it requires stakeholder accountability.
Make sure that risk owners have reviewed the risk management plan and are clear on their responsibilities. Follow up with them as you monitor risk throughout the project life cycle.
6. Populate the risk register
Following the risk workshop, finish populating any information required for the risk register . This includes a description of the risk, the risk response category, detailed risk response, risk status, and risk owner.
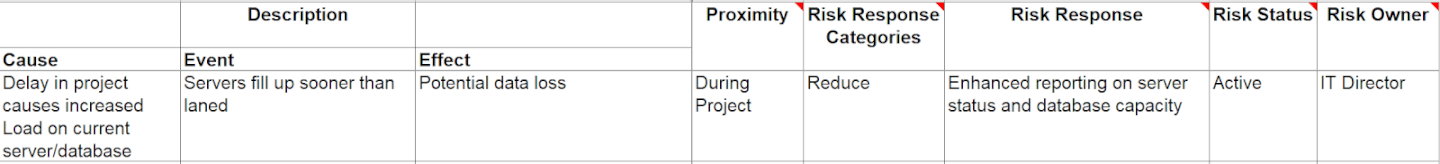
What’s important to remember during this exercise is ensuring that the risk response reflects the severity and importance of the risk. You can then review the broader risk register to understand any wider correlations that might exist among risks.
7. Publish the risk register
Send around the updated risk register within 48 hours of the workshop to give everyone time to read and process the output.
You can also use the risk register within wider project discussions to explain or define the timeline for a project or specific actions that need to be completed. It’s important to be timely so that the output can be used in other project artifacts.
8. Monitor and assess risks continuously throughout the project
New risks are introduced to a project constantly. In fact, mitigating one risk might create another risk or leave “residual risk.”
If feasible within your project constraints, try to run risk workshops periodically throughout the duration of the project or incorporate risk register reviews into other recurring planning activities.
Nothing feels quite as deflating as when you swerve to avoid one risk only to drive blindly into another, much bigger risk.
9. Archive your risk management plan in a reusable & accessible format
After your project, it’s a good idea to archive your risk management plan for future reference.
There are many reasons why (in fact, it may be mandatory in your organization), but here’s the main one: while not every risk management plan suits every project, the risk and response strategies may remain applicable. Use past risks to create a foundation for your next project.
Examples Of Risk Management Plans In Action
Admittedly, the word “risk” is itself a bit broad. Not having enough resources to hit the project deadline is a risk. Hurricane season is a risk. Disruption of the space-time continuum is a risk.
So, where do you draw the line on what types of risks to consider—which risks have a large enough potential impact to require attention, or even a contingency plan?
Here’s one way to think about it:
If the item is related to people, processes, resources, or technology and has any likelihood of threatening project success, you should log it as a risk.
Now, you might not need to do a comprehensive analysis on every risk in your risk register, but you do need to revisit the risks identified and conduct risk monitoring throughout the project. If someone starts testing a time machine near your office, for example, your highly unlikely space-time continuum risk has escalated.
Does this matter?
Yes. To prove it, here’s a simple example of risk management that saved a project:
A colleague was working on a service design project that required in-person research (this was before COVID-19), and on her RACI chart , she had clearly communicated to the client that it was the client’s responsibility to book a meeting space to conduct this research. She had logged a risk with her team that the client might not be able to secure a space.
Two days before the research commenced, the client informed her they weren’t able to secure the space. Luckily, her risk mitigation strategy on this particular risk was to book a backup space at the office, which she had done weeks ago.
Something that could have stalled the project for weeks had become nothing more than an email that said something like “All good, we’ll use our space."

Here’s another example:
An agency agreed to an aggressive timeline for a highly technical project. The team had raised concerns as the project was being initiated, but leadership still wanted to proceed. The project manager and technical architect logged the timeline risk before the project started, and their risk response strategy was to re-evaluate the project timeline using a Monte Carlo simulation.
After calculating a pessimistic, optimistic, and likely duration for every project activity on the critical path, they determined mathematically that the project had a 3% chance of hitting the deadline.
The project manager raised this with the client, and the client agreed to re-scope the project and re-baseline the project before getting going. It was too big of a risk for them to take.

Risk Register Template
There are a lot of risk register templates available online, and I would recommend looking at one that fits your needs, rather than one that includes every possible scenario.
In the risk management plan template available in DPM Membership , we’ve tried to keep the risk register as simple as possible to ensure that you’re able to enter the relevant information for your project.
Best Practices For Risk Management Plans
Consider these best practices to help you craft an effective risk management plan:
- Develop the risk management plan during the project planning phase, after you’ve developed the project charter and the project management plan, to give stakeholders the necessary context
- Adapt the format and level of detail of the risk management plan to align with the needs of the project, industry, and organization that you support
- Assign a risk owner to every risk identified in your risk register, and hold them accountable for the risk response
- Continuously identify risks throughout the project life cycle and update the risk register accordingly
- During project closing , archive your risk management plan and use it to inform risk planning on future projects.
What's Next?
Whether you’re a novice project manager or a seasoned pro, having a good risk management plan is vital to project success. And, the key to a successful risk management plan is adaptability. You need to make sure that, with every project you run, you can adapt the risk management plan to your project, industry, and organization.
Dive deeper into these strategies by enrolling in one of these comprehensive risk management courses .
17 Project Risk Management Courses To Take In 2024
Project Risk Management: How To Do It Well & 5 Expert Tips

Time Tracking: Your Secret Risk Management Superpower
- Sign up for free
- SafetyCulture
- Risk Analysis
Risk Analysis: A Comprehensive Guide
Everything you need to know about risk analysis: its components, types, and methods, as well as examples and steps on how to perform risk analysis

What is Risk Analysis?
Risk analysis is a multi-step process aimed at mitigating the impact of risks on business operations. Leaders from different industries use risk analysis to ensure that all aspects of the business are protected from potential threats. Performing regular risk analysis also minimizes the vulnerability of the business to unexpected events.
Difference Between Risk Assessment and Risk Analysis
Risk assessment is just one component of risk analysis. The other components of risk analysis are risk management and risk communication. Risk management is the proactive control and evaluation of risks while risk communication is the exchange of information involving risks. Unlike risk analysis, risk assessment is primarily focused on safety and hazard identification .
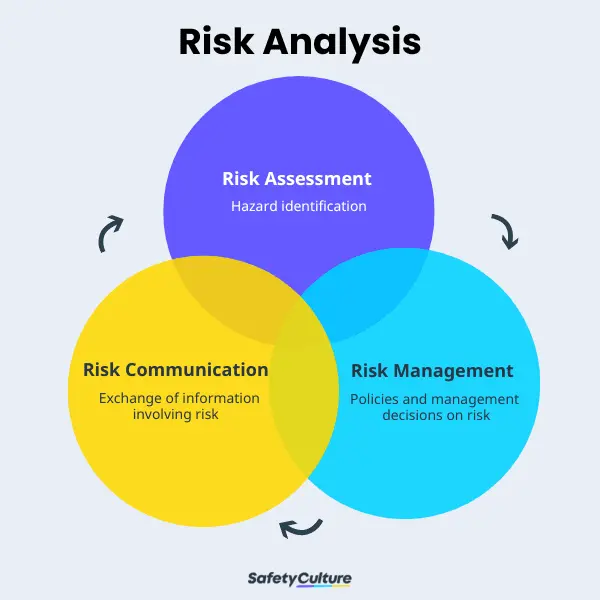
Risk Analysis Framework
Types of Risk Analysis
As risk analysis covers a wide range of topics, there are many approaches to analyzing risks or types of risk analysis. These include, but are not limited to, the following:
- Risk Benefit & Cost Benefit Analysis A risk benefit analysis involves weighing the pros and cons (benefits and risks) of an action. Elements are ranked and evaluated against the impact of their potential success or failure. Meanwhile, a cost benefit analysis sums the projected or estimated costs of an action and weighs the total cost against the potential benefits and opportunities.Both types of analysis help leaders carefully weigh their decision in pursuing a plan or action. Choosing to pursue a risk-heavy or cost-heavy action can result in losses.
- Needs Assessment A needs assessment is a systematic process of identifying and evaluating organizational needs and gaps. It gives leaders an idea of where the business may be lacking and helps them refocus resources towards achieving goals more efficiently.
- Business Impact Analysis A business impact analysis entails planning for operational disruptions caused by natural disasters and other external factors. It is the basis for investment in recovery, prevention, and mitigation strategies.
- Failure Mode and Effect Analysis A failure mode and effects analysis is a systematic method of anticipating potential failures in business processes and mitigating their impact on customers. It improves product and service reliability and reduces the cost of failures.
- Root Cause Analysis A root cause analysis focuses on identifying and eliminating root causes to solve problems. It helps in the prevention of recurring problems by targeting the ineffective systems behind them. Aside from failure mode and effects analysis, other root cause analysis tools are 5 Whys , 8D , and DMAIC (part of Six Sigma ).
Risk Analysis Methods
There are two main risk analysis methods. The easier and more convenient method is qualitative risk analysis. Qualitative risk analysis rates or scores risk based on the perception of the severity and likelihood of its consequences. Quantitative risk analysis , on the other hand, calculates risk based on available data.
Types of risk analysis associated with qualitative risk analysis are all root cause analysis (RCA) tools except for failure mode and effects analysis, needs assessment, and risk matrix. Furthermore, the most common types of the latter are the 3×3 risk matrix, 4×4 risk matrix, and 5×5 risk matrix .
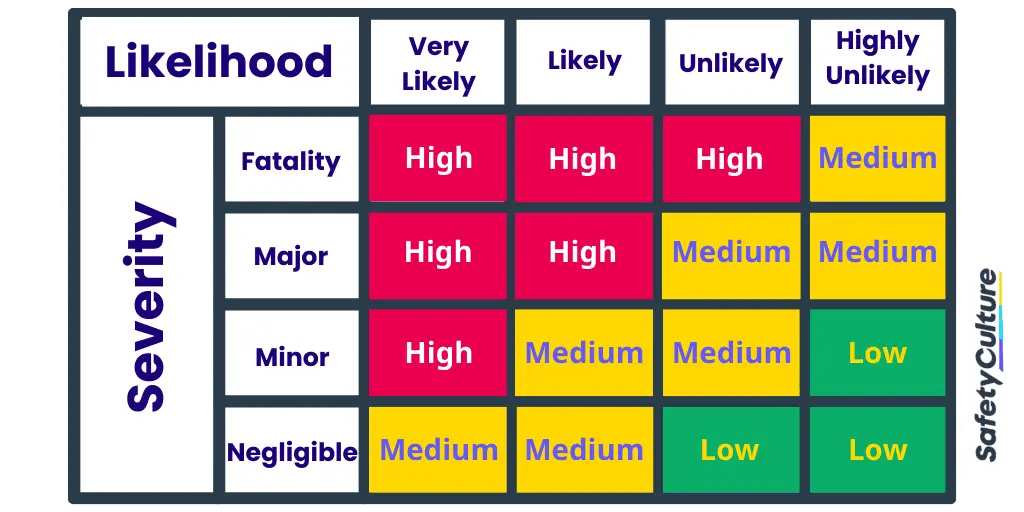
Risk Assessment Matrix | SafetyCulture
Types of risk analysis included in quantitative risk analysis are business impact analysis (BIA), failure mode and effects analysis (FMEA), and risk benefit analysis.
A key difference between qualitative and quantitative risk analysis is the type of risk each method results in. For qualitative risk analysis, this is projected risk, which is an estimation or guess of how the risk will manifest. Meanwhile, quantitative risk analysis deals with statistical risk. Unlike projected risk, statistical risk is specific and verified. For this reason, it’s often used in the calculation of insurance premiums.
Risk Analysis Example
Though risk analysis is used across industries by businesses of all sizes and types, some leaders may find a risk analysis example that’s specific to their industry more helpful than a generic one. Here are risk analysis examples for three major industries: construction, transport & logistics, and manufacturing.
Construction Risk Analysis Example : The owner of a construction company was presented with a project proposal to build a luxury resort. While pursuing this project may lead to good press for the company, the owner is hesitant to accept the project because her company specializes in mid-range residential buildings. Taking on this project would be both a leap and a challenge. Before making a final decision, she performs a risk-benefit analysis together with her team to see if the benefits of pursuing this project outweigh the risks.
Transport & Logistics Risk Analysis Example : The director of a multinational shipping company is anxious about the impact an upcoming storm will have on business operations. She believes the company should set aside some money for recovery after the storm hits. Her colleague, however, thinks differently. He argues that the storm won’t affect them that much. To convince her colleague and fellow directors, she performs a business impact analysis and presents its results in the next board meeting.
Manufacturing Risk Analysis Example : A newly hired manager is in charge of preparing a factory and its workers for a large influx of customer orders due to the summer season. To get an understanding of what he needs to do for this factory to succeed in producing enough units, he performs a quick needs assessment by asking the workers to fill out a survey on the factory’s processes.
How to Perform Risk Analysis
For leaders who have already decided on the type of risk analysis to perform, here are steps and instructions on how to perform risk analysis for each type:
How to Perform Needs Assessment
- Step 1: Identify requirements – What must the business deliver to succeed?
- Step 2: Assess existing resources – What can be used to achieve success?
- Step 3: Identify needs – What does the business lack that is critical to success?
- Step 4: Develop a plan of action – What must be done to fill the gaps and succeed?
Needs Assessment Template
Use this digital template to identify business/department, performance, and learning needs. It has all the tools leaders need to improve the management of their businesses.
How to Perform Business Impact Analysis
- Step 1: Gather information on business processes, finances, and management.
- Step 2: Identify Recovery Time Objective (RTO) or how long it takes to restore business processes after disruption. RTO helps determine how long the business can function without normal business processes.
- Step 3: Identify Recovery Point Objective (RPO) or the acceptable loss to customers when a disruption occurs. RPO helps determine the estimated financial impact on the business.
- Step 4: Develop workaround procedures of the business in the event of disruption.
- Step 5: Decide business needs based on the information gathered in previous steps.
Business Impact Analysis Template
Use this digital template to assess the impact of possible disruptive events across key business functions. This template includes an assessment of losses in terms of operational activities and revenue. Leaders can use it to prioritize functions for recovery during crises.
How to Perform Failure Mode and Effects Analysis
- Step 1: Identify mechanism of failure
The mechanism of failure (potential failure modes, effects, and causes) can be identified properly when leaders in charge of FMEAs account for past failures, agree upon certain assumptions, and establish ground rules.
- Step 2: Determine RPN
The risk priority number is used to prioritize the potential failures that require additional planning. It’s a product of three factors: severity, occurrence, and detection.

FMEA: RPN Risk Analysis | SafetyCulture
Leaders should focus their improvement efforts on potential failures at the top 20% of the highest RPNs. These high-risk failure modes must be addressed through effective action plans.
- Step 3: Follow-up on actions
After establishing and executing effective action plans, leaders should remember to continuously review these plans and the high-risk failure modes they address.
Failure Mode and Effects Analysis Template
Use this digital template to identify problems in processes or products. Describe the potential failure effect, the potential cause, and current controls. Add the severity, occurrence, and detection ratings. Finally, record the RPN and sign-off.
How to Perform Root Cause Analysis
- Step 1: Define the problem – In the context of risk analysis, a problem is an observable consequence of an unidentified risk or root cause.
- Step 2: Select a tool – 5 Whys , 8D , or DMAIC
5 Whys involves asking the question “why” five times. Though 5 Whys is the easiest to use, it can also oversimplify problems. 8D stands for the eight disciplines of problem-solving. While 8D provides long-term solutions, performing it correctly requires extensive training .
DMAIC, on the other hand, is more comprehensive than 5 Whys, but also relatively easier to perform than 8D, especially if the third step (Analyze) is simplified.
- Step 3: Implement actions – Address root cause/s identified using the tool selected in the previous step by creating and implementing actions. These actions should be specific and directed to the person/s most capable of executing them.
Root Cause Analysis Template
Use this digital template to analyze a recurring problem and its effect on productivity. List reasons why the problem occurs and rate how likely they are to be root causes. Once a root cause has been identified, choose its category and provide a prevention strategy.
For leaders who haven’t decided on a specific type or want a general outline of how to perform risk analysis, refer to the steps below:
- Set the goal for risk analysis
- Collect data to identify risks
- Add values to risks
- Identify highest-priority risks
- Develop a plan to mitigate these risks
- Follow through with the plan
- Review the effectiveness of the plan
Create a Risk Analysis Template
Eliminate manual tasks and streamline your operations.
How to Manage and Communicate Risks
One way to manage risks effectively is to use the ISO 31000 standard. ISO 31000 is an internationally recognized benchmark for risk management. It can be summarized into three guiding rules for leaders to follow:
- Risk management must be structured, innovative, inclusive, dynamic, continuously improving, and customized to fit business objectives.
- Leaders must proactively integrate risk management on all levels of the business.
- Risk management policies and practices should support open risk communication.
Another key aspect of using ISO 31000 is to ensure that all employees are familiar with the standard and/or have received related training on how to apply the standard in their work. While leaders should take responsibility for the overall risk management, they should be careful to not alienate employees from this process. Without the support and input of employees, implementing ISO 31000 will be much harder than it needs to be.
Improve your GRC management
Simplify risk management and compliance with our centralized platform, designed to integrate and automate processes for optimal governance.
ISO 31000:2018 Risk Management Template
Use this digital template to establish a solid risk management framework based on ISO 31000. Show leadership by making a commitment to risk management. Share the responsibility of managing risks with other stakeholders in the business, including employees.
Though adhering to the ISO 31000 standard is recommended, this can seem intimidating or overly complicated for smaller businesses or those with less resources to spend on risk management. A temporary alternative is to use a risk management plan , which should have the following parts:
- Descriptions of all identified risks, their consequences, and possible causes
- A model for estimating the likelihood and severity of consequences (risk analysis)
- Corrective actions to target possible causes or to lessen the severity of consequences
When using a risk management plan , it can be helpful to have a risk management plan template that’s easy to distribute to employees and update when needed. Without a template, it can be difficult to use or create a risk management plan for the entire business.
Risk Management Plan Template
Use this digital template to assess the likelihood and severity of consequences. Specify planned mitigation strategies and the employee/s responsible for executing them. Give the estimated cost and timeline of mitigation actions.
Manage Risks with SafetyCulture (formerly iAuditor)
SafetyCulture is a digital inspection platform businesses can use to identify, analyze, communicate, and manage risks effectively. Together with Mitti, a technology-first insurance company, SafetyCulture rewards businesses that are proactive in managing their risks.
SafetyCulture Platform for Teams
Why use safetyculture.
Minimize your business’ vulnerability to unexpected events and potential threats with a digital tool like SafetyCulture .
✓ Simplify processes with digital checklists ✓ Receive professional reports and share instantly ✓ Use for teams of any size
Streamline your organization’s operations and workflow with our digital checklist. It empowers you to:
- Maintain safety and compliance standards with customizable templates
- Increase your team’s engagement and accountability including contractors and stakeholders
- Create powerful workflows by integrating your existing software
- Gain greater visibility and transparency with real-time reporting
- Access unlimited storage and data security for your reports
Take advantage of our comprehensive features to optimize your operations and enhance workplace safety today.
FAQs about Risk Analysis
What are the 4 components of risk analysis.
The four components of risk analysis are hazard identification, risk assessment, risk management, and risk communication. The risk analysis process follows a general format but can differ based on the needs of an organization or which structure works for them.
What is a risk analysis checklist?
A risk analysis checklist or template is a document that you can use to verify that all aspects of a project or business are analyzed for potential risks. Utilizing this kind of tool helps ensure that nothing was overlooked and also helps maintain a standardized approach when it comes to managing risks.
What is the most commonly used technique for risk analysis?
The most commonly used technique for risk analysis is through the use risk matrix. It is a simple yet effective method that helps assess and prioritize risks based on their likelihood of occurrence and potential impact on a project or business. The risk matrix is typically represented with a visual aid or chart.
SafetyCulture Content Team
Related articles

- Layer of Protection Analysis
Discover the key aspects of and strategies for LOPA to effectively evaluate and enhance safety systems in high-risk industries.
- Find out more

- Dust Hazard Analysis
Explore the essential components of DHA, its significance, and the strategies for ensuring industrial safety.

- Reputational Risk
Learn more about reputational risk, why it’s important that businesses properly manage it, and how to effectively implement risk mitigation strategies.
Related pages
- Hazard Assessment Software
- Process Hazard Analysis Software
- EHS Risk Assessment Software
- Integrated Risk Management Software
- Operational Risk Management Software
- Reputation Management
- Environmental Aspects and Impacts
- Safety Improvement Plan Template
- Contract Risk Assessment Checklist
- Point of Work Risk Assessment Template
- 7 Best Risk Assessment Templates
- 5×5 Risk Matrix Template
Not finding what you are looking for?
- Chat with us!
- Culture and Business Transformation
7 key types of business risk every leader should plan for (2024 update)
- August 23, 2024
3. Compliance risk
How familiar are you with the laws and regulations that apply to your business? Compliance can be tricky for many reasons. Compliance risks represent a critical challenge for businesses operating in today’s highly regulated environment. Failure to adhere to industry regulations, data protection laws, and corporate governance standards can have significant legal and financial consequences. Non-compliance may lead to hefty fines, legal battles, and damage to a company’s credibility.
Recently, the Ministry of Manpower (MOM) in Singapore introduced the Complementary Assessment Framework (COMPASS) , which requires employers to offer clear career development pathways for foreign employees. This underscores the importance of businesses understanding and navigating these evolving regulations. To mitigate compliance risks related to COMPASS, it is crucial to implement robust employment verification strategies, including thorough background screening and employment history checks, ensuring adherence to current and new regulatory requirements.
4. Financial or economic risk
Financial or economic risk is closely related to business profits, so investors and shareholders often scrutinise it. Financial risks are caused by multiple factors, such as market movements, foreign currency exchange rates, commodity price fluctuations, etc. Strategies to mitigate financial or economic risk usually aim to ease cash flow issues, and common tactics include getting insurance, diversifying income streams, and limiting the amount or tenure of loans.
5. Reputational risks
Reputational risk involves the potential damage to a company’s public image and brand value, which can arise from various incidents, including unethical breaches, product failures, or poor customer service. Social media exacerbates this risk by amplifying the impact of any negative event. For instance, in 2017, United Airlines faced a severe reputational crisis when a video of a passenger being forcibly removed from an overbooked flight went viral. This incident led to widespread media condemnation and public outrage, significantly damaging the airline’s reputation. In such a highly connected environment, even a single misstep can quickly escalate, underscoring the importance of proactive reputation management.
6. Geopolitical risks
Geopolitical risks can significantly impact supply chains, as political instability, trade disputes, and international sanctions disrupt the flow of goods and materials across borders. The ongoing conflict between Russia and Ukraine serves as a stark example of such disruptions. The war has severely affected global supply chains , particularly in sectors reliant on key exports like grain and energy. For instance, companies worldwide have faced shortages and price increases for agricultural products due to the blockade of Ukrainian ports and the destruction of infrastructure. Additionally, disruptions in energy supplies from Russia have led to increased costs and supply uncertainties for industries dependent on natural gas and oil.
7. Hiring risk
When hiring, one of the most critical risks businesses face is the potential for hiring the wrong person, which can lead to significant consequences. A notable example of this risk is the case of a Nanyang Technological University (NTU) dropout who forged a bachelor’s degree in engineering and deceived companies, securing positions in The Walt Disney Company, Marshall Cavendish, and Scholastic Education International. It is shocking easily to get a fake university degree, a recent investigation by a Singapore news media reported.
Organisations can protect themselves from potential financial losses, reputational damage, and operational disruptions by ensuring candidates’ authenticity and qualifications.
How to minimise business risk
To effectively manage risks and ensure long-term stability, organisations must work towards getting the basics of risk management strategies right . Some essential actions include:
- Establish a comprehensive risk management framework that integrates risk identification, assessment, and mitigation processes across all levels of the organisation.
- Monitor and review your risk management strategies to adapt to evolving risks and ensure your controls remain effective.
- Cultivate a risk-aware culture by promoting clear communication, ongoing training, and accountability among all employees.
- Conduct background checks on potential employees.
Understandably, most businesses don’t have the time, know-how, and manpower to dedicate to thorough intelligence gathering. There’s also the grey area of privacy laws to consider – how much is a company allowed to dig into their potential hires or partners? In such cases, trusting a specialist and market leader like RMI to do the legwork for you can be the most cost-effective solution. Contact us to learn more about our solutions.
Proudly a member of

Preferred partners

Risk Management Intelligence 20 Anson, Road #19-01 Twenty Anson, Singapore 079912 Company Reg No: 201210650Z
- +65 6309 1800
- [email protected]
© RMI - All Rights Reserved 2024. Site by Manning&Co.
Quick links
Get the latest insights.
JavaScript is disabled in your browser. To view the website properly, please enable JavaScript in your browser settings and refresh the page.
Apply for and manage a grant or program for your business.
Manage your interactions with the R&D Tax Incentive program.
- Risk management
- Risk assessment and planning
Business risks
On this page
What is risk management?
How you can manage risk in your business, why manage risk, risks that you must manage, types of risk, risk management in your state or territory.
Risk management helps you make better business decisions. It involves reducing the things that could have a negative effect on your business. For example, the reducing the risk of injury by through safety procedures. You can also look for opportunities that could have a positive impact on your business.
Jimmy owns a transport business. He drives trucks, moving commercial products around Australia. Some of the hazards Jimmy faces each day include:
- contact with chemicals and fumes when refuelling
- uncomfortable seating and fatigue, especially on long journeys
- no heating or air-conditioning to change the temperature inside the truck.
Some steps Jimmy could take to reduce the risks in his daily work include:
- wearing appropriate clothing to reduce his exposure to chemicals
- taking regular breaks during his trips to stretch and walk around
- ensuring that he only works the legal hours for his industry to deal with fatigue
- installing fans or air-conditioning in his truck
- having suitable clothing and water for each trip.
Begin by finding out about risk management practices and how you can use them. You should also talk to others involved in your business (including your employees and customers) to decide on the best way to manage risk in your business.
Before you decide what to do, you’ll need to work out what your risks are and which ones are most urgent:
- Identify – work out what risks your business could face.
- Analyse – find the level of the risks and which ones are most urgent.
- Evaluate – compare the risk against set risk criteria to decide what to do.
Find out how to manage risk in your business.
By managing risk, you can reduce the impact of unexpected events on your business.
Managing risk can also help you to:
- improve your relationships with customers, suppliers, employees and the community, by understanding and managing their expectations
- improve staff confidence in a safe work environment, through workplace health and safety (WHS) and workers’ compensation insurance
- keep your business open during natural or economic disasters, by having an emergency management plan
- reduce your compliance and insurance costs, by having a lower risk of damages.
You won't always have enough information or the resources to manage every risk. A good risk management plan will allow you to change your approach if it isn't working, or when unexpected risk happens.
You're required by law to manage some risks. For example, you must manage or reduce the risk of:
- accidents and injury by making your workplace safe under work health and safety (WHS) laws
- customer complaints by treating customers fairly under Australian Consumer Law
- injury or harm to employees by having workers' compensation insurance
- damaging the environment by meeting the environmental laws that apply to you.
It's a good idea to understand the different types of risks your business may face so you can recognise and plan ahead for them.
Risks can be:
- opportunity-based risk from choosing one option over other options (such as buying a new property)
- uncertainty-based risk from uncertain or unknown events (such as natural disasters or loss of suppliers)
- hazard-based risk from dangerous materials or actions (such as using hazardous chemicals or working at heights).
Opportunity-based risks
This type of risk comes from taking one opportunity over others. By deciding to commit your resources to one opportunity, you risk:
- missing a better opportunity
- getting unexpected result.
Opportunity-based risks for a business include moving a business to a different location, buying a new property, or selling a new product or service.
Uncertainty-based risks
This type of risk is from uncertainty around unknown or unexpected events. It’s hard to predict these events and the damage they can cause. It’s also hard to control the damage once they occur.
Examples of uncertainty-based risks include:
- damage by fire, flood or other natural disasters
- unexpected financial loss due to an economic downturn, or bankruptcy of other businesses that owe you money
- loss of important suppliers or customers
- decrease in market share because new competitors or products enter the market
- court action.
To reduce the impact of uncertain events on your business, you can do things like:
- develop an emergency management plan to reduce the damage to your business in an emergency
- keep a supplier database to help you manage your stock and equipment
- seek and use regular feedback from your customers and other people you deal with in your business
- check your business environment regularly for risks such as changes in trends and customer expectations
- seek expert advice every now and then to check the financial health of your business and to get advice on how to improve your business.
Hazard-based risks
These types of risks come from dangerous situations in the workplace.
Some common examples include:
- physical hazards caused by high noise levels, extreme weather or other environmental factors
- equipment hazards caused by faulty equipment or poor processes when using equipment such as machinery
- chemical hazards caused by improper storage or use of flammable, poisonous, toxic or carcinogenic chemicals
- biological hazards caused by viruses, bacteria, fungi or pests
- ergonomic hazards caused by poor workplace design, layout or equipment use
- psychological hazards caused by bullying and harassment , discrimination, heavy workload or mismatch of employee skills with job duties.
Find information on managing risk in your state or territory
Australian capital territory.
Learn about risk management for your business on the Access Canberra website.
New South Wales
Read SafeWork NSW's work environment and facilities to help identify safety risks in your workplace.
Northern Territory
Read about the NT WorkSafe's small business safety program .
Read about risk management on the Queensland Government website.
South Australia
Find information on risk management on the South Australian Government website.
Read information on managing risk in your business on the Business Victoria website.
Find out what to include in your risk management plan.
Learn about the different insurance types to protect your business from risk., was this page helpful, thanks for sharing your feedback with us..
Our live chat service is open from 8am - 8pm, Monday to Friday, across Australia (excluding national public holidays ).
Learn about the other ways you can contact us .
All our experts are busy now. Please try again later or contact us another way
We're open from 8am - 8pm, Monday to Friday, across Australia (excluding national public holidays ).
We use cookies to give you a better experience on our website. Learn more about how we use cookies and how you can select your preferences.
- Contact sales
Start free trial
How to Make a Risk Management Plan (Template Included)

You identify them, record them, monitor them and plan for them: risks are an inherent part of every project. Some project risks are bound to become problem areas—like executing a project over the holidays and having to plan the project timeline around them. But there are many risks within any given project that, without risk assessment and risk mitigation strategies, can come as unwelcome surprises to you and your project management team.
That’s where a risk management plan comes in—to help mitigate risks before they become problems. But first, what is project risk management ?
What Is Risk Management?
Risk management is an arm of project management that deals with managing potential project risks. Managing risks is arguably one of the most important aspects of project management.
The risk management process has these main steps:
- Risk Identification: The first step to managing project risks is to identify them. Use data sources such as information from past projects or subject matter experts’ opinions to estimate all the potential risks that can impact the project.
- Risk Assessment: Once the project risks are identified, prioritize them by looking at their likelihood and level of impact.
- Risk Mitigation: Now it’s time to create a contingency plan with risk mitigation actions to manage your project risks. You also need to define which team members will be risk owners, responsible for monitoring and controlling risks.
- Risk Monitoring: Risks must be monitored throughout the project life cycle so that they can be controlled.
Even one risk can jeopardize the entire project plan . There isn’t usually just one risk per project, either; there are many risk categories that require assessment and discussion with stakeholders. That’s why risk management needs to be both a proactive and reactive process that is constant throughout the project life cycle. Now let’s define a risk management plan.
What Is a Risk Management Plan?
A risk management plan defines how the project’s risk management process will be executed. That includes the budget , tools and approaches that will be used to perform risk identification, assessment, mitigation and monitoring activities.
Get your free
Risk Management Plan Template
Use this free Risk Management Plan Template for Word to manage your projects better.
A risk management plan usually includes:
- Methodology: Define the tools and approaches that will be used to perform risk management activities such as risk assessment, risk analysis and risk mitigation strategies.
- Risk Register: A risk register is a chart to document the risk identification information.
- Risk Breakdown Structure: This is a chart that identifies risk categories and the hierarchical structure of project risks.
- Risk Assessment Matrix: A risk assessment matrix allows teams to analyze the likelihood and the impact of project risks so they can prioritize them.
- Risk Response Plan: A risk response plan is a project management document that explains the risk mitigation strategies that will be employed to manage risks.
- Roles and responsibilities: The risk management team members have responsibilities as risk owners. They need to monitor project risks and supervise their risk response actions.
- Budget: Have a section to identify the funds required to perform risk management activities.
- Timing: Include a section to define the schedule for the risk management activities.
How to Make a Risk Management Plan
For every web design and development project, construction project or product design, there will be risks. That’s the nature of project management. But that’s also why it’s always best to get ahead of them as much as possible by developing a risk management plan. We’ve outlined the steps to make a risk management plan below.
1. Risk Identification
Risk identification occurs at the beginning of the project planning phase, as well as throughout the project life cycle. While many risks are considered “known risks,” others might require additional research.
Create a risk breakdown structure to identify project risks and classify them into risk categories. You can do this by interviewing all project stakeholders and industry experts. Many project risks can be divided into risk categories, like technical or organizational, and listed out by specific sub-categories like technology, interfaces, performance, logistics, budget, etc. Additionally, create a risk register to share with everyone interviewed for a centralized location of all known risks revealed during the identification phase.
It’s easy to create a risk register using online project management software. For example, use the list view on ProjectManager to capture all project risks, add their priority level and assign a team member to own identify and resolve them. Better than to-do list apps, you can attach files and tags and monitor progress. Track the percentage complete and even view risks from the project menu. Keep risks from derailing projects by signing up for a free trial of ProjectManager.
2. Risk Assessment
In this next phase, review the qualitative and quantitative impact of the risk—like the likelihood of the risk occurring versus the impact it would have on the project—and map that out into a risk assessment matrix
First, you’ll do this by assigning the risk likelihood a score from low probability to high probability. Then, map out the risk impact from low to medium to high and assign each a score. This provides an idea of how likely the risk is to impact project success as well as how urgent the response will need to be.
To make it efficient for all risk management team members and project stakeholders to understand the risk assessment matrix, assign an overall risk score by multiplying the impact level score with the risk probability score.
3. Create a Risk Response Plan
A risk response is the action plan taken to mitigate project risks when they occur. The risk response plan includes risk mitigation strategies to mitigate the impact of project risks. Doing this usually comes with a price—at the expense of your time or your budget. So you’ll want to allocate resources, time and money for your risk management needs before creating the risk management plan.
4. Assign Risk Owners
Next, assign a risk owner to each project risk. Those risk owners become accountable for monitoring the risks assigned to them and supervising the execution of the risk response if needed.
Related: Risk Tracking Template
When creating the risk register and risk assessment matrix, list out the risk owners, that way no one is confused as to who will need to implement the risk response strategies once the project risks occur, and each risk owner can take immediate action.
Be sure to record the exact risk response for each project risk with a risk register and have the risk response plan approved by all stakeholders before implementation. That way, there’s a record of the issue and the resolution to review once the project is finalized.
5. Understand Your Triggers
This can happen with or without a risk already having impacted the project—especially during project milestones as a means of reviewing project progress. If they have, consider reclassifying those existing risks.
Even if those triggers haven’t been met, it’s best to come up with a backup plan as the project progresses—maybe the conditions for a certain risk won’t exist after a certain point has been reached in the project.
6. Make a Backup Plan
Consider your risk register and risk assessment matrix a living document. Project risks can change in classification at any point, and because of that, come up with a contingency plan as part of the process.
Contingency planning includes discovering new risks during project milestones and reevaluating existing risks to see if any conditions for those risks have been met. Any reclassification of a risk means adjusting your contingency plan.
7. Measure Your Risk Threshold
Measuring your risk threshold is all about discovering which risk is too high and consulting with project stakeholders to consider whether or not it’s worth it to continue the project—worth it whether in time, money or scope .
Here’s how the risk threshold is typically determined: consider your risks that have a score of “very high”, or more than a few “high” scores, and consult with your leadership team and project stakeholders to determine if the project itself may be at risk of failure. Project risks that require additional consultation are risks that have passed the risk threshold.
To keep a close eye on risks as they raise issues in the project, use project management software. ProjectManager has real-time dashboards embedded in our tool, unlike other software that require teams to manually build them. We automatically calculate the health of projects, checking if teams are on time or running behind. Get a high-level view of how much you’re spending, progress and more. The quicker the risk is identified, the faster you can resolve it.
Free Risk Management Plan Template
This free risk management plan template will help prepare your team for any risks inherent in the project. This Word document includes sections for your risk management methodology, risk register, risk breakdown structure and more. It’s so thorough, you’re sure to be ready for whatever comes your way. Download the template today.

Best Practices for Maintaining Your Risk Management Plan
Risk management plans only fail in a few ways: incrementally because of insufficient budget, via modeling errors or by ignoring your risks outright.
Your risk management plan is constantly evolving throughout the project life cycle, from beginning to end. So the best practices are to focus on the monitoring phase of the risk management plan. Continue to evaluate and reevaluate your risks and their scores, and address risks at every project milestone.
Project dashboards and other risk-tracking features can be a lifesaver for maintaining your risk management plan. Watch the video below to see just how important project management dashboards, live data and project reports can be for keeping projects on track and budget.
In addition to routine risk monitoring, at each milestone, conduct another round of interviews with the same checklist you used at the beginning of the project, and re-interview project stakeholders, risk management team members, customers (if applicable) and industry experts.
Record their answers, adjust the risk register and risk assessment matrix if necessary, and report all relevant updates of your risk management plan to key project stakeholders. This process and level of transparency help identify any new risks to be assessed and shows if any previous risks have expired.
How ProjectManager Can Help Your Risk Management Plan
A risk management plan is only as good as the risk management features you have to implement and track them. ProjectManager is online project management software that lets you view risks directly in the project menu. You can tag risks as open or closed and even make a risk matrix directly in the software. You get visibility into risks and can track them in real time, sharing and viewing the risk history.

Tracking & Monitor Risks in Real Time
Managing risk is only the start. You must also monitor risk and track it from the point that you first identified it. Real-time dashboards provide a high-level view of slippage, workload, cost and more. Customizable reports can be shared with stakeholders and filtered to show only what they need to see. Risk tracking has never been easier.

Risks are bound to happen no matter the project. However, if you have the right tools to better navigate the risk management planning process, you can better mitigate errors. ProjectManager is online project management software that updates in real time, giving you all the latest information on your risks, issues and changes. Start a free 30-day trial and start managing your risks better.

Deliver your projects on time and on budget
Start planning your projects.
4 Signs Your New Business Venture Is Too Risky
If it costs too much, definitely walk away.
As an entrepreneur and founder of multiple companies, I’ve experienced the pleasure of success and the drama of failure. When I look back on the unsuccessful attempts, I can see the loopholes I missed and, in retrospect, can recognize why the opportunities failed.
4 Signs a Business Risk Is Too Risky
- It requires too much capital.
- You’re not sure of the market.
- The field is too competitive.
- You’re letting your ego make the decision.
It’s often said that failure is a better teacher than success, but that doesn’t mean we want failures. Here are a few points I’ve learned over the years that can help you minimize the failures on your entrepreneurial journey.
Related Reading Risk Averse? Don’t Let It Stunt Your Startup’s Growth
It Needs Too Much Money
First and foremost, for me, the economic viability and requirements of the new business are paramount to understanding the opportunity in front of you. Before you take the first step, you must have an understanding of the capital requirements, the time frame needed to achieve profitability, and the total economic return during the business life .
Dig deep and understand the cash requirements you will need to reach the break-even point. Lack of capital is the No. 1 cause of business failure. Don’t even consider starting a business until you truly know the capital needs of the business and know that you have the means to get there.
Knowing the capital requirements also means knowing the length of time it will take you to get to profitability . Is it six months? A year? Longer? While you may never know exactly the time frame, plan conservatively and have extra capital for the just-in-case moments.
It is also important to forecast an effective return . It does no good to spend a bunch of money on getting a business to profitability if you are never going to receive the expected, or necessary, return. So have enough capital, know your time frame and your expected profitability before ever opening the doors.
You’re Not Sure of the Market
Of additional importance is understanding your market and, specifically, the demographic of your customer base. Knowing who your customer is before you start the business lets you develop a strategic and effective marketing plan.
This also is critical in helping you determine the total capital needs as referenced above. Whether it’s print advertising, internet or social media, all cost money and need to be factored into your cash requirements. Understanding the financial viability of your customer base ensures that you have the right pricing for the right market.
There’s Too Much Competition
Knowing your competition is extremely important. Even if you’re not afraid of competition, you need to understand if the market you’re aiming for can handle another competitor. Unless you have created something new, you will face competitors and a fixed market base, so make sure there is room for one more provider.
The other thing to think about is how established your competitors are. If I’m in a really seasoned industry with only a few large competitors, I’m going to rethink my strategy and maybe take a pass. On the other hand, if there is a large market with a lot of competitors, taking a piece of the pie might be a little easier.
More From James Harold Webb This Valentine’s Day, Fall in Love With Your Job Again
Your Ego Is Making the Decision
If I’m transparent about one final point in determining the viability of a venture, it’s simply to not let my ego get in the way of a smart decision. Yes, believing in yourself is important, but don’t let that affect your ability to see a clear picture of the new business opportunity.
I’ve always been a believer in trusting my gut , but I’ve also failed when I’ve been too confident and not seen all the potential signs of failure. Take your egotistical hat off and look at this opportunity with a clean and clear vision. Ask others, including your mentors, for their opinion. The more eyes, the better.
When evaluating business opportunities, it’s crucial to be energized and ready for the journey. However, it’s equally important to understand the potential downsides, plan for them and be prepared to step back if you can’t clearly see the end-game strategy. This focus on the end-game strategy will keep you goal oriented and ensure that you’re excited about the journey and prepared for the destination.
Recent Entrepreneurial Finance Articles

- Risk Management
- Compliance Management
- 3rd Party Risk Management
- Executive Reporting
- Cyber Insurance Risk Management
- NIST 800-171
- Higher Education
- Become a Partner
- Partner Login
With Centraleyes it feels natural to manage your cyber risk and compliance levels, visualize them and even present them in a live environment
Whitepapers
- News & Updates
- Feature Reviews
- On-demand Webinars
Cyber Leaders
- US Privacy Laws Tracker
- Global Privacy Laws Tracker

- Secure Africa
- Risk Register Templates: Enhancing Your Risk Management Strategy

Rebecca Kappel
- September 2, 2024
- Yair Solow Featured on Bugy's Founder Interviews
- Centraleyes Chosen as Global Top 5 Startups of the Year - Interview
- Centraleyes on Cyber Ghost: Interview with Yair Solow
- Spotlight Q&A with Centraleyes at Safety Detectives
- Centraleyes Expands Automated Risk Register To Cover All Enterprise Risk
- New Centraleyes 4th Generation Release Officially Goes Live
- Yair Solow Featured on VPN Mentor
- Yair Solow on CNN
- CyGov Signs a Strategic Agreement with R3 (Spanish)
- Centraleyes Welcomes Co-Founder of Optiv, Dan Burns, to Its Board of Directors
- Centraleyes Continues to Expand Its Global Network of Strategic Partners with UK-based ITC Secure
- Centraleyes Introduces First Automated Risk Register
- Yair Solow Featured on Website Planet
- Trevor Failor named head of sales at CyGov
- CyGov is rebranding its platform as Centraleyes
- Cybersecurity Company Cygov Partners With Risk Management Company Foresight
- CyGov agrees strategic partnership with top 200 MSSP Cybriant
- Cyber Resilience Resource for Businesses Re-Deploying Remotely
- The Four New Pillars of Corporate Protection Yair Solow on InfoSecurity Magazine
- CyGov selected by SixThirty as Top Cyber Security Startup
- Europe's Top Cyber Security Startups
- CyGov Interviewed by MediaSet
- Eli Ben Meir's article in Security Intelligence
- Yair Solow on i24 News
- CyGov Selected by WorldBank
- Eli Ben Meir OpEd in the Houston Chronicle
- Yair Solow and Eli Ben Meir Present at the SparkLabs Demoday 8
- Financial Institutions
- Life Science
Platform Feature Reviews
- Enhance Your Cyber Maturity With ITSM Integration and Automated Remediation
- Ensure Your Ongoing Compliance With Automatic Framework Reassessment Tasks
- Stay in the Know With a Full Activity Log of Your Assessment Collection
- Add a New Entity to Perform Your Assessment in 10 Seconds
- Quantify Financial Risk With Centraleyes Platform Primary Loss Calculator
- Cover Your Entire Environment With Centraleyes's Risk Application Assessments
- Communicate Cyber Risk With Your Executives in an Intuitive, Beautifully Visualized Board Reporting
- Stay on Top of Your Vendors' Cyber History With In-Depth External Scans
- Automate the Creation and Maintenance of a Risk Register, Saving Hours on Manual Work
- Add a New Framework and Distribute Assessments in Your Organization
- View Your Organization's Risk Scoring Through the NIST Tiering Lens
- Most Intuitive Way for Compliance With the Framework Navigation Tool
- Always Prepared for the Next Task With Automated Remediation
- Effective Team Work With Drag-and-Drop Control Assignment
- Get Real-Time Critical Alerts That are Specifically Relevant to You
- MSSPs Can Manage Multiple Clients Under One Platform
- Onboard a New Vendor in Just 30 Seconds
- Turn Hours of Work Into Seconds with Centraleyes Vendor Risk Profile
- Always Informed with Centraleyes Domain Benchmarking
News & Updates
- White House and CISA Double Down on Securing Open Source Software: A New Era of Vigilance
- Massive Data Breach Exposes Personal Information of Billions
- Whistle While You Work
- Delta’s Mirror Moment: A Play of Third-Party Reflection
- The Great Cyber Debate: Regulation vs. Innovation
- CrowdStrike Outage
- How is "Materiality" Defined According to the SEC Disclosure Rules?
- Balancing Act: Streamlining Federal Cybersecurity Regulations
- Auto Sales Hit a Cyber Speedbump
- Explainer: The CDK Global Ransomware Attack
- Micro-Managed: AMD Investigates IntelBroker Hack
- Microsoft Puts Recall on Hold
- Snowflake Breach Snowballs
- Game Over? Law Enforcement Plays Hardball in Operation Endgame
- Cybersecurity in Sports: A New Arena for Risk Management
- Boeing's Sky-High Ransomware Refusal
- What was Behind the Change Healthcare Breach that Shook the Healthcare Industry?
- Cisco Raises Concerns Over Surge in Brute-Force Attacks Targeting VPN and Web Services
- Bipartisan Proposal Sparks Hope for American Privacy Rights Act
- Microsoft Responsible for Made-in-China Hack that Targeted US Officials
- AI Gets an Endorsement from Coalition
- NIST NVD "Under Construction"
- TutaCrypt to Thwart 'Harvest Now, Decrypt Later' Attacks
- 9.8/10 Severity Flaw in Team City- Patch Now!
- Blackcat Claims Responsibility for the UnitedHealth Change Breach
- US Gov's Cyber Survival Guide for Water Utilities
- Safeguarding Elections Amidst the Deepfake Deluge
- Faking the Figures (and the Faces): Deepfake Financial Frauds
- Trello Got a Scrape
- Advisory Issued for Androxgh0st Malware
- X Marks the Spot: Mandiant and SEC's Security Sway on Twitter
- Quantum Quandary: Navigating the Path to Unbreakable Encryption
- Chameleon Android Banking Trojan Morphs with Advanced Tactics, Expands Targets
- Ubiquiti Resolves User Access Bug
- The U.S. Needs a Better AI Plan
- Navigating the Cyber Currents: Ensuring a Watertight Critical Infrastructure
- Dollar Tree Breach: Supplier Roots Sprout Risks
- Applying Digital Pressure to Stop the “Citrix Bleed”
- 30-Year-Old Medical Protocol Making Headlines
- 88 Million Americans Affected in 2023 By Healthcare Data Breaches
- How to Build a Successful GRC Program to Help Reduce Your Risk Posture
- How to Stay Secure and Compliant in a World of Regulatory turmoil
- Don’t Keep Your Head in the Clouds – How to Protect Yourself from Virtual Risk
- Flash Webinar: How to Know When it's Time to Build a Risk Management Program
- Enhancing Cyber Risk Management Through the Power of Automation - Boutique Webinar
- Flash Webinar: From Technical to Business Risk - How to Communicate With Your Board
- Flash Webinar: What You Can Learn From the SolarWinds Attack to Lower Your Chances of Being Breached
- Flash Webinar: Supply Chain, 3rd-Party Vendors and the Silent Assassin Among Them
- Flash Webinar: Cyber Risk Management - it Doesn't Have to Be So Painful
Understanding British Columbia's Personal Information Protection Act (PIPA)
10 best erm software in 2024: the complete guide, new jersey privacy act 2024: what to expect.
- Colorado New AI Act: Everything you Need to Know
- Updating Security Metrics For NIST CSF 2.0: A Guide To Transitioning From 1.0 To 2.0
- When Compliance Fails: Eye-Opening Incidents in GRC You Need to Know
- CJIS Compliance Checklist: Are You Meeting All the Requirements?
- Substantive Testing vs. Control Testing: Unveiling the Difference
- DORA's Third-Party Risk Standards in 2024: A Comprehensive Guide
- The Key Components of HRIPA Compliance
- 7 Methods for Calculating Cybersecurity Risk Scores: A Guide to Risk Analysis
- 7 Best Cyber Risk Management Platforms of 2024
- The Top 7 AI Compliance Tools of 2024
- Best 5 SOC 2 Compliance Software in 2024
- ISO/IEC 42001: What You Need to Know
- 10 Best Integrated Risk Management Solutions
- Best 8 Vulnerability Management Tools for 2024
- How to Select a Qualified SOC 2 Auditor
- Maximizing Cloud Data Security: Importance, Challenges and Best Practices
- Best Strategies to Reduce Generative AI Risk
- The Best 10 Vendor Risk Management Tools
- Comprehensive Guide to AI Risk Assessment and Regulatory Compliance
- The American Privacy Rights Act: What You Need to Know
- Top Cybersecurity Websites and Blogs for Compliance in 2024
- What is the Massachusetts Data Privacy Law (MIPSA)?
- AI Auditing: Ensuring Ethical and Efficient AI Systems
- Best Practices in Audit Management Process
- Best 11 Third-party Risk Management Software in 2024
- Responsible AI Governance and Policy: Guiding Principles
- Best 7 ESG Reporting Tools for 2024
- AI Regulation in Finance: Steering the Future with Consumer Protection at the Helm
- Understanding the Regulatory Technical Standards (RTS) and Implementing Technical Standards (ITS) of DORA
- Best 7 CCPA Compliance Tools in 2024
- Top 6 Compliance Reporting Tools in 2024
- What is AI TRiSM? And Why Is It Important?
- How to Develop a Statement of Applicability: Step-by-Step Guide
- Defining Objectives within ISMS: A Strategic Blueprint
- The Ultimate Guide to Troubleshooting Vulnerability Scan Failures
- Mastering GRC Roles and Responsibilities for Compliance Organizational Excellence
- Cyber Leaders of the World: Chris Lockery, CISO at Help at Home
- Cyber Leaders of the World: Michael Anderson, CISO at the Dallas Independent School District
- Cyber Leaders of the World: Timothy Spear, Co-Founder and CTO of Whonome
- Cyber Leaders of the World: Marc Johnson, CISO at Impact Advisors
- Cyber Leaders of the World: Craig Williams, CISO at Secure Data Technologies
- Cyber Leaders of the World: Bill Genovese, CIO Advisory Partner at Kyndryl
- Cyber Leaders of the World: Dr. Brian Callahan, Graduate Program Director & Lecturer at ITWS@RPI, and CISO at PECE
- Cyber Leaders of the World: Chris Grundemann, Research Category Lead for Security and Risk at GigaOm
- Cyber Leaders of the World: Barak Blima, CISO at CHEQ
- Cyber Leaders of the World: Tony Velleca, CEO at CyberProof and CISO at UST
- Cyber Leaders of the World: Rob Black, CEO and Founder of Fractional CISO
- Cyber Leaders of the World: Zachary Lewis, CISO at the University of Health Sciences and Pharmacy in St. Louis
- Cyber Leaders of the World: Dan Wilkins, CISO at the State of Arizona
- Cyber Leaders of the World: Sagar Narasimha, CISO at Amagi
- Cyber Leaders of the World: Seema Sharma, Global Head of Information Security & Data Privacy at Servify
- Cyber Leaders of the World: Shay Siksik, VP of Customer Experience at XM Cyber
- Cyber Leaders of the World: Raz Karmi, CISO at SimilarWeb
- Data Subprocessor
- Threat-Based Risk Assessment
- Semi-Quantitative Risk Assessment
- Vulnerability-Based Risk Assessment
- Risk Management Strategy
- Authorization to Operate (ATO)
- Segregation of Duties
- PCI Penetration Testing
- Due Diligence Questionnaire
- Key Risk Indicator
- AI Risk Management
- AI Auditing
- Data Exfiltration
- Data Sovereignty
- Control Objectives for Information and Related Technologies (COBIT)
- Audit Management Software
- Vendor Framework
- AI Governance
- AI Transparency
- Internal Penetration Testing
- Cybersecurity Automation
- GDPR Compliance Risk Assessment
- Audit Fatigue
- Compliance Operations
- Risk Management Automation
- Corporate Sustainability Reporting Directive
- Man-in-the-Middle Attack
- Digital Rights Management
- Content Disarm and Reconstruction
- Calculated Risk
- Data Residency
- Asset Risk Management
- Identity Security
- Risk Modeling
- CISO Board Report
- Risk Communication
- What are the different types of compliance management tools?
- How long does SOC 2 compliance take?
- What are the Differences Between Internal and External Penetration Testing?
- What is the difference between proactive and reactive risk management?
- Why is a data retention policy important?
- What is the operational risk management process?
- How to implement the COSO framework?
- How do you perform a cyber security risk assessment?
- How to develop an enterprise risk management framework?
- How do you respond to a security questionnaire?
- What are the main steps in the threat modeling process?
- What exactly is considered PHI according to HIPAA?
- What does the PCI Compliance Auditor Look At?
- How to Detect and Prevent Data Leakage?
- What are the Challenges Associated with Cloud Security Management?
- How Many Techniques Are There in MITRE Att&ck?
- What Are the Benefits of Conducting a Risk Assessment?
- What are the categories of controls in ISO 27001?
- How Does ABAC Differ From Other Access Control Models?
- What Does a Compliance Management System Look Like?
- What Are the NIST CSF Implementation Tiers?
- What is the Purpose of Compliance Attestation?
- How do I become NIST 800-171 compliant?
- Why are the three rules of HIPAA necessary?
- What are the seven categories of risk?
- What are the Six Types of Vulnerability Scanning?
- Which are the most important compliance frameworks?
- How do you implement GRC automation?
- How Can I Measure the ROI of Implementing a Compliance Solution?
- How do you determine whether HIPAA violations need to be reported?
- What are the three major threats to cybersecurity today?
- How Do You Manage Compliance Risk?
- How Does a GRC platform handle data privacy and security?
- How Often Should Supplier Risk Assessments Be Conducted?
- How is a SOC 2 Report Structured?
- What Are the Major Risk Factors in Cyber Security?
- How Do You Read a Risk Matrix Table?
- What is the Risk Rating Matrix Used For?
- What are the Benefits of Risk Assessment Software?
- How does the CMMC differ from NIST?
- Generative AI Governance
- Security Events
In a world full of uncertainties, how do you keep your business risks in check?
Today, we’re exploring risk register templates and how they can supercharge your risk management strategy.

What is a Risk Register?
First things first, let’s define what a risk register is. A risk register is a tool used in risk management and project management. It acts as a centralized repository for all risks identified during the lifecycle of a project or within an organization. Each risk is documented, assessed, and tracked to manage it effectively.
Why Use a Risk Register Template?
Creating a risk register from scratch can be daunting. That’s where templates come in handy. A risk register template simplifies the process, providing a structured format that captures all necessary information. Templates can vary but generally include sections for risk identification, assessment , mitigation strategies, and monitoring.
The Benefits of Using Risk Register Templates
- Consistency : Templates ensure that all risks are documented consistently, making comparing and assessing them easier.
- Efficiency : Using a template saves time. You don’t have to reinvent the wheel whenever you need to create a new risk register.
- Comprehensiveness : A good template prompts you to consider all aspects of each risk, ensuring nothing is overlooked.
- Communication : Templates facilitate the communication of risks to stakeholders by providing a clear and standardized way of presenting information.
Types of Risk Register Templates
Not all risks are created equal, and neither are risk register templates. Different situations call for different templates. In short, there’s no clear-cut “best risk register template”. Let’s explore some types of risk registers out there on the market.
Compliance Risk Register Template These templates identify, assess, and mitigate compliance-related risks in regulatory-heavy industries. They emphasize regulatory risks and compliance requirements.
Cyber Risk Register Template Cyber risk templates, or information security risk register templates focus on managing risks related to information security and cyber threats, helping organizations protect digital assets and respond effectively to incidents. They include cyber risk identification, prioritization , impact assessment, and mitigation strategies.
ERM Risk Register Template ERM templates are agile risk management templates that capture risks across all departments, ensuring a coordinated approach. They facilitate cross-departmental risk identification, strategic alignment, and integrated mitigation plans.
Start Getting Value With Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC system does and eliminates the need for manual processes and spreadsheets to give you immediate value and run a full risk assessment in less than 30 days
Centraleyes Risk Register: A Game Changer in Risk Management
Centraleyes, a SaaS cyber risk management company, has revolutionized the concept of a risk register with its latest release. The Centraleyes risk register offers a fully customizable and automated solution that stands out in the industry.
Key Features of Centraleyes Risk Register
Automated functionality.
Streamlines the process of risk identification, assessment, and management, making it ten times faster and more efficient.
Custom Tagging
Allows security teams to organize and filter risks based on multiple, personalized criteria, enhancing the ability to prioritize and manage risks effectively.
Integration with Other Tools
Directly links gaps and open tasks to risks for better management and strategic planning.
Smart Mapping
Facilitates cross-walking shared compliance and risk controls across multiple standards and frameworks.
Financial Impact Calculation
The platform calculates financial impact under six elements of loss, automatically tagging the risk with a financial attribute, which helps in understanding the economic consequences of each risk.
Components of a Risk Register
A risk register template should include several key components to ensure comprehensive risk management. Here are 11 components you might want to use:
- Risk Identification Number: The first step is recording the risk identification number, which organizes risks into categories and helps track different entries and responses. This can be a simple numerical system or an alphanumeric code, depending on the project’s size and the business’s structure.
- Date of Entry: Recording the date of entry helps future readers understand the timeline of the project risks and the progress made in responses to them.
- Risk Description: This section provides a space to explain the nature of the risk and additional important information. It includes project-related risks such as costs, consumer markets, product or service quality, performance, or technology.
- Likelihood of Occurrence: Assign a score reflecting the likelihood of the risk occurring. This can be a numerical scale (e.g., 1 to 5) or indicators like low, medium, and high.
- Potential Impact of Risk: Describing the potential impact informs how a company can plan to respond. Impacts often affect finances or performance but may involve employees, customers, investors, and other stakeholders.
- Intensity of Risk: Measure the intensity of risk by assessing its likelihood and potential effects. The higher the probability and the more potential impacts, the higher the intensity score.
- Owner of Risk Response: Establish a person responsible for handling the risk plan and leading a response team. Include the owner’s contact information for stakeholder inquiries.
- Preventative Actions: Outline the ways to prevent the risk from occurring. This may involve assuming and accepting risk, transferring risk to insurance companies, or avoiding risk altogether.
- Contingency Plan: Address the effects of a risk if it occurs, focusing on reducing the impact on the project’s progress and team’s work. Contingency plans serve as effective response plans for emergencies.
- Progress Updates: Monitor risks and provide progress updates on the stages and success level of the initial response or contingency plan.
- Risk Status: Mark the risk status with indicators like “open,” “waiting,” “closed,” or “in progress” to show the urgency of the risk.
Why a Cyber Risk Register is Essential
A specialized cyber risk register is crucial for managing the unique risks associated with cybersecurity. Cybersecurity risks span physical, technical, and operational domains, requiring a high level of organization and focus.
- Organized Risk Management: It helps in identifying, analyzing, and mitigating cyber risks efficiently.
- Regulatory Compliance: Ensures the organization meets regulatory requirements, avoiding potential legal and financial penalties.
- Efficiency and Productivity: An organized approach to risk management boosts overall efficiency and productivity, ultimately benefiting the organization financially.
- Proactive Risk Mitigation : Helps in planning and implementing mitigation strategies before risks turn into actual threats.
What to Include in a Cyber Risk Register
A comprehensive cyber risk register should include several detailed components:
- Risk Description: Details of the risk and how it may threaten the organization.
- Impact: The event’s result and effect on the organization.
- Likelihood: The probability of the event occurring, is crucial for prioritizing remediation efforts.
- Outcome: Measures the effect on the organization post-event, helping leaders decide on necessary actions.
- Risk Level: A priority measure based on your risk matrix.
- Cost: Evaluation of the financial implications of mitigation measures.
- Mitigation Actions: Steps to remediate or mitigate the risk, with progress tracking.
- Roles and Responsibilities: Assigns accountability for each risk, maximizing team productivity and efficiency.
Risk Register FAQ’s
Here are some commonly asked questions regarding risk registers.
How do I start creating a risk register?
Starting with a blank slate can be intimidating. Risk register templates provide a structured format that guides you through the process. They ensure you don’t miss any critical steps and help you capture all necessary information systematically.
How do I prioritize risks?
Prioritizing risks can be challenging, especially when dealing with numerous potential threats. Templates often include fields for assessing the likelihood and impact of each risk, helping you rank them effectively. This allows you to focus on the most critical risks first.
How can I ensure my risk register stays updated?
Keeping your risk register current is crucial for effective risk management. Automated tools like the Centraleyes risk register streamline the process of updating risks, ensuring your register reflects the latest information. This reduces manual effort and minimizes the risk of outdated data.
What if my organization has unique risk management needs?
Every organization is different, and a one-size-fits-all approach rarely works. Customizable risk register templates allow you to tailor the fields and structure to match your specific requirements. This flexibility ensures that your risk register is relevant and useful for your organization.
How do I communicate risks to stakeholders?
Clear communication is vital for effective risk management. Standardized templates provide a consistent way to present information, making it easier for stakeholders to understand and act on the data. This enhances collaboration and ensures everyone is on the same page.
Example Risk Register Templates
Here are a few table-based designs of risk register templates to illustrate what I’ve explained in the blog:
Basic Risk Register Template
| Risk ID | Risk Description | Likelihood | Impact | Mitigation Actions | Owner | Status |
| 1 | Data breach due to phishing | High | Severe | Implement anti-phishing training | IT Security Team | Open |
| 2 | Server downtime | Medium | Moderate | Regular maintenance | IT Department | In Progress |
Cyber Risk Register Template
| Risk ID | Risk Description | Impact | Likelihood | Outcome | Mitigation Actions | Cost | Owner | Status |
| 1 | Ransomware attack | High | High | Data loss | Regular backups, anti-malware software | $50,000 | IT Security Team | Open |
| 2 | DDoS attack | Medium | Medium | Service disruption | Implement DDoS protection | $30,000 | Network Team | In Progress |
Compliance Risk Register Template
| 1 | GDPR Article 32 | Unauthorized data access | High | Severe | Encryption, access control | Compliance Officer | Open |
| 2 | HIPAA Security Rule | PHI data breach | Medium | High | Staff training, audit logs | Compliance Officer | In Progress |
Final Word on Risk Registers
Incorporating a risk register into your risk management strategy is crucial for navigating today’s complex risk landscape. Whether you’re managing an agile project, ensuring regulatory compliance , or securing your digital assets, there’s a risk register template that fits your needs.
With advanced tools like Centraleyes’ Automated Cyber Risk Register , you can take your risk management to the next level, ensuring your organization is always prepared to handle whatever comes its way.
Related Content

- All Resources

500 7th Avenue New York, NY 10018
- +1-212-655-3023
- [email protected]
- Internal Risk Management
- Vendor Risk Management
- NIST 800-53
- Partner Resources
- Compliance Automation

Sign up for our Centraleyes Intelligence Report
- Vendor risk management
- Compliance management
- Become a partner
Try the Centraleyes Risk & Compliance
Free for 30 Days
How to Create a Risk Management Plan for Consultants
Table of contents, why is it important for consultants to have a risk management plan, what kinds of risks do consultants face, 1. risk identification, 2. risk analysis, 3. risk evaluation and ranking, 4. risk response, 5. risk monitoring, insurance for consultants.
There’s a relatively common notion that independent consultants spend a lot of their time traveling abroad and doing their work poolside (probably with a pina colada in hand). Sounds like a dream, right? It’s a dream for consultants, too, because it’s far from reality for most.
While that may not reflect the real world for many consultants, there are still plenty of perks to consultancy work. Think: flexible work hours, variety, networking, and, yes, the ability to travel.
But being a consultant also comes with some unique risks that many other professionals don’t encounter. A consultant’s livelihood relies heavily on their client relationships, which could mean financial ruin if those relationships get jeopardized. That’s why every consultant needs to have a risk management plan in place, to successfully tackle the inevitable challenges while also making the most of opportunities for growth and innovation.
With that in mind, we’ve put together this guide with everything you need to create a risk management plan for your consultancy business.
You may be thinking, “Risk management plans are just for large corporations.”
Think again.
Every business has risks and independent consultants are no exception. Whether you provide consulting services in marketing, IT , HR, financial services, graphic design, or even risk management, there are risks that could compromise your success and reputation. That’s why it’s crucial to be proactive and use all the resources at your disposal to minimize and control the impact of potential and real threats.
Because simply ignoring business risks won’t make them go away.
Consultants are brought in as experts in their field, which means that their clients typically have high expectations for their work. What’s more, competition can be fierce for consultants. In fact, the global management consulting services market is expected to grow from $976.3 billion in 2022 to $1,184 billion in 2027 . Having an effective risk management plan goes a long way in helping consultants manage client expectations and stand out from the competition.
No matter what stage your consulting business is at, it’s essential to know the challenges you may face. While threats can vary based on your specific area of work, there are several risks that all consultants, regardless of their industry, must be ready to tackle.
Unhappy Clients: No one can please everyone all the time, and there are plenty of reasons for unhappy clients in the consultancy world. Think: missed deadlines, cost overruns, failure to meet expectations, misrepresentation, and miscommunication. Even with detailed contracts and clear communication, unhappy clients are inevitable. That’s why this risk should be top of mind for all consultants.
Data Breaches: Most consultants store client data on their computers, meaning a data breach could have devastating financial and PR consequences. Considering that the global average cost of a data breach in 2023 was $4.45 million , a 15% increase from three years prior, it’s easy to see why so many businesses don’t survive a data breach or cybercrime. This isn’t a threat any consulting business can afford to overlook.
Unpredictable Markets and Unstable Income: If there’s one thing that’s certain in consulting work, it’s uncertainty. Most consultants are familiar with the feast or famine cycle . It’s easy to get caught up in that cycle, where all of your attention goes to a current client, followed by a period of no work — and no income . The delicate balance of paying attention to existing clients while finding new ones isn’t easy, but it is necessary.
Scope Creep: You know when a client asks for extra work beyond what’s been agreed upon and included in the contract? That’s known as scope creep, and it can be a tricky situation for consultants to deal with. Those just starting their consulting career may be tempted to complete extra requests as a favor to a client. While you may think this is one way to keep them happy and coming back to you, it can lead to problems like missed deadlines, subpar work, and setting an expectation that is hard to maintain.
How to Start a Risk Management Plan for Consultants
Now that you know some of the risks your consulting business may encounter, what can you do about them? Having a risk management plan will help you stay on top of issues that could threaten your business — it may also help you spot opportunities for growth.
Below are the key steps for creating a risk management plan for your consulting business:
Knowing about a risk means you can plan for it. That’s why the first step to take when preparing a risk management plan is to identify all potential threats to your consulting business. Be sure to look at all aspects of your business. Some threats are obvious, while others may take a bit of research to discover.
At this stage, you may find it worthwhile to start a risk register , where you can document information for all identified risks.
Once you’ve identified risks, you can analyze them and determine the potential quantitative and qualitative impact each could have on your business. That means figuring out the likelihood of a risk occurring versus the effect it could have.
This stage is where you ask, “How likely is it that this risk will happen, and what will it take to recover if and when it does happen?” Ranking risks is a vital step as it helps you understand how to prioritize resources to mitigate specific threats. A risk assessment matrix can help you visualize each risk’s likelihood and impact.
Once you’ve ranked the risks, the next step is determining how to respond to each one. This could involve mitigation tactics, such as limiting who has access to sensitive information or transferring the risk to a third party with insurance. For example, if you’re concerned about a data breach, you can transfer the associated risk to your insurance provider with cyber liability insurance .
There is no such thing as “one and done” with risk management. While new risks are inevitable, eliminating one risk could result in another threat popping up. A risk management plan is a living document that needs to be reviewed regularly and updated as required. You don’t want the plan to end up outdated and irrelevant when you need it.
Want more tips on preparing a risk management plan? For a complete breakdown of how to put together an effective risk management plan, check out our detailed guide .
Risk is simply a part of doing business. You can’t have one without the other.
And risks will inevitably change over time; new concerns will emerge as your business grows or a project progresses. So, to successfully grow your consulting business, you have to keep on top of threats that could jeopardize your practice.
One of the most effective ways for consultants to manage risk is by transferring it to a third party, such as your business insurance provider. With coverage like professional liability insurance , your consulting business will be protected from allegations of errors and omissions, while cyber liability insurance will help your firm withstand a data breach.
To learn more about coverage for consultants , read our recent blog post that outlines everything about the insurance policies consultants need .
Related Articles
What is errors and omissions insurance a comprehensive guide for professionals.
In today’s fast-paced business world, mistakes happen. But when those mistakes cost your clients money, you could find yourself in hot water. That’s where errors and omissions (E&O) insurance comes in. If you’re a professional offering services or advice, E&O insurance isn’t just a nice-to-have — it’s a must-have. Let’s answer the question, what is […]
What is Legal Malpractice? And How Can You Protect Your Firm Against It?
If you’re just starting your legal career, you may think that a legal malpractice claim could never happen to you. While that’s hopefully the case, the reality is that the majority of lawyers will face a malpractice claim at some point in their career. According to the American Bar Association (ABA), four out of five […]
Trending Courses
Course Categories
Certification Programs
- Free Courses
Budgeting Resources
- Free Practice Tests
- On Demand Webinars
Published on :
21 Aug, 2024
Blog Author :
Wallstreetmojo Team
Edited by :
Reviewed by :
Dheeraj Vaidya
What is Budgeting?
Budgeting projects anticipated revenue and expenditures for a future period based on prevailing internal and external factors. A detailed statement of projected financial result is prepared by considering inputs from various levels.
It is a health check for the organization—it is essential for avoiding cash crunch or losses. The changes in incomes and expenditures are brought out by labor laws, inflation, market growth, and economic downturns. Budgeting is done by top-level management in the top-down approach; other levels implement it. In the bottom-up approach, inputs from various levels are sent to top management.
Table of contents
Budgeting explained, types of budgeting, #1 - incremental budgeting, #2 - zero-based budgeting (zbb), #3 - activity-based budgeting, #4 - participative budgeting, #5 - negotiated budgeting, #6 - value proposition budgeting, budgeting process, example of budgeting, frequently asked questions (faqs), recommended articles.
- Budgeting is a systematic approach, that predicts revenues and expenditures of an individual, family, group, business entity, or government. A realistic report helps businesses trace their financial performance. This is crucial for decision-making.
- They are classified into personal, corporate, government, static, flexible, master, operating, cash, financial, and labor subtypes.
- Incremental, zero-based , activity-based , participative , negotiated , and value proposition are different methods of budgeting.

Budgeting is done by individuals, families, groups, companies, and the government—to plan, monitor, and control finances. It is everywhere; homemakers use it to manage their monthly expenses and savings; the government relies on it to run the nation.
Anticipated revenue and estimated expenditure are the two crucial components. Anticipated revenue is the potential cash inflow that a person, business entity, or government might generate. On the other hand, estimated expenditure is the cash outflow that an individual, firm, or government expects to make in the upcoming period.
It can be approached top-down or bottom-up. In the top-down approach, top-level management estimates costs and gradually moves down levels. Ultimately, the top management prepares the breakdown of spending and passes it down for implementation. In contrast, in the bottom-up approach, managers prepare department-wise reports based on team inputs and past experiences. They then send it to top management for approval.
Following are different types of budgets prepared by individuals, businesses, and governments.

- Personal Budget : An individual or family plans their monthly earnings and expenses to ensure that they don't run out of cash before the next paycheck.
- Corporate Budget : It is a plan to maintain cash flow, operating cash, and emergency funds efficiently. It comprises sales, material, production, and factory overheads.
- Government Budget : A financial plan prepared by the federal government accounts for the estimated national revenue for a particular financial or fiscal year. The revenue comes from taxes, fees, and grants. It also considers the anticipated expenditure over public services and infrastructure. There are two types of federal budgets—capital and revenue.
- Master Budget : It is a culmination of various lower-level budgets prepared for different areas of business operations. It is a consolidated business plan.
- Operating Budget : It is created at the beginning of a given period. It reflects the profit and loss accounting—accounts for fixed, non-operating, variable, and capital expenditures.
- Static Budget : It is mostly formulated by the government and non-profit organizations. It is rigid and does not allow variations depending on the activity of the institution. It is a prediction of revenue and expenses—based on anticipated values. The actual results may vary from the predicted values.
- Flexible Budget : It is a realistic approach adopted by businesses. A flexible plan considers changes in expenses and costs over the period and adjusts accordingly.
- Financial Budget : It incorporates assets, liabilities, and shareholders equity. It charts a company’s short-term and long-term financial goals.
- Cash Budget : It is simply a cash flow prepared in advance. It documents anticipated payables and receivables for an upcoming period. It is prepared to ensure that the business has enough money to run the organization effortlessly.
- Labor Budget : It is tailor-made for labor-intensive firms. Businesses that are heavily reliant on employees need a systematic plan balancing revenue and wages.
Budgeting Methods
Different methods of preparing financial plans are as follows.
It is a traditional method; the manager takes the previous period's budget as a benchmark. Further, the anticipated percentage change is either summed up or deducted to formulate the current budget. It includes adjustment for inflation, overall market growth, and other relevant factors.
In this method, all the figures are reset to zero, and the manager begins with a fresh interpretation of all the items. The manager has to justify every new number with reasoning, in contrast to using figures from the previous accounting period. ZBB eradicates traditional expenditures that are no longer required. It is a strategic top-down approach re-evaluating every detail and decision.
Operations or activities that generate cost to the business are identified. Ways of reducing costs are strategized. It is mostly used in mature organizations.
Top-level executives often take the help of the managers and workers of different departments in designing the financial plan. It is a bottom-up approach.
It has both top-down and bottom-up traits. Managers and employees together frame the financial plan, keeping in mind goals and targets—set by top-level management.
As the name suggests, every cost is re-evaluated and justified based on its impact. Unnecessary expenses are eliminated.
Given below are the seven steps of financial planning.
- First, ascertain the goal of financial planning.
- Next, interpret and compare historical data of revenues and expenses.
- Then, devise a rough budget to direct the actions towards the objective.
- Further, refine the findings to chalk down a final budget.
- Prepare and submit a budget report.
- Review the financial plan from time to time—detect loopholes.
- Track the performance, taking the necessary corrective measures if required.
The management of ABC Ltd. sets a new target for the sales team to sell 12000 units at a lower price for the year to increase the organization's overall profitability. But the production unit cannot make 12000 units in a year. This could potentially cause frequent clashes between sales and production departments . If inputs from the production unit were considered in financial planning this problem could have been prevented.
On the other hand, if the sales team had achieved the target, sales personnel would expect a raise or incentive for their performance. However, due to lower production, incentives were not delivered. The management may have to spend more on wages without an increase in revenue. This is why companies need master budgets, integrating different departments.
Let us assume Ryan goes to a departmental store and picks a lot of stuff. At the billing counter, he realizes that he does not have enough cash. He ends up unloading items from his cart. This is where financial planning plays a role—saving people from potential embarrassment.
Let us look at some of its other benefits:
- Helps Attain Short and Long-term Goals : The financial planner can prepare for the future by foretelling the revenue and expenditure to achieve the desired objectives effectively.
- Decision-making : Business decisions are not taken blindly; they are based on proper research and planning.
- Avoid Cash Crunch : A person, firm, or government that efficiently plans and executes a financial plan can avoid financial crisis.
Whether it is personal, corporate, or government finance, everything requires planning to actualize short-term or long-term goals. Anticipating revenue and expenditure helps track finances—prevents overspending and depleted emergency funds.
To formulate a financial plan, the manager first needs to define the goal. The next step is gathering and comparing the historical and present data. Then, the future revenue and expenses are predicted—based on the available data. Consequently, a realistic plan is drafted. Ultimately, a comprehensive report is submitted to the top-level executives.
The “50-30-20 ruleu0022 recommends spending 50% of earnings (after-tax) on basic necessities. Of the remainder, the rule recommends spending 30% on leisure and 20% on savings.
This article has been a guide to what is Budgeting and its Meaning. Here we explain budgeting types, methods, processes, examples, and importance. You may learn more about financing from the following articles –
- Top 4 Careers in Budgeting
- Personal Monthly Budget Template
- Types - Accounting Convention
- Fund Accounting Example
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
The 4 Key Strengths of China’s Economy — and What They Mean for Multinational Companies
- Mitch Presnick
- James B. Estes

Companies that fail to understand them risk falling behind.
China’s hybrid “state capitalist” system, driven by centralized planning and fierce competition, has led to dominance in critical technological fields and emerging markets. Western multinational corporations are advised to adopt a pragmatic approach to capitalize on four key strengths of China’s economy: its innovation ecosystem, its investment in the Global South, its ultra-competitive markets, and its vast consumer base. Those who fail to engage risk losing global revenue and strategic opportunities.
In 1978, Deng Xiaoping launched his “Reform and Opening” policy to leverage Western technology and know-how for China’s development. It was a politically risky move: Ideological hardliners in the Communist Party resented the implicit assumption of China’s economic backwardness under socialism — and the superiority of the capitalist West. But Deng recognized that China’s modernization required both pragmatism and humility.
- MP Mitch Presnick is a visiting fellow of practice at the Fairbank Center for Chinese Studies at Harvard University. He is the founder and former chair & CEO of Super 8 Hotels China, the founder and former managing director of the China practice of APCO Worldwide, a Washington D.C. advisory and advocacy firm, and the former vice chair of the American Chamber of Commerce in China.
- JE James B. Estes is a senior at St. Paul’s School, Concord New Hampshire. He is research assistant to visiting fellow of practice Mitch Presnick at the Fairbank Center of Chinese Studies at Harvard University. He is co-founder and project director for educational startup company Reason & Rationality LLC.
Partner Center
Money blog: How to get ridiculously cheap flights - by someone who does it professionally
An employee at Jack's Flight Club has revealed to the Money blog how to find ridiculously cheap flights. Scroll through to read this plus all today's personal finance and consumer news, and this week's Money Problem.
Monday 9 September 2024 17:23, UK
- How to get ridiculously cheap flights - by Jack's Flight Club employee
- 20mph roads would see us lower insurance premiums - esure
- Ministers will not soften blow for pensioners no longer receiving winter fuel payments, Number 10 says
Essential reads
- Fake voucher trend sees supermarket call in police
- How data roaming charges compare by network
- How your pension could be taxed
Tips and advice
- Money Problem : How can I buy a shared property outright?
- Weekly mortgage guide
- Free school meals guide
- Cheapest holidays dates before Xmas
Ask a question or make a comment
Engagement rings can be traced back as far as Ancient Rome - but the modern diamond only came into fashion in the late 1930s.
Now, almost a hundred years on, we are asking - are they still relevant, and how much would you spend on one?
Tell us your stories - do you even have one?
Fill out the comment box above, or you can also send us a message on WhatsApp .
The Body Shop has been rescued from administration in a deal that could save more than a thousand jobs.
The beauty retailer has been acquired by a consortium led by the British cosmetics tycoon Mike Jatania.
It is currently understood there are no immediate plans to shut any of the 113 remaining UK stores.
In a statement, Aurea said the acquisition was its largest transaction to date and it would "steer the Body Shop's revival and reclaim its global leadership in the ethical beauty sector it pioneered".
The Body Shop was founded in 1976 by Dame Anita Roddick. Trading out of a small shop in Brighton, it made its name selling cruelty-free fairtrade products.
But it fell into administration in early February after previous forecasts for how much funding it would need to keep going proved too low. In the weeks that followed, administrators said hundreds of jobs would be lost and dozens of shops closed.
Ministers are not looking to soften the blow for 10 million pensioners who will no longer receive winter fuel payments, the prime minister's spokesman has said.
Ahead of a vote on Tuesday on the controversial decision to limit winter fuel payments to those on pension credit, the government is remaining steadfast despite growing opposition from Labour MPs, unions and charities.
Up until now, all pensioners received the payment to help with higher energy bills over the winter.
Following a cabinet meeting on Monday, Sir Keir Starmer's spokesman was asked if ministers discussed softening the impact for pensioners no longer eligible.
"Not at all," he said.
Read the full story from our politics team here ...
By Tomos Evans , Wales reporter
The average driver could save £50 per year on their car insurance premium if the 20mph speed limit were to be rolled out across the whole of the UK.
Insurance company esure says it would "proactively reduce policy prices" for its customers within three months of identifying a new 20mph zone.
Earlier this year, the company said it had seen a 20% reduction in car accident claims in Wales.
20mph became the default limit in Wales's built-up areas in September last year but was met with significant opposition.
A record-breaking petition on the Senedd's website calling for the policy to be scrapped was signed by more than 500,000 people.
The Welsh government has since updated its guidance for councils to exempt certain roads from the reduced speed limit, in an effort to get "the right speed on the right road".
In May, it was announced the speed limit on almost 4,000 of Glasgow's streets would be reduced to 20mph.
Transport Secretary Louise Haigh has said traffic speeds in England are "entirely up for local areas to decide".
Many parts of England have already changed the default speed limit on their roads.
Primark is losing more money to shoplifters than it spends on rates, its chief executive has said.
The company's billionaire boss, George Weston, said shoplifting had become "socially acceptable... with thieves facing no consequences".
Primark pays around £70m a year in business rates for its UK shops, but Mr Weston says the price of losses from theft now eclipses this.
Business rates are a tax on the occupation of a non-domestic property but have been criticised for allowing online retailers to have an advantage over their bricks-and-mortar counterparts.
He welcomed the home secretary's plans to scrap the £200 rule - which allows thieves to be charged with a summary-only offence if they steal goods worth less than £199.
A summary-only offence is less severe and is tried in a magistrates' court, with the court only able to impose a maximum jail term of up to six months (however, the offence is more likely to result in a community order, according to sentencing guidelines).
Primark has already reported that gloomy summer weather knocked sales by 3.1% - but it has also driven higher sales of autumn fashions, including the company's new collection with singer Rita Ora.
It remains unclear what Labour's first budget next month will mean for pensions - with Chancellor Rachel Reeves refusing to rule out additional taxation.
The lack of detail has created speculation - and so experts at investment bank Saxo have provided us with quick answers to the top 10 most googled questions about pensions...
1. How will I find a lost pension?
If you're looking for a workplace pension, you can contact previous employers and get the information directly from them or many companies offer this service and track them down on your behalf.
The government offers the Pension Tracing Service which, by using your employer's name or your information, can provide you with the details of their workplace pension provider.
2. How much is the state pension?
The current full rate of the UK state pension is £221.20 per week, but this is dependent on how much National Insurance you've paid while working.
To qualify, you'll need to have paid national insurance for 10 full years.
If you're married and both of you have built up 35 qualifying years, this amount doubles to £442.40 a week, or £23,004 a year.
3. When do pensions go up?
The state pension is increased on the first Monday on or after 6 April in line with whatever is highest out of inflation, average wage growth or 2.5%. In April 2024, the annual rise increased by more than 8.5%.
4. How much pension will I receive?
This depends on two main factors - your NI contributions to make sure you receive the full state pension and whether you have a private pension (but there are more factors to consider as well).
This private pension could be a Self-Invested Personal Pension that you've managed, or a workplace pension you and your employer have paid into while working.
Other factors to consider are sector specific pension schemes (teachers' pension, NHS workers, military), how you draw down your pension and the tax implication, and your age.
5. Are pensions subject to inheritance tax?
Usually pensions are exempt from inheritance tax as most schemes are written as trusts, therefore they are valued separately from one's estate and not included in probate calculations - but there are exceptions:
- Continuing guarantee payments may be subject to IHT;
- If a lump sum is paid from a value protected pension, the net of tax amount may be included in the estate;
- If the pension owner died after reaching 75, income tax may be payable.
6. Are pensions tax-free?
It depends on the amount you are withdrawing from your pension, as income from pensions is taxed like any other kind of income. You have a personal allowance (£12,570 for the 2024-25 tax year) which is tax-free.
You then pay 20% tax on income between £12,571 to £50,270 and 40% for any more.
7. How much money can you have in the bank on pension credit?
There is no upper limit on how much money you can have in the bank to receive pension credit, but if you have more than £10,000 in savings and investments, the amount you receive may be reduced.
8. How do I consolidate a pension?
Pension consolidation means combining all (or some) of your pensions into one pot.
If you have several employers over time you are likely going to have workplace pensions in different places. There are advantages and disadvantages to both so it is best to seek advice before combining your pension.
9. How much pension pot do I need for £2,000 per month?
Using a pension calculator, the minimum amount required would be £272,000 for a £24,000 annual drawdown.
However, this doesn't include a lump sum and other factors that will be personal for you. Speak to a professional to receive tailored advice for you.
10. Will Labour tax pensions?
Pensions are already subject to tax. Regardless of how you withdraw your pension, 25% of your total pension pot will be tax-free and you'll pay tax on the rest as if it were income.
Asda workers will stage demonstrations outside the start of an equal pay claim that will assess whether shop floor workers should be paid the same as warehouse staff.
The case (which is expected to last for up to three months) centres on the fact the predominately female retail workforce at the supermarket giant is paid up to £3.74 per hour less than the predominately male warehouse workforce.
Claimants in the case argue both jobs are of equal value to the company.
It is just the latest stage in a 12-year battle over equal pay by Asda retail workers - and if successful, the bill could run into billions of pounds.
Nadine Houghton, GMB National Officer, said: "Asda workers are making history. The result of this hearing will call time on the retailers undervaluing their predominantly women shop floor workers.
"The entire retail sector has been built on the structural undervaluing of women's work - but GMB members are changing this."
It comes as the Employment Tribunal ruled in favour of Next workers in a similar case involving a dispute centred on different rates of pay between job roles.
An Asda spokesperson said: "We fully respect the right of current and former colleagues to bring this case; however, we strongly reject any claim that Asda's pay rates are influenced by gender.
"There are numerous different jobs within retail and within warehouses. We continue to defend these claims because retail and distribution are two different industry sectors that have their own distinct skill sets and pay structures."
By Sarah Taaffe-Maguire , business reporter
German supermarket giant Aldi has repeated its commitment today to opening more stores as it reported record UK sales (this comes despite a falling market share). Pre-tax profits reached £536.7m for the 12 months to December - up from £152.6m a year earlier.
The oil price is just above a more than two-and-a-half-year low at $71.84 (£54.89). It dropped sharply on Friday afternoon amid news of a slowing US economy and weak Chinese demand.
The pound slipped below $1.31 for the first time in nearly a week. This is still high, but anyone who was on holiday in the US last week would have got more bang for their buck. Sterling is doing relatively well against the euro with £1 buying €1.1839.
Following the worst week of 2024, UK stocks have rebounded. The FTSE 100 index of the most valuable companies on the London Stock Exchange rose 0.7% while the FTSE 250 was up 0.34%.
By Megan Harwood-Baynes, cost of living specialist
A £200 flight to the Caribbean sounds almost too good to be true, but for seasoned flight finder Katy Maclure, moments like this are just another (really great) day at the office.
Katy has worked for Jack's Flight Club for almost three years and spends her day researching cheap flights and finding deals - and she's given Sky News some of her best tips.
JFC was started in 2016 by Jack Sheldon. Jack had worked for a large data company but had a knack for finding budget airfares and, after spending time doing this for his friends and family, he decided to turn it into a business - first starting as a newsletter and then a website and company that employs a dozen people.
Katy was one of those. She began as a flight finder and now edits The Detour, the company's weekly travel inspiration.
She says one of the best ways to find a steal is to look at places you might never have thought to go.
"I knew I wanted to go to the Caribbean, and I knew it was expensive - then I saw these cheap flights to Martinique from Paris.
"And Paris is easy to get to, you can just jump on an EasyJet flight or take a train."
So, for just over £200, a train (and the cost of their Airbnb), she and a friend spent two weeks in the overseas French region situated in the eastern Caribbean Sea.
The trick, she says, is going off the beaten track. Last year, she spent £175 on a return trip to Kyrgyzstan and Uzbekistan.
"It's like the Scottish Highlands, but more extreme," she says.
"We stayed in a yurt and it was absolutely phenomenal. It would be amazing for nature lovers - we did a trek into the mountains.
"And it wasn't just nomadic and wild, when we got to Bishkek, it was so modern."
JFC operates a two-tier system for members - you can sign up for free and, each week, a roundup of deals will land in your inbox. If you sign up for their paid tier (which costs around £48 a year) you'll get those emails more frequently.
What's the deal with error fares?
They're the golden goose of airfares, and they are quite literally what they say on the tin - someone made a mistake when putting the price into the system.
Among some great error fares found by JFC was a return flight from Manchester to New York City in the low £200s, and a return to Tanzania from the UK for just £280. That deal was so good that eight of the JFC team booked a trip.
When this happens, the JFC team scramble to get them into subscribers' inboxes as fast as possible, because they can be withdrawn at any time.
Airlines don't have to honour an error fare (they can just refund you), so Katy says it's worth waiting a few weeks before booking any accommodation, just in case - and the rules are slightly different for online travel agencies.
"We've heard many stories of online travelling agencies calling up afterwards or emailing after saying 'oh, sorry, that fare's no longer available, please provide your card details and we'll charge you X amount more'.
"So just be aware that you don't have to pay, that you're not obliged to pay, that you can back out if they try and charge you more."
Katy's top tips for discount travel
1. If you have a specific date and destination in mind, set up alerts on Google flights - you will then get an email when the price changes;
2. Have an idea in mind of what you are willing to pay. If you want a direct flight, it will cost more - as will baggage, so research what these will cost ahead of time to know if you are getting a good deal;
3. Be flexible. If you can't be flexible about the dates, be flexible about the destination.
Jobs data published tomorrow could have a significant impact on the money in your pocket.
As we mentioned in our hello post, the average earnings growth figure published by the ONS is likely to set next year's state pension rise.
The triple lock commits the government to increasing pensions every April by whichever is highest - inflation (the figure for September, published in October), average wage growth between May and July (published tomorrow) or 2.5%.
It is estimated wage growth will come in at around 3.7%, which is very likely to be higher than inflation (currently 2.2%).
This would result in an around-£400 rise to the full state pension in April.
It is sometimes forgotten that, regardless of the political commitment to the triple lock, the government is legally required to raise pensions by at least average earnings growth.
Aside from pensions, tomorrow's jobs market data could also influence the path of interest rates.
Any noticeable shift in the supply-demand dynamic - ie fewer vacancies and more workers looking for jobs - could push down wage growth.
This, in turn, could ease any lasting pressure on inflation.
Gabriel McKeown, head of macroeconomics at Sad Rabbit Investments, told industry news wire Newspage: "With inflation fears still simmering, the forthcoming UK labour market data could be the cold water that extinguishes the Bank of England's hawkish fire.
"The latest projections paint a picture of a cooling labour market, as vacancies have fallen for nine consecutive months, while the availability of workers has increased.
"This shift in the supply-demand balance has begun to exert downward pressure on wage inflation, suggesting a trajectory towards target.
"Consequently, Tuesday's labour data is critical for the BoE's monetary policy decisions.
"A September cut seems unlikely, with the Bank's Monetary Policy Committee wanting more evidence of sustained cooling in the labour market and a further moderation in wage growth.
"However, a higher-than-expected unemployment rate or a sharper wage growth decline could tilt the MPC towards a more dovish stance."
Be the first to get Breaking News
Install the Sky News app for free

The University of Chicago The Law School
Innovation clinic—significant achievements for 2023-24.
The Innovation Clinic continued its track record of success during the 2023-2024 school year, facing unprecedented demand for our pro bono services as our reputation for providing high caliber transactional and regulatory representation spread. The overwhelming number of assistance requests we received from the University of Chicago, City of Chicago, and even national startup and venture capital communities enabled our students to cherry-pick the most interesting, pedagogically valuable assignments offered to them. Our focus on serving startups, rather than all small- to medium-sized businesses, and our specialization in the needs and considerations that these companies have, which differ substantially from the needs of more traditional small businesses, has proven to be a strong differentiator for the program both in terms of business development and prospective and current student interest, as has our further focus on tackling idiosyncratic, complex regulatory challenges for first-of-their kind startups. We are also beginning to enjoy more long-term relationships with clients who repeatedly engage us for multiple projects over the course of a year or more as their legal needs develop.
This year’s twelve students completed over twenty projects and represented clients in a very broad range of industries: mental health and wellbeing, content creation, medical education, biotech and drug discovery, chemistry, food and beverage, art, personal finance, renewable energy, fintech, consumer products and services, artificial intelligence (“AI”), and others. The matters that the students handled gave them an unparalleled view into the emerging companies and venture capital space, at a level of complexity and agency that most junior lawyers will not experience until several years into their careers.
Representative Engagements
While the Innovation Clinic’s engagements are highly confidential and cannot be described in detail, a high-level description of a representative sample of projects undertaken by the Innovation Clinic this year includes:
Transactional/Commercial Work
- A previous client developing a symptom-tracking wellness app for chronic disease sufferers engaged the Innovation Clinic again, this time to restructure its cap table by moving one founder’s interest in the company to a foreign holding company and subjecting the holding company to appropriate protections in favor of the startup.
- Another client with whom the Innovation Clinic had already worked several times engaged us for several new projects, including (1) restructuring their cap table and issuing equity to an additional, new founder, (2) drafting several different forms of license agreements that the company could use when generating content for the platform, covering situations in which the company would license existing content from other providers, jointly develop new content together with contractors or specialists that would then be jointly owned by all creators, or commission contractors to make content solely owned by the company, (3) drafting simple agreements for future equity (“Safes”) for the company to use in its seed stage fundraising round, and (4) drafting terms of service and a privacy policy for the platform.
- Yet another repeat client, an internet platform that supports independent artists by creating short films featuring the artists to promote their work and facilitates sales of the artists’ art through its platform, retained us this year to draft a form of independent contractor agreement that could be used when the company hires artists to be featured in content that the company’s Fortune 500 brand partners commission from the company, and to create capsule art collections that could be sold by these Fortune 500 brand partners in conjunction with the content promotion.
- We worked with a platform using AI to accelerate the Investigational New Drug (IND) approval and application process to draft a form of license agreement for use with its customers and an NDA for prospective investors.
- A novel personal finance platform for young, high-earning individuals engaged the Innovation Clinic to form an entity for the platform, including helping the founders to negotiate a deal among them with respect to roles and equity, terms that the equity would be subject to, and other post-incorporation matters, as well as to draft terms of service and a privacy policy for the platform.
- Students also formed an entity for a biotech therapeutics company founded by University of Chicago faculty members and an AI-powered legal billing management platform founded by University of Chicago students.
- A founder the Innovation Clinic had represented in connection with one venture engaged us on behalf of his other venture team to draft an equity incentive plan for the company as well as other required implementing documentation. His venture with which we previously worked also engaged us this year to draft Safes to be used with over twenty investors in a seed financing round.
More information regarding other types of transactional projects that we typically take on can be found here .
Regulatory Research and Advice
- A team of Innovation Clinic students invested a substantial portion of our regulatory time this year performing highly detailed and complicated research into public utilities laws of several states to advise a groundbreaking renewable energy technology company as to how its product might be regulated in these states and its clearest path to market. This project involved a review of not only the relevant state statutes but also an analysis of the interplay between state and federal statutes as it relates to public utilities law, the administrative codes of the relevant state executive branch agencies, and binding and non-binding administrative orders, decisions and guidance from such agencies in other contexts that could shed light on how such states would regulate this never-before-seen product that their laws clearly never contemplated could exist. The highly varied approach to utilities regulation in all states examined led to a nuanced set of analysis and recommendations for the client.
- In another significant research project, a separate team of Innovation Clinic students undertook a comprehensive review of all settlement orders and court decisions related to actions brought by the Consumer Financial Protection Bureau for violations of the prohibition on unfair, deceptive, or abusive acts and practices under the Consumer Financial Protection Act, as well as selected relevant settlement orders, court decisions, and other formal and informal guidance documents related to actions brought by the Federal Trade Commission for violations of the prohibition on unfair or deceptive acts or practices under Section 5 of the Federal Trade Commission Act, to assemble a playbook for a fintech company regarding compliance. This playbook, which distilled very complicated, voluminous legal decisions and concepts into a series of bullet points with clear, easy-to-follow rules and best practices, designed to be distributed to non-lawyers in many different facets of this business, covered all aspects of operations that could subject a company like this one to liability under the laws examined, including with respect to asset purchase transactions, marketing and consumer onboarding, usage of certain terms of art in advertising, disclosure requirements, fee structures, communications with customers, legal documentation requirements, customer service and support, debt collection practices, arrangements with third parties who act on the company’s behalf, and more.
Miscellaneous
- Last year’s students built upon the Innovation Clinic’s progress in shaping the rules promulgated by the Financial Crimes Enforcement Network (“FinCEN”) pursuant to the Corporate Transparency Act to create a client alert summarizing the final rule, its impact on startups, and what startups need to know in order to comply. When FinCEN issued additional guidance with respect to that final rule and changed portions of the final rule including timelines for compliance, this year’s students updated the alert, then distributed it to current and former clients to notify them of the need to comply. The final bulletin is available here .
- In furtherance of that work, additional Innovation Clinic students this year analyzed the impact of the final rule not just on the Innovation Clinic’s clients but also its impact on the Innovation Clinic, and how the Innovation Clinic should change its practices to ensure compliance and minimize risk to the Innovation Clinic. This also involved putting together a comprehensive filing guide for companies that are ready to file their certificates of incorporation to show them procedurally how to do so and explain the choices they must make during the filing process, so that the Innovation Clinic would not be involved in directing or controlling the filings and thus would not be considered a “company applicant” on any client’s Corporate Transparency Act filings with FinCEN.
- The Innovation Clinic also began producing thought leadership pieces regarding AI, leveraging our distinct and uniquely University of Chicago expertise in structuring early-stage companies and analyzing complex regulatory issues with a law and economics lens to add our voice to those speaking on this important topic. One student wrote about whether non-profits are really the most desirable form of entity for mitigating risks associated with AI development, and another team of students prepared an analysis of the EU’s AI Act, comparing it to the Executive Order on AI from President Biden, and recommended a path forward for an AI regulatory environment in the United States. Both pieces can be found here , with more to come!
Innovation Trek
Thanks to another generous gift from Douglas Clark, ’89, and managing partner of Wilson, Sonsini, Goodrich & Rosati, we were able to operationalize the second Innovation Trek over Spring Break 2024. The Innovation Trek provides University of Chicago Law School students with a rare opportunity to explore the innovation and venture capital ecosystem in its epicenter, Silicon Valley. The program enables participating students to learn from business and legal experts in a variety of different industries and roles within the ecosystem to see how the law and economics principles that students learn about in the classroom play out in the real world, and facilitates meaningful connections between alumni, students, and other speakers who are leaders in their fields. This year, we took twenty-three students (as opposed to twelve during the first Trek) and expanded the offering to include not just Innovation Clinic students but also interested students from our JD/MBA Program and Doctoroff Business Leadership Program. We also enjoyed four jam-packed days in Silicon Valley, expanding the trip from the two and a half days that we spent in the Bay Area during our 2022 Trek.
The substantive sessions of the Trek were varied and impactful, and enabled in no small part thanks to substantial contributions from numerous alumni of the Law School. Students were fortunate to visit Coinbase’s Mountain View headquarters to learn from legal leaders at the company on all things Coinbase, crypto, and in-house, Plug & Play Tech Center’s Sunnyvale location to learn more about its investment thesis and accelerator programming, and Google’s Moonshot Factory, X, where we heard from lawyers at a number of different Alphabet companies about their lives as in-house counsel and the varied roles that in-house lawyers can have. We were also hosted by Wilson, Sonsini, Goodrich & Rosati and Fenwick & West LLP where we held sessions featuring lawyers from those firms, alumni from within and outside of those firms, and non-lawyer industry experts on topics such as artificial intelligence, climate tech and renewables, intellectual property, biotech, investing in Silicon Valley, and growth stage companies, and general advice on career trajectories and strategies. We further held a young alumni roundtable, where our students got to speak with alumni who graduated in the past five years for intimate, candid discussions about life as junior associates. In total, our students heard from more than forty speakers, including over twenty University of Chicago alumni from various divisions.
The Trek didn’t stop with education, though. Throughout the week students also had the opportunity to network with speakers to learn more from them outside the confines of panel presentations and to grow their networks. We had a networking dinner with Kirkland & Ellis, a closing dinner with all Trek participants, and for the first time hosted an event for admitted students, Trek participants, and alumni to come together to share experiences and recruit the next generation of Law School students. Several speakers and students stayed in touch following the Trek, and this resulted not just in meaningful relationships but also in employment for some students who attended.
More information on the purposes of the Trek is available here , the full itinerary is available here , and one student participant’s story describing her reflections on and descriptions of her experience on the Trek is available here .
The Innovation Clinic is grateful to all of its clients for continuing to provide its students with challenging, high-quality legal work, and to the many alumni who engage with us for providing an irreplaceable client pipeline and for sharing their time and energy with our students. Our clients are breaking the mold and bringing innovations to market that will improve the lives of people around the world in numerous ways. We are glad to aid in their success in any way that we can. We look forward to another productive year in 2024-2025!

COMMENTS
1) Economic Risks. Failure to acquire adequate funding for your business can damage the chances of your business succeeding. Before a new business starts making profits, it needs to be kept afloat with money. Bills will pile up, suppliers will need payments, and your employees will be expecting their salaries.
10 Types of Business Risks and How to Manage Them
What is business risk?
13 Types of Business Risks for Companies to Manage
Outsource. 24. Loss of key skills. Use employee incentive or bonus schemes. Check pay reflects industry (going rate) Identify top performers and reward/offer incentives to stay. Remove hygiene factors e.g. poor parking, lack of flexible working. 25. Loss of political support.
What Is Business Risk? Definition, Factors, and Examples
Risk Mitigation Strategies: Types & Examples (+ Free ...
Types of Business Risks and Ideas for Managing Them
Identifying and Managing Business Risks
How to Highlight Risks in Your Business Plan
A business risk assessment matrix, sometimes called a probability and impact matrix, is a tool you can use to assess and prioritize different types of risks based on their likelihood (probability) and potential damage (impact). Here's a step-by-step process to create one: Step 1: Begin by listing out your risks.
How To Create A Risk Management Plan + Template & ...
A Guide to Risk Analysis: Example & Methods
Managing Risks: A New Framework
After the hottest summer on record in the Northern Hemisphere in 2023, 66% of those surveyed saw extreme weather as the biggest risk for 2024 and could get worse: Expected global economic losses by 2060 could be US$24.7 trillion due to weather-related losses. 2. Security and cyber incident risks. In today's digital landscape, security and ...
The risks and mitigants subsection is at the end of the strategy section of your business plan, at which point the reader has a fairly clear idea of what your business does, what market you operate in and what your strategy to conquer that market is. When writing this section, it's important to be transparent.
Business risks | business.gov.au ... Business risks
Physical risk. Physical risks include dangers that pose a threat to physical assets, including your buildings, equipment and people. Risks could be events such as fire, flooding, or crimes like theft and vandalism. Physical damage can present a risk to your business in a number of ways, from time lost and repair costs, to legal action and ...
What Is Business Risk?
How to Make a Risk Management Plan (Template Included)
There may be benefits of having business leaders articulate risk considerations as part of their development of a business plan or budget request. This tool identifies questions that an organization might embed in its instructions that are provided to business unit leaders as they develop a strategic plan or budget request for their business unit.
Dig deep and understand the cash requirements you will need to reach the break-even point. Lack of capital is the No. 1 cause of business failure. Don't even consider starting a business until you truly know the capital needs of the business and know that you have the means to get there.
Types of Risk Register Templates. Not all risks are created equal, and neither are risk register templates. ... This can be a simple numerical system or an alphanumeric code, depending on the project's size and the business's structure. ... Establish a person responsible for handling the risk plan and leading a response team. Include the ...
Below are the key steps for creating a risk management plan for your consulting business: 1. Risk Identification. Knowing about a risk means you can plan for it. That's why the first step to take when preparing a risk management plan is to identify all potential threats to your consulting business. Be sure to look at all aspects of your business.
Budgeting - Meaning, Process, Example, Types and Methods
China's hybrid "state capitalist" system, driven by centralized planning and fierce competition, has led to dominance in critical technological fields and emerging markets. Western ...
House prices have hit a two-year high after jumping 0.3% in August, the latest data from Halifax has shown. Scroll through the Money blog for this plus more personal finance and consumer posts ...
General The Innovation Clinic continued its track record of success during the 2023-2024 school year, facing unprecedented demand for our pro bono services as our reputation for providing high caliber transactional and regulatory representation spread. The overwhelming number of assistance requests we received from the University of Chicago, City of Chicago, and even national startup and ...