- Talk to Expert
- Machine Identity Management
- October 20, 2023
- 9 minute read

7 Data Breach Examples Involving Human Error: Did Encryption Play a Role?

Despite an overall increase in security investment over the past decade, organizations are still plagued by data breaches. What’s more, we’re learning that many of the attacks that result in breaches misuse encryption in some way. (By comparison, just four percent of data breaches tracked by Gemalto’s Breach Level Index were “secure breaches” in that the use of encryption rendered stolen data useless). Sadly, it’s often human error that allows attackers access to encrypted channels and sensitive information. Sure, an attacker can leverage “gifts” such as zero-day vulnerabilities to break into a system, but in most cases, their success involves provoking or capitalizing on human error.
Human error has a well-documented history of causing data breaches. The 2022 Global Risks Report released by the World Economic Forum, found that 95% of cybersecurity threats were in some way caused by human error. Meanwhile, the 2022 Data Breach Investigations Report (DBIR) found that 82% of breaches involved the human element, including social attacks, errors and misuse.
I think it’s interesting to look at case studies on how human error has contributed to a variety of data breaches, some more notorious than others. I’ll share the publicly known causes and impacts of these breaches. But I’d also like to highlight how the misuse of encryption often compounds the effects of human error in each type of breach.

SolarWinds: Anatomy of a Supersonic Supply Chain Attack
Data breach examples.
Here is a brief review of seven well-known data breaches caused by human error.
1. Equifax data breach—Expired certificates delayed breach detection
In the spring of 2017, the U.S. Department of Homeland Security's Computer Emergency Readiness Team (CERT) sent consumer credit reporting agency Equifax a notice about a vulnerability affecting certain versions of Apache Struts. According to former CEO Richard Smith, Equifax sent out a mass internal email about the flaw. The company’s IT security team should have used this email to fix the vulnerability, according to Smith’s testimony before the House Energy and Commerce Committee. But that didn’t happen. An automatic scan several days later also failed to identify the vulnerable version of Apache Struts. Plus, the device inspecting encrypted traffic was misconfigured because of a digital certificate that had expired ten months previously. Together, these oversights enabled a digital attacker to crack into Equifax’s system in mid-May and maintain their access until the end of July.
How encryption may become a factor in scenarios like this: Once attackers have access to a network, they can install rogue or stolen certificates that allow them to hide exfiltration in encrypted traffic. Unless HTTPS inspection solutions are available and have full access to all keys and certificates, rogue certificates will remain undetected.
Impact: The bad actor is thought to have exposed the personal information of 145 million people in the United States and more than 10 million UK citizens. In September 2018, the Information Commissioner’s Office issued Equifax a fine of £500,000, the maximum penalty amount allowed under the Data Protection Act 1998, for failing to protect the personal information of up to 15 million UK citizens during the data breach.
2. Ericsson data breach—Mobile services go dark when the certificate expires
At the beginning of December 2018, a digital certificate used by Swedish multinational networking and telecommunications company Ericsson for its SGSN–MME (Serving GPRS Support Node—Mobility Management Entity) software expired. This incident caused outages for customers of various UK mobile carriers including O2, GiffGaff, and Lyca Mobile. As a result, a total of 32 million people in the United Kingdom alone lost access to 4G and SMS on 6 December. Beyond the United Kingdom, the outage reached 11 countries including Japan.
How encryption may become a factor in scenarios like this: Expired certificates do not only cause high-impact downtime; they can also leave critical systems without protection. If a security system experiences a certificate outage , cybercriminals can take advantage of the temporary lack of availability to bypass the safeguards.
Impact: Ericsson restored the most affected customer services over the course of 6 December. The company also noted in a blog post that “The faulty software [for two versions of SGSN–MME] that has caused these issues is being decommissioned.”
3. LinkedIn data breach—Millions miss connections when the certificate expires
On 30 November, a certificate used by business social networking giant LinkedIn for its country subdomains expired. As reported by The Register , the incident did not affect www.linkedin.com, as LinkedIn uses a separate certificate for that particular domain. But the event, which involved a certificate issued by DigiCert SHA2 Secure Server CA, did invalidate us.linkedin.com along with the social media giant’s other subdomains. As a result, millions of users were unable to log into LinkedIn for several hours.
How encryption may become a factor in scenarios like this: Whenever certificates expire, it may indicate that overall protection for machine identities is not up to par. Uncontrolled certificates are a prime target for cybercriminals who can use them to impersonate the company or gain illicit access.
Impact: Later in the afternoon on 30 November, LinkedIn deployed a new certificate that helped bring its subdomains back online, thereby restoring all users’ access to the site.
4. Strathmore College data breach—Student records not adequately protected
In August 2018, it appears that an employee at Strathmore secondary college accidentally published more than 300 students’ records on the school’s intranet. These records included students' medical and mental health conditions such as Asperger’s, autism and ADHD. According to The Guardian , they also listed the exposed students’ medications along with any learning and behavioral difficulties. Overall, the records remained on Strathmore’s intranet for about a day. During that time, students and parents could have viewed and/or downloaded the information.
How encryption may become a factor in scenarios like this: Encrypting access to student records makes it difficult for anyone who doesn’t have the proper credentials to access them. Any information left unprotected by encryption can be accessed by any cybercriminals who penetrate your perimeter.
Impact: Strathmore’s principal said he had arranged professional development training for his staff to ensure they’re following best security practices. Meanwhile, Australia’s Department of Education announced that it would investigate what had caused the breach.
5. Veeam data breach—Customer records compromised by unprotected database
Near the end of August 2018, the Shodan search engine indexed an Amazon-hosted IP. Bob Diachenko, director of cyber risk research at Hacken.io, came across the IP on 5 September and quickly determined that the IP resolved to a database left unprotected by the lack of a password. The exposed database contained 200 gigabytes worth of data belonging to Veeam, a backup and data recovery company. Among that data were customer records including names, email addresses and some IP addresses.
How encryption may become a factor in scenarios like this: Usernames and passwords are a relatively weak way of securing private access. Plus, if an organization does not maintain complete control of the private keys that govern access for internal systems, attackers have a better chance of gaining access.
Impact: Within three hours of learning about the exposure, Veeam took the server offline. The company also reassured TechCrunch that it would “conduct a deeper investigation and… take appropriate actions based on our findings.”
6. Marine Corps data breach—Unencrypted email misfires
At the beginning of 2018, the Defense Travel System (DTS) of the United States Department of Defense (DOD) sent out an unencrypted email with an attachment to the wrong distribution list. The email, which the DTS sent within the usmc.mil official unclassified Marine domain but also to some civilian accounts, exposed the personal information of approximately 21,500 Marines, sailors and civilians. Per Marine Corp Times , the data included victims’ bank account numbers, truncated Social Security Numbers and emergency contact information.
How encryption may become a factor in scenarios like this: If organizations are not using proper encryption, cybercriminals can insert themselves between two email servers to intercept and read the email. Sending private personal identity information over unencrypted channels essentially becomes an open invitation to cybercriminals.
Impact: Upon learning of the breach, the Marines implemented email recall procedures to limit the number of email accounts that would receive the email. They also expressed their intention to implement additional security measures going forward.
7. Pennsylvania Department of Education data breach—Misassigned permissions
In February 2018, an employee in Pennsylvania’s Office of Administration committed an error that subsequently affected the state’s Teacher Information Management System (TIMS). As reported by PennLive , the incident temporarily enabled individuals who logged into TIMS to access personal information belonging to other users including teachers, school districts and Department of Education staff. In all, the security event is believed to have affected as many as 360,000 current and retired teachers.
How encryption may become a factor in scenarios like this: I f you do not know who’s accessing your organization’s information, then you’ll never know if it’s being accessed by cybercriminals. Encrypting access to vital information and carefully managing the identities of the machines that house it will help you control access.
Impact: Pennsylvania’s Department of Education subsequently sent out notice letters informing victims that the incident might have exposed their personal information including their Social Security Numbers. It also offered a free one-year subscription for credit monitoring and identity protection services to affected individuals.
How machine identities are misused in a data breach
Human error can impact the success of even the strongest security strategies. As the above attacks illustrate, this can compromise the security of machine identities in numerous ways. Here are just a few:
- SSH keys grant privileged access to many internal systems. Often, these keys do not have expiration dates. And they are difficult to monitor. So, if SSH keys are revealed or compromised, attackers can use them to pivot freely within the network.
- Many phishing attacks leverage wildcard or rogue certificates to create fake sites that appear to be authentic. Such increased sophistication is often required to target higher-level executives.
- Using public-key encryption and authentication in the two-step verification makes it harder to gain malicious access. Easy access to SSH keys stored on computers or servers makes it easier for attackers to pivot laterally within the organization.
- An organization’s encryption is only as good as that of its entire vendor community. If organizations don’t control the keys and certificates that authenticate partner interactions, then they lose control of the encrypted tunnels that carry confidential information between companies.
- If organizations are not monitoring the use of all the keys and certificates that are used in encryption, then attackers can use rogue or stolen keys to create illegitimate encrypted tunnels. Organizations will not be able to detect these malicious tunnels because they appear to be the same as other legitimate tunnels into and out of the organization.
How to avoid data breaches
The best way to avoid a data breach to make sure your organization is using the most effective, up-to-date security tools and technologies. But even the best cybersecurity strategy is not complete unless it is accompanied by security awareness training for all who access and interact with sensitive corporate data.
Because data breaches take many different forms and can happen in a multitude of ways, you need to be ever vigilant and employ a variety of strategies to protect your organization. These should include regular patching and updating of software, encrypting sensitive data, upgrading obsolete machines and enforcing strong credentials and multi-factor authentication.
In particular, a zero-trust architecture will give control and visibility over your users and machines using strategies such as least privileged access, policy enforcement, and strong encryption. Protecting your machine identities as part of your zero trust architecture will take you a long way toward breach prevention. Here are some machine identity management best practices that you should consider:
- Locate all your machine identities. Having a complete list of your machine identities and knowing where they’re all installed, who owns them, and how they’re used will give you the visibility you need to ensure that they are not being misused in an attack.
- Set up and enforce security policies. To keep your machine identities safe, you need security policies that help you control every aspect of machine identities — issuance, use, ownership, management, security, and decommissioning.
- Continuously gather machine identity intelligence. Because the number of machines on your network is constantly changing, you need to maintain intelligence their identities, including the conditions of their use and their environment.
- Automate the machine identity life cycle. Automating he management of certificate requests, issuance, installation, renewals, and replacements helps you avoid error-prone manual actions that may leave your machine identities vulnerable to outage or breach.
- Monitor for anomalous use. After you’ve established a baseline of normal machine identity usage, you can start monitoring and flagging anomalous behavior, which can indicate a machine identity compromise.
- Set up notifications and alerts. Finding and evaluating potential machine identity issues before they exposures is critical. This will help you take immediate action before attackers can take advantage of weak or unprotected machine identities.
- Remediate machine identities that don’t conform to policy. When you discover machine identities that are noncompliant, you must quickly respond to any security incident that requires bulk remediation.
Training your users about the importance of machine identities will help reduce user errors. And advances in AI and RPA will also play a factor in the future. But for now, your best bet in preventing encryption from being misused in an attack on your organization is an automated machine identity management solution that allows you to maintain full visibility and control of your machine identities. Automation will help you reduce the inherent risks of human error as well as maintain greater control over how you enforce security policies for all encrypted communications.
( This post has been updated. It was originally published Posted on October 15, 2020. )
Related posts
- Marriott Data Breach: 500 Million Reasons Why It’s Critical to Protect Machine Identities
- Breaches Are Like Spilled Milk: It Doesn’t Help to Cry
- The Major Data Breaches of 2017: Did Machine Identities Play a Factor?

Machine Identity Security Summit 2024
Help us forge a new era of cybersecurity
☕ We're spilling all the machine identiTEA Oct. 1-3, but these insights are too valuable to just toss in the harbor! Browse the agenda and register now.
- Data Breach
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

The 15 biggest data breaches of the 21st century
Data breaches affecting millions of users are far too common. here are some of the biggest, baddest breaches in recent memory..

In today’s data-driven world, data breaches can affect hundreds of millions or even billions of people at a time. Digital transformation has increased the supply of data moving, and data breaches have scaled up with it as attackers exploit the data-dependencies of daily life. How large cyberattacks of the future might become remains speculation, but as this list of the biggest data breaches of the 21 st Century indicates, they have already reached enormous magnitudes.
For transparency, this list has been calculated by the number of users impacted, records exposed, or accounts affected. We have also made a distinction between incidents where data was actively stolen or reposted maliciously and those where an organization has inadvertently left data unprotected and exposed, but there has been no significant evidence of misuse. The latter have purposefully not been included in the list.
So, here it is – an up-to-date list of the 15 biggest data breaches in recent history, including details of those affected, who was responsible, and how the companies responded (as of July 2021).
Date: August 2013 Impact: 3 billion accounts
Securing the number one spot – almost seven years after the initial breach and four since the true number of records exposed was revealed – is the attack on Yahoo. The company first publicly announced the incident – which it said took place in 2013 – in December 2016. At the time, it was in the process of being acquired by Verizon and estimated that account information of more than a billion of its customers had been accessed by a hacking group. Less than a year later, Yahoo announced that the actual figure of user accounts exposed was 3 billion. Yahoo stated that the revised estimate did not represent a new “security issue” and that it was sending emails to all the “additional affected user accounts.”
Despite the attack, the deal with Verizon was completed, albeit at a reduced price. Verizon’s CISO Chandra McMahon said at the time: “Verizon is committed to the highest standards of accountability and transparency, and we proactively work to ensure the safety and security of our users and networks in an evolving landscape of online threats. Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon’s experience and resources.” After investigation, it was discovered that, while the attackers accessed account information such as security questions and answers, plaintext passwords, payment card and bank data were not stolen.
2. Aadhaar [tie with Alibaba]
Date: January 2018 Impact: 1.1 billion Indian citizens’ identity/biometric information exposed
In early 2018, news broke that malicious actors has infiltrated the world’s largest ID database, Aadhaar , exposing information on more than 1.1 billion Indian citizens including names, addresses, photos, phone numbers, and emails, as well as biometric data like fingerprints and iris scans. What’s more, since the database – established by the Unique Identification Authority of India (UIDAI) in 2009 – also held information about bank accounts connected with unique 12-digit numbers, it became a credit breach too. This was despite the UIDAI initially denying that the database held such data
The actors infiltrated the Aadhaar database through the website of Indane, a state-owned utility company connected to the government database through an application programming interface that allowed applications to retrieve data stored by other applications or software. Unfortunately, Indane’s API had no access controls, thus rendering its data vulnerable. Hackers sold access to the data for as little as $7 via a WhatsApp group. Despite warnings from security researchers and tech groups, it took Indian authorities until March 23, 2018, to take the vulnerable access point offline.
2. Alibaba [tie with Aadhaar]
Date: November 2019 Impact: 1.1 billion pieces of user data
Over an eight-month period, a developer working for an affiliate marketer scraped customer data, including usernames and mobile numbers, from the Alibaba Chinese shopping website, Taobao, using crawler software that he created. It appears the developer and his employer were collecting the information for their own use and did not sell it on the black market, although both were sentenced to three years in prison.
A Taobao spokesperson said in a statement : “Taobao devotes substantial resources to combat unauthorized scraping on our platform, as data privacy and security is of utmost importance. We have proactively discovered and addressed this unauthorized scraping. We will continue to work with law enforcement to defend and protect the interests of our users and partners.”
4. LinkedIn
Date: June 2021 Impact: 700 million users
Professional networking giant LinkedIn saw data associated with 700 million of its users posted on a dark web forum in June 2021, impacting more than 90% of its user base. A hacker going by the moniker of “God User” used data scraping techniques by exploiting the site’s (and others’) API before dumping a first information data set of around 500 million customers. They then followed up with a boast that they were selling the full 700 million customer database. While LinkedIn argued that as no sensitive, private personal data was exposed, the incident was a violation of its terms of service rather than a data breach, a scraped data sample posted by God User contained information including email addresses, phone numbers, geolocation records, genders and other social media details, which would give malicious actors plenty of data to craft convincing, follow-on social engineering attacks in the wake of the leak, as warned by the UK’s NCSC .
5. Sina Weibo
Date: March 2020 Impact: 538 million accounts
With over 600 million users, Sina Weibo is one of China’s largest social media platforms. In March 2020, the company announced that an attacker obtained part of its database, impacting 538 million Weibo users and their personal details including real names, site usernames, gender, location, and phone numbers. The attacker is reported to have then sold the database on the dark web for $250.
China’s Ministry of Industry and Information Technology (MIIT) ordered Weibo to enhance its data security measures to better protect personal information and to notify users and authorities when data security incidents occur. In a statement , Sina Weibo argued that an attacker had gathered publicly posted information by using a service meant to help users locate the Weibo accounts of friends by inputting their phone numbers and that no passwords were affected. However, it admitted that the exposed data could be used to associate accounts to passwords if passwords are reused on other accounts. The company said it strengthened its security strategy and reported the details to the appropriate authority.
6. Facebook
Date: April 2019 Impact: 533 million users
In April 2019, it was revealed that two datasets from Facebook apps had been exposed to the public internet. The information related to more than 530 million Facebook users and included phone numbers, account names, and Facebook IDs. However, two years later (April 2021) the data was posted for free, indicating new and real criminal intent surrounding the data. In fact, given the sheer number of phone numbers impacted and readily available on the dark web as a result of the incident, security researcher Troy Hunt added functionality to his HaveIBeenPwned (HIBP) breached credential checking site that would allow users to verify if their phone numbers had been included in the exposed dataset.
“I’d never planned to make phone numbers searchable,” Hunt wrote in blog post . “My position on this was that it didn’t make sense for a bunch of reasons. The Facebook data changed all that. There’s over 500 million phone numbers but only a few million email addresses so >99% of people were getting a miss when they should have gotten a hit.”
7. Marriott International (Starwood)
Date: September 2018 Impact: 500 million customers
Hotel Marriot International announced the exposure of sensitive details belonging to half a million Starwood guests following an attack on its systems in September 2018. In a statement published in November the same year, the hotel giant said: “On September 8, 2018, Marriott received an alert from an internal security tool regarding an attempt to access the Starwood guest reservation database. Marriott quickly engaged leading security experts to help determine what occurred.”
Marriott learned during the investigation that there had been unauthorized access to the Starwood network since 2014. “Marriott recently discovered that an unauthorized party had copied and encrypted information and took steps towards removing it. On November 19, 2018, Marriott was able to decrypt the information and determined that the contents were from the Starwood guest reservation database,” the statement added.
The data copied included guests’ names, mailing addresses, phone numbers, email addresses, passport numbers, Starwood Preferred Guest account information, dates of birth, gender, arrival and departure information, reservation dates, and communication preferences. For some, the information also included payment card numbers and expiration dates, though these were apparently encrypted.
Marriot carried out an investigation assisted by security experts following the breach and announced plans to phase out Starwood systems and accelerate security enhancements to its network. The company was eventually fined £18.4 million (reduced from £99 million) by UK data governing body the Information Commissioner’s Office (ICO) in 2020 for failing to keep customers’ personal data secure. An article by New York Times attributed the attack to a Chinese intelligence group seeking to gather data on US citizens.
Date: 2014 Impact: 500 million accounts
Making its second appearance in this list is Yahoo, which suffered an attack in 2014 separate to the one in 2013 cited above. On this occasion, state-sponsored actors stole data from 500 million accounts including names, email addresses, phone numbers, hashed passwords, and dates of birth. The company took initial remedial steps back in 2014, but it wasn’t until 2016 that Yahoo went public with the details after a stolen database went on sale on the black market.
9. Adult Friend Finder
Date: October 2016 Impact: 412.2 million accounts
The adult-oriented social networking service The FriendFinder Network had 20 years’ worth of user data across six databases stolen by cyber-thieves in October 2016. Given the sensitive nature of the services offered by the company – which include casual hookup and adult content websites like Adult Friend Finder, Penthouse.com, and Stripshow.com – the breach of data from more than 414 million accounts including names, email addresses, and passwords had the potential to be particularly damning for victims. What’s more, the vast majority of the exposed passwords were hashed via the notoriously weak algorithm SHA-1, with an estimated 99% of them cracked by the time LeakedSource.com published its analysis of the data set on November 14, 2016.
10. MySpace
Date: 2013 Impact: 360 million user accounts
Though it had long stopped being the powerhouse that it once was, social media site MySpace hit the headlines in 2016 after 360 million user accounts were leaked onto both LeakedSource.com and put up for sale on dark web market The Real Deal with an asking price of 6 bitcoin (around $3,000 at the time).
According to the company , lost data included email addresses, passwords and usernames for “a portion of accounts that were created prior to June 11, 2013, on the old Myspace platform. In order to protect our users, we have invalidated all user passwords for the affected accounts created prior to June 11, 2013, on the old Myspace platform. These users returning to Myspace will be prompted to authenticate their account and to reset their password by following instructions.”
It’s believed that the passwords were stored as SHA-1 hashes of the first 10 characters of the password converted to lowercase.
11. NetEase
Date: October 2015 Impact: 235 million user accounts
NetEase, a provider of mailbox services through the likes of 163.com and 126.com, reportedly suffered a breach in October 2015 when email addresses and plaintext passwords relating to 235 million accounts were being sold by dark web marketplace vendor DoubleFlag. NetEase has maintained that no data breach occurred and to this day HIBP states : “Whilst there is evidence that the data itself is legitimate (multiple HIBP subscribers confirmed a password they use is in the data), due to the difficulty of emphatically verifying the Chinese breach it has been flagged as “unverified.”
12. Court Ventures (Experian)
Date: October 2013 Impact: 200 million personal records
Experian subsidiary Court Ventures fell victim in 2013 when a Vietnamese man tricked it into giving him access to a database containing 200 million personal records by posing as a private investigator from Singapore. The details of Hieu Minh Ngo’s exploits only came to light following his arrest for selling personal information of US residents (including credit card numbers and Social Security numbers) to cybercriminals across the world, something he had been doing since 2007. In March 2014, he pleaded guilty to multiple charges including identity fraud in the US District Court for the District of New Hampshire. The DoJ stated at the time that Ngo had made a total of $2 million from selling personal data.
13. LinkedIn
Date: June 2012 Impact: 165 million users
With its second appearance on this list is LinkedIn, this time in reference to a breach it suffered in 2012 when it announced that 6.5 million unassociated passwords (unsalted SHA-1 hashes) had been stolen by attackers and posted onto a Russian hacker forum. However, it wasn’t until 2016 that the full extent of the incident was revealed. The same hacker selling MySpace’s data was found to be offering the email addresses and passwords of around 165 million LinkedIn users for just 5 bitcoins (around $2,000 at the time). LinkedIn acknowledged that it had been made aware of the breach, and said it had reset the passwords of affected accounts.
14. Dubsmash
Date: December 2018 Impact: 162 million user accounts
In December 2018, New York-based video messaging service Dubsmash had 162 million email addresses, usernames, PBKDF2 password hashes, and other personal data such as dates of birth stolen, all of which was then put up for sale on the Dream Market dark web market the following December. The information was being sold as part of a collected dump also including the likes of MyFitnessPal (more on that below), MyHeritage (92 million), ShareThis, Armor Games, and dating app CoffeeMeetsBagel.
Dubsmash acknowledged the breach and sale of information had occurred and provided advice around password changing. However, it failed to state how the attackers got in or confirm how many users were affected.
Date: October 2013 Impact: 153 million user records
In early October 2013, Adobe reported that hackers had stolen almost three million encrypted customer credit card records and login data for an undetermined number of user accounts. Days later, Adobe increased that estimate to include IDs and encrypted passwords for 38 million “active users.” Security blogger Brian Krebs then reported that a file posted just days earlier “appears to include more than 150 million username and hashed password pairs taken from Adobe.” Weeks of research showed that the hack had also exposed customer names, password, and debit and credit card information. An agreement in August 2015 called for Adobe to pay $1.1 million in legal fees and an undisclosed amount to users to settle claims of violating the Customer Records Act and unfair business practices. In November 2016, the amount paid to customers was reported to be $1 million.
More news-making data breaches:
- Hackers steal data of 200k Lulu customers in an alleged breach
- Evolve data breach impacted upward of 7.64 million consumers
The biggest data breach fines, penalties, and settlements so far
- Dell data breach exposes data of 49 million customers
- Sensitive US government data exposed after Space-Eyes data breach
Related content
Most interesting products to see at rsac 2024, google launches google threat intelligence at rsa conference, accenture, ibm, mandiant join elite cyber defenders program to secure critical infrastructure, most interesting products to see at rsa conference 2023, from our editors straight to your inbox.

Michael Hill is the UK editor of CSO Online. He has spent the past five-plus years covering various aspects of the cybersecurity industry, with particular interest in the ever-evolving role of the human-related elements of information security. A keen storyteller with a passion for the publishing process, he enjoys working creatively to produce media that has the biggest possible impact on the audience.
More from this author
If you don’t already have a generative ai security policy, there’s no time to lose, bigid unveils new data risk remediation guidance feature, generative ai could erode customer trust, half of business leaders say, us launches “shields ready” campaign to secure critical infrastructure, eclypsium launches supply chain security guide to track risks and incidents, frontegg releases new identity, user management solution for saas products, organizations turn to zero trust, network segmentation as ransomware attacks double.

Dan Swinhoe is UK Editor of CSO Online. Previously he was Senior Staff Writer at IDG Connect.
EU’s DORA regulation explained: New risk management requirements for financial firms
Man-in-the-middle (mitm) attack definition and examples, how decision-making psychology can improve incident response, how stagecoach stops bec attacks with security training, email controls, interim data deal and brexit: what cisos need to know now the uk has left the eu, uk telecommunications security bill aims to improve telco security for 5g rollouts, what is typosquatting a simple but effective attack technique, what cisos need to know about europe’s gaia-x cloud initiative, most popular authors.

- Gyana Swain
Show me more
Crowdstrike questions could give cisos pause — with options available.

Who writes the code in your security software? You need to know

AWS environments compromised through exposed .env files

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

Cybersecurity Insights for Tech Leaders: Addressing Dynamic Threats and AI Risks with Resilience

Data Security Case Studies
Data security in databases: exploring case studies.
In today's digital world, the security of data stored in databases has become a critical concern for organizations and individuals alike. With the ever-increasing sophistication of cyberattacks, it is essential for programmers to understand the importance of data security and implement robust measures to safeguard sensitive information. In this blog post, we delve into the world of data security within databases, examining real-life case studies that highlight the challenges and solutions faced by organizations. Through code snippets and examples, we will explore the best practices to protect data and mitigate potential risks.
Understanding the Need for Data Security
Before we dive into the case studies, let's first comprehend why data security is crucial. Databases serve as a repository for valuable and often confidential information, including financial data, user credentials, and personal details. Unauthorized access to this data can result in severe consequences, such as financial loss, reputation damage, and legal implications. To ensure the integrity, confidentiality, and availability of data, programmers must implement robust security measures.
Case Study 1: SQL Injection Attack
One of the most common and well-known database security threats is the SQL injection attack. This type of attack involves manipulating user inputs to execute unauthorized SQL commands, potentially compromising the entire database.
To better understand this threat, consider the following example:
In this code snippet, the application constructs an SQL query by directly concatenating user input into the SQL statement. An attacker can exploit this vulnerability by providing malicious input such as ' OR '1'='1'; -- , which would cause the query to return all rows from the users table, bypassing the authentication process.
To mitigate SQL injection attacks, programmers should adopt prepared statements or parameterized queries, which separate the query from the user input. This prevents malicious inputs from altering the query structure.
Case Study 2: Inadequate Access Control
Another significant aspect of data security is controlling access to the database. In our second case study, we examine the consequences of inadequate access control.
Consider a scenario where a database administrator fails to implement proper access controls, allowing unauthorized individuals to gain escalated privileges. In such a situation, an attacker could exploit this vulnerability to access or modify sensitive data, leading to a data breach.
To mitigate this risk, programmers should enforce strict access controls based on the principle of least privilege (PoLP). This means granting users only the minimum privileges required to perform their tasks. Additionally, implementing suitable authentication mechanisms and regular auditing of user permissions are essential for maintaining a secure database environment.
Case Study 3: Unencrypted Data
Encryption serves as a powerful technique to protect data, both at rest and during transmission. Our third case study focuses on the implications of storing unencrypted data in a database.
Imagine a scenario where an attacker gains unauthorized access to a database and steals valuable information. If the data is stored in plain text, the attacker can easily read and exploit it. However, if the data is encrypted, even if compromised, it remains unreadable without the decryption key.
To ensure data confidentiality, programmers must implement encryption mechanisms such as using SSL/TLS for secure communication and encrypting sensitive fields, such as passwords and credit card numbers, within the database.
As programmers, it is our responsibility to prioritize data security within databases. By examining real-life case studies, we have explored common vulnerabilities and their potential consequences. We have also learned how to mitigate these risks through the use of prepared statements to prevent SQL injection, enforcing strict access control, and implementing encryption.
Remember, securing data is an ongoing process, and staying updated with the latest security practices is crucial to protect against evolving threats. By implementing strong security measures and staying vigilant, programmers can ensure the integrity and confidentiality of data within databases.
Now that we have explored these case studies and best practices, let's put this knowledge into action and take proactive steps to secure our databases effectively.
Note: The above content is in Markdown format, ready to be converted into HTML.
Hi, I'm Ada, your personal AI tutor. I can help you with any coding tutorial. Go ahead and ask me anything.
I have a question about this topic
Give more examples
- Digital Marketing
- Facebook Marketing
- Instagram Marketing
- Ecommerce Marketing
- Content Marketing
- Data Science Certification
- Machine Learning
- Artificial Intelligence
- Data Analytics
- Graphic Design
- Adobe Illustrator
- Web Designing
- UX UI Design
- Interior Design
- Front End Development
- Back End Development Courses
- Business Analytics
- Entrepreneurship
- Supply Chain
- Financial Modeling
- Corporate Finance
- Project Finance
- Harvard University
- Stanford University
- Yale University
- Princeton University
- Duke University
- UC Berkeley
- Harvard University Executive Programs
- MIT Executive Programs
- Stanford University Executive Programs
- Oxford University Executive Programs
- Cambridge University Executive Programs
- Yale University Executive Programs
- Kellog Executive Programs
- CMU Executive Programs
- 45000+ Free Courses
- Free Certification Courses
- Free DigitalDefynd Certificate
- Free Harvard University Courses
- Free MIT Courses
- Free Excel Courses
- Free Google Courses
- Free Finance Courses
- Free Coding Courses
- Free Digital Marketing Courses
25 Cybersecurity Case Studies [Deep Analysis][2024]
In our digital world, robust cybersecurity is critical. Each of the 15 case studies in this collection explores the challenges, strategies, and results of securing digital assets against cyber threats. Covering real-world scenarios from various organizations, these case studies offer insights into innovative security solutions and underscore the necessity of protecting information from increasingly sophisticated cybercriminals.
25 Cybersecurity Case Studies
Case study 1: enhancing network security with predictive analytics (cisco) .
Challenge: Cisco encountered difficulties in protecting its extensive network infrastructure from complex cyber threats, aiming to enhance security by predicting breaches before they happen.
Solution: Cisco created a predictive analytics tool using machine learning to evaluate network traffic patterns and spot anomalies signaling potential threats. Integrated with their current security protocols, this system allows for dynamic defense adjustments and real-time alerts to system administrators about possible vulnerabilities.
Overall Impact:
1. Improved Security Posture: The predictive system enabled proactive responses to potential threats, significantly reducing the incidence of successful cyber attacks.
2. Enhanced Operational Efficiency: Automating threat detection and response processes allowed Cisco to manage network security more efficiently, with fewer resources dedicated to manual monitoring.
Key Takeaways:
1. Proactive Security Measures: Employing predictive cybersecurity analytics helps organizations avoid potential threats.
2. Integration of Machine Learning: Machine learning is crucial for effectively detecting patterns and anomalies that human analysts might overlook, leading to stronger security measures.
Case Study 2: Strengthening Endpoint Security through Advanced Encryption (Microsoft)
Challenge: Microsoft faced difficulties securing many global devices, particularly protecting sensitive data across diverse platforms susceptible to advanced cyber-attacks.
Solution: Microsoft deployed an advanced encryption system enhanced with multi-factor authentication to secure data, whether stored or in transit. This solution integrates smoothly with Microsoft’s existing security frameworks, employs robust encryption algorithms, and adapts continuously to emerging security threats.
1. Robust Data Protection: By encrypting data on all endpoints, Microsoft significantly minimized the risk of data breaches, ensuring that sensitive information remains inaccessible to unauthorized parties.
2. Increased User Confidence: The enhanced security measures fostered greater trust among users, encouraging the adoption of Microsoft products and services in environments requiring stringent security protocols.
1. Essential Role of Encryption: Encryption remains a critical tool in protecting data across devices, serving as a fundamental component of comprehensive cybersecurity strategies.
2. Adaptive Security Systems: Implementing flexible, adaptive security solutions is essential to effectively address the dynamic nature of cyber threats, ensuring ongoing protection against potential vulnerabilities.
Case Study 3: Implementing Zero Trust Architecture for Enhanced Data Security (IBM)
Challenge: With the increase in remote work, IBM needed to bolster its data security strategy to protect against vulnerabilities in its internal networks and ensure that only verified users and devices accessed specific network segments.
Solution: IBM implemented a Zero Trust security model requiring rigorous verification for every access attempt across its network. This model employs strict identity checks, network micro-segmentation, and least privilege access controls, coupled with real-time threat detection and response to enhance security dynamically.
1. Enhanced Security Compliance: The implementation of Zero Trust architecture helped IBM meet stringent compliance requirements and protect sensitive data effectively.
2. Reduced Data Breach Incidents: By enforcing strict access controls and continuous verification, IBM significantly lowered the risk of data breaches.
1. Necessity of Zero Trust: Adopting a Zero Trust approach is crucial for organizations looking to protect critical data in increasingly complex IT environments.
2. Continuous Verification: Regular and comprehensive verification processes are essential for maintaining security integrity in a dynamic threat landscape.
Related: Cybersecurity Interview Questions
Case Study 4: Revolutionizing Threat Detection with AI-Powered Security Systems (Palo Alto Networks)
Challenge: Palo Alto Networks struggled to manage the large volumes of security data and keep pace with rapidly evolving cyber threats, as traditional methods faltered against advanced threats and sophisticated malware.
Solution: Palo Alto Networks introduced an AI-powered security platform that uses developed machine learning algorithms to analyze extensive network data. This system automates threat detection by identifying subtle patterns indicative of cyber threats, allowing quicker and more precise responses.
1. Improved Threat Detection Rates: The AI-driven system significantly improved identifying and responding to threats, decreasing the time from detection to resolution.
2. Scalable Security Solutions: The automation and scalability of the AI system allowed Palo Alto Networks to offer more robust security solutions to a larger client base without compromising efficiency or effectiveness.
1. Leveraging Artificial Intelligence: AI is transforming the field of cybersecurity by enabling the analysis of complex data sets and the identification of threats that human analysts would miss.
2. Automation in Cyber Defense: Embracing automation in cybersecurity operations is crucial for organizations to efficiently manage the increasing number of threats and reduce human error.
Case Study 5: Enhancing Phishing Defense with Real-Time User Education (Google)
Challenge: With its vast ecosystem and user base, Google was highly susceptible to sophisticated phishing attacks that traditional security measures couldn’t adequately counter.
Solution: Google introduced a real-time user education program within its email services. This system flags suspicious emails and offers users contextual information and tips on recognizing phishing attempts, supported by machine learning algorithms that continuously adapt to new phishing strategies.
1. Increased User Awareness: By educating users at the moment of potential danger, Google has significantly increased awareness and prevention of phishing attacks among its user base.
2. Reduced Successful Phishing Attacks: The proactive educational approach has led to a noticeable decrease in successful phishing attacks, enhancing overall user security.
1. Importance of User Education: Continuous user education is vital in combating phishing and other forms of social engineering.
2. Adaptive Learning Systems: Utilizing adaptive learning systems that evolve with changing attack vectors is crucial for effective cybersecurity.
Case Study 6: Securing IoT Devices with Blockchain Technology (Samsung)
Challenge: As a prominent IoT device manufacturer, Samsung encountered difficulties in protecting its devices from escalating cyber threats, hindered by IoT networks’ decentralized and diverse nature.
Solution: Samsung innovated by using blockchain technology to secure its IoT devices, establishing a decentralized ledger for each device that transparently and securely records all transactions and data exchanges, thwarting unauthorized tampering. This blockchain system seamlessly integrates with Samsung’s existing security protocols, enhancing the overall security of its IoT devices.
1. Enhanced Device Integrity: The blockchain technology ensured the integrity of device communications and data exchanges, significantly decreasing the risk of tampering and unauthorized access.
2. Increased Trust in IoT Devices: The robust security features blockchain technology provides have increased consumer trust in Samsung’s IoT products, fostering greater adoption.
1. Blockchain as a Security Enhancer: Blockchain technology can enhance security for IoT and other decentralized networks.
2. Holistic Security Approaches: Adopting comprehensive, multi-layered security strategies is essential for protecting complex and interconnected device ecosystems.
Related: How to Move from Sales to a Cybersecurity Career?
Case Study 7: Implementing Secure Biometric Authentication for Mobile Banking (HSBC)
Challenge: With the rise in mobile banking, HSBC faced growing security threats, such as identity theft and unauthorized account access, as traditional password-based methods fell short.
Solution: HSBC introduced a secure biometric authentication system across its mobile banking platforms, employing fingerprint scanning and facial recognition technologies enhanced by AI. This integration improved accuracy and reduced false positives, bolstering security while streamlining user access to banking services.
1. Strengthened Account Security: Introducing biometric authentication significantly minimized the risk of illegal access, providing a more secure banking experience.
2. Improved User Satisfaction: Customers appreciated the ease of use and increased security, leading to higher adoption rates of mobile banking services.
1. Biometric Security: Biometrics offer a powerful alternative to traditional security measures, providing enhanced security and user convenience.
4. Adaptation to User Needs: Security measures that align with user convenience can drive higher engagement and adoption rates, benefiting both users and service providers.
Case Study 8: Advanced Threat Intelligence Sharing in the Financial Sector (JPMorgan Chase)
Challenge: JPMorgan Chase faced escalating cyber threats targeting the financial sector, with traditional defense strategies proving inadequate against these threats’ dynamic and sophisticated nature.
Solution: JPMorgan Chase initiated a threat intelligence sharing platform among leading financial institutions, enabling the real-time exchange of cyber threat information. This collaboration enhances predictive capabilities and attack mitigation, leveraging advanced technologies and collective expertise to fortify cybersecurity defenses.
1. Enhanced Predictive Capabilities: The collaborative platform significantly improved the predictive capabilities of each member institution, allowing for more proactive security measures.
2. Strengthened Sector-Wide Security: The shared intelligence contributed to a stronger, more unified defense posture across the financial sector, reducing the overall incidence of successful cyber attacks.
1. Collaboration is Key: Sharing threat intelligence across organizations can significantly enhance the collective ability to counteract cyber threats.
2. Sector-Wide Security Approaches: Developing industry-wide security strategies is crucial in sectors where collaborative defense can provide a competitive advantage and enhance overall security.
Case Study 9: Reducing Ransomware Impact Through Advanced Backup Strategies (Adobe)
Challenge: Adobe faced heightened ransomware threats, risking data encryption and operational disruptions, compounded by the complexity and size of its extensive data repositories.
Solution: Adobe deployed a comprehensive data backup and recovery strategy featuring real-time data replication and off-site storage. This approach maintains multiple backups in varied locations, minimizing ransomware impact. Additionally, machine learning algorithms monitor for ransomware indicators, triggering immediate backup actions to prevent significant data encryption.
1. Minimized Downtime: The proactive backup strategy allowed Adobe to quickly restore services after a ransomware attack, minimizing downtime and operational disruptions.
2. Enhanced Data Protection: By securing backups in separate locations and continuously updating them, Adobe strengthened its resilience against data loss due to ransomware.
1. Proactive Backup Measures: Advanced, proactive backup strategies are essential in mitigating the effect of ransomware attacks.
2. Machine Learning in Data Protection: Leveraging machine learning for early detection and response can significantly enhance data security measures.
Related: Cybersecurity Manager Interview Questions
Case Study 10: Enhancing Cloud Security with Automated Compliance Tools (Amazon Web Services)
Challenge: As cloud computing became essential for businesses globally, Amazon Web Services (AWS) must ensure compliance with diverse international security standards to protect customer data and sustain trust.
Solution: AWS introduced automated compliance tools into its cloud platform, continuously monitoring and auditing AWS services against global standards. These tools, enhanced with AI for data analysis, swiftly detect and correct compliance deviations, upholding stringent security compliance across all customer data.
1. Streamlined Compliance Processes: Automating compliance checks significantly streamlined the process, reducing the manual workload and enhancing efficiency.
2. Consistent Security Standards: The consistent monitoring and quick resolution of compliance issues helped AWS maintain high-security standards, boosting customer confidence in cloud security.
1. Importance of Compliance Automation: Automation in compliance monitoring is crucial for maintaining high-security standards in cloud environments.
2. AI and Security Compliance: AI plays a vital role in analyzing vast amounts of compliance data, ensuring that cloud services adhere to stringent security protocols.
Case Study 11: Implementing Multi-Factor Authentication for Global Remote Workforce (Deloitte)
Challenge: With a shift to remote work, Deloitte faced increased security risks, particularly unauthorized access to sensitive data, as traditional single-factor authentication proved inadequate for their global team.
Solution: Deloitte implemented a robust multi-factor authentication (MFA) system across its operations, requiring employees to use multiple verification methods to access company networks. This system includes biometric options like fingerprint and facial recognition alongside traditional methods such as SMS codes and apps, enhancing security while providing flexibility.
1. Enhanced Security Posture: The introduction of MFA greatly strengthened Deloitte’s defense against unauthorized access, particularly in a remote working environment.
2. Increased Employee Compliance: The user-friendly nature of the MFA system ensured high levels of employee compliance and minimal disruption to workflow.
1. Necessity of Multi-Factor Authentication: MFA is a critical security measure for organizations with remote or hybrid work models to protect against unauthorized access.
2. Balancing Security and Usability: It’s crucial to implement safety measures that are both effective and user-friendly to ensure high adoption and compliance rates among employees.
Case Study 12: Fortifying Financial Transactions with Real-Time Fraud Detection Systems (Mastercard)
Challenge: Mastercard dealt with the continuous challenge of fraudulent transactions, which affected their customers’ trust and led to significant financial losses. The evolving sophistication of fraud techniques required a more dynamic and predictive approach to detection and prevention.
Solution: Mastercard developed a real-time fraud detection system powered by advanced analytics and machine learning. This system analyzes transaction data across millions of transactions globally to identify unusual patterns and potential fraud. It operates in real-time, providing instant decisions to block or flag suspicious transactions, significantly enhancing financial operations’ security.
1. Reduced Incidence of Fraud: The real-time detection system has markedly decreased the number of fraudulent transactions, protecting customers and merchants.
2. Enhanced Customer Trust: With strengthened security measures, customers feel more secure when using Mastercard, leading to increased loyalty and usage.
1. Real-Time Analytics in Fraud Detection: Real-time analytics is essential for detecting and preventing fraud in the fast-paced world of financial transactions.
2. Leveraging Machine Learning: Machine learning is invaluable in recognizing and adapting to new fraudulent tactics maintaining a high level of security as threats evolve.
Related: Ways Manufacturing Sector Can Mitigate Cybersecurity Risks
Case Study 13: Cyber Resilience in the Energy Sector Through Advanced Network Segmentation (BP)
Challenge: BP, a global energy company, faced significant cyber threats to disrupt its operations and compromise sensitive data. The interconnected nature of its global infrastructure posed particular vulnerabilities, especially in an industry frequently targeted by sophisticated cyber-attacks.
Solution: BP implemented advanced network segmentation as a key strategy to enhance its cyber resilience. This approach divides the network into distinct zones, each with security controls, effectively isolating critical infrastructure from less sensitive areas. This segmentation is reinforced with stringent access controls and real-time monitoring systems that detect and respond to threats before they can propagate across the network.
1. Strengthened Infrastructure Security: Network segmentation significantly reduced the potential effect of a breach by limiting the movement of a threat within isolated network segments.
2. Improved Incident Response: The clear division of network zones allowed faster identification and isolation of security incidents, enhancing BP’s overall response capabilities.
1. Importance of Network Segmentation: Effective segmentation is critical in protecting essential services and sensitive data in large, interconnected networks.
2. Proactive Defense Strategy: A proactive approach to network security, including segmentation and real-time monitoring, is essential for high-risk industries like energy.
Case Study 14: Protecting Healthcare Data with End-to-End Encryption (Mayo Clinic)
Challenge: The Mayo Clinic, a leading healthcare organization, faced the dual challenges of protecting patient privacy and complying with stringent healthcare regulations such as HIPAA. The risk of data leaks and illegal access to sensitivehealth information was a constant concern.
Solution: The Mayo Clinic addressed these challenges by implementing end-to-end encryption across all its digital communication channels and data storage systems. This encryption ensures that patient data is secure from the point of origin to the point of destination, making it inaccessible to unauthorized users, even if intercepted during transmission.
1. Enhanced Patient Data Protection: End-to-end encryption significantly bolstered the security of patient information, virtually eliminating the risk of interception by unauthorized parties.
2. Regulatory Compliance Assurance: This robust security measure helped the Mayo Clinic maintain compliance with healthcare regulations, reducing legal risks and enhancing patient trust.
1. Critical Role of Encryption in Healthcare: End-to-end encryption is indispensable for protecting sensitive health information and ensuring compliance with healthcare regulations.
2. Building Patient Trust: Strengthening data security measures is essential in healthcare to maintain patient confidence and trust in the confidentiality of their health records.
Case Study 15: Implementing AI-Driven Security Operations Center (SOC) for Real-Time Threat Management (Sony)
Challenge: Sony, a global conglomerate with diverse business units, faced complex security challenges across its vast digital assets and technology infrastructure. Managing these risks required a more sophisticated approach than traditional security operations centers could offer.
Solution: Sony enhanced its security operations by implementing an AI-driven Security Operations Center (SOC). Utilizing machine learning and artificial intelligence, this system monitors and analyzes threats in real-time. It automatically detects patterns of cyber threats and initiates responses to potential security incidents without human intervention.
1. Elevated Threat Detection and Response: The AI-driven SOC enabled Sony to detect and respond to threats more quickly and accurately, significantly enhancing the effectiveness of its cybersecurity efforts.
2. Reduced Operational Costs: Automating routine monitoring and response tasks reduced the workload on human analysts, allowing Sony to allocate resources more efficiently and reduce operational costs.
1. Advantages of AI in Cybersecurity: Utilizing AI technologies in security operations centers can greatly enhance threat detection and response speed and accuracy.
2. Operational Efficiency: Integrating AI into cybersecurity operations helps streamline processes and reduce the dependence on manual intervention, leading to cost savings and improved security management.
Related: Predictions About the Future of Cybersecurity
Case Study 16: Securing Online Transactions with Behavioral Biometrics (Visa)
Challenge: Visa faced ongoing challenges with securing online transactions, especially against sophisticated fraud techniques like social engineering and credential stuffing, which traditional authentication methods often failed to detect.
Solution: Visa implemented a real-time behavioral biometrics system that scrutinizes user behavior patterns like typing speed, mouse movements, and device interactions. This technology enhances security by verifying users’ identities based on their unique behavioral traits, integrating seamlessly with existing security frameworks. This adds a robust layer of protection, ensuring transactions are safeguarded against unauthorized access.
1. Reduced Fraud Incidents : The behavioral biometrics technology significantly decreased instances of online fraud, providing a more secure transaction environment for users.
2. Enhanced User Experience : By adding this passive authentication layer, Visa improved the user experience, as customers did not need to perform additional steps to prove their identity.
1. Behavioral Biometrics as a Fraud Prevention Tool : Behavioral biometrics offer a subtle yet powerful means of authenticating users, significantly enhancing online transaction security.
2. Seamless Security Integration : Integrating advanced security technologies like behavioral biometrics can boost security without compromising user convenience.
Case Study 17: Streamlining Regulatory Compliance with AI-Driven Audit Trails (Goldman Sachs)
Challenge: Goldman Sachs needed to maintain stringent compliance with financial regulations globally, which required detailed and accurate tracking of all transaction data. This task was becoming increasingly cumbersome and error-prone.
Solution: Goldman Sachs introduced an AI-driven platform that automatically generates and maintains audit trails for all transactions. This system uses machine learning algorithms to ensure all data is captured accurately and formatted for compliance reviews, greatly reducing human error and the resources needed for manual audits.
1. Enhanced Compliance Accuracy : The AI-driven audit trails improved regulatory compliance by ensuring all transactions were accurately recorded and easily accessible during audits.
2. Reduced Operational Costs : By automating the audit process, Goldman Sachs minimized the need for extensive manual labor, reducing operational costs and enhancing efficiency.
1. AI in Compliance : Utilizing AI to automate compliance tasks can significantly increase accuracy and efficiency.
2. Cost-Effective Regulatory Practices : Automating complex compliance requirements with AI technologies can reduce costs and streamline operations, particularly in highly regulated industries like finance.
Related: Biotech Cybersecurity Case Studies
Case Study 18: Enhancing Cybersecurity with Advanced SIEM Tools (Hewlett Packard Enterprise)
Challenge: Hewlett Packard Enterprise (HPE) faced complex cybersecurity threats across its global IT infrastructure, requiring a solution that could provide comprehensive visibility and fast response times to potential security incidents.
Solution: HPE implemented an advanced Security Information and Event Management (SIEM) system that seamlessly consolidates data from multiple network sources. This integration allows for enhanced monitoring and management of security events. This platform utilizes sophisticated analytics to detect anomalies and potential threats, providing real-time alerts and enabling quick, informed decisions on incident responses.
1. Increased Threat Detection Capability : The SIEM system enhanced HPE’s ability to swiftly detect and respond to threats, improving overall cybersecurity measures.
Streamlined Security Operations : By integrating various data inputs into a single system, HPE streamlined its security operations, enhancing the efficiency and effectiveness of its response to cyber incidents.
1. Integration of Advanced Analytics : Utilizing advanced analytics in SIEM tools can significantly improve the detection and management of cybersecurity threats.
2. Real-time Monitoring and Response : Implementing systems equipped with real-time monitoring and rapid response capabilities is crucial to maintain a robust security posture. These systems ensure timely detection and effective management of potential threats.
Case Study 19: Cybersecurity Enhancement through Cloud-Based Identity and Access Management (Salesforce)
Challenge: Salesforce needed to enhance its identity and access management controls to secure its cloud-based services against unauthorized access and potential data breaches.
Solution: Salesforce implemented a cloud-based Identity and Access Management (IAM) framework, enhancing security with robust identity verification, access control, and user activity monitoring. Key features include multi-factor authentication, single sign-on, and role-based access control, essential for safeguarding sensitive data and applications.
1. Improved Access Control : The cloud-based IAM solution strengthened Salesforce’s ability to control and monitor access to its services, significantly reducing the risk of unauthorized access.
2. Enhanced Data Security : With stronger identity verification processes and detailed access logs, Salesforce enhanced the security of its customer data and applications.
1. Importance of Robust IAM Systems : Effective identity and access management systems protect cloud environments from unauthorized access and breaches.
2. Cloud-Based Security Solutions : Using cloud-based security solutions offers scalability and flexibility, enabling businesses to adapt to evolving security requirements swiftly. This adaptability ensures that organizations can efficiently meet their security needs as they change.
Related: Aviation Cybersecurity Case Studies
Case Study 20: Securing Remote Work with Virtual Desktop Infrastructure (VDI) (Dell Technologies)
Challenge: Dell Technologies recognized the need to secure a rapidly expanding remote workforce to protect sensitive data and maintain productivity across dispersed teams.
Solution: Dell deployed a Virtual Desktop Infrastructure (VDI) solution, enabling remote employees to access their work environments from any location securely. This system centralizes desktop management and enhances security by hosting all operations and data on internal servers, minimizing endpoint vulnerabilities.
1. Enhanced Data Security : Centralizing data storage and operations significantly reduced the risk of data breaches associated with remote work.
2. Increased Workforce Flexibility : The VDI system enabled Dell employees to access their work securely and efficiently from various remote locations, supporting business continuity and operational flexibility.
1. Centralized Management for Enhanced Security : Using VDI to centralize desktop management can significantly enhance security by reducing endpoint vulnerabilities.
2. Support for Remote Work : Implementing VDI is crucial for businesses looking to secure and support a diverse and geographically dispersed workforce.
Case Study 21: Implementing Intrusion Detection Systems for Network Security (AT&T)
Challenge: AT&T needed to bolster its defenses against increasingly sophisticated cyber-attacks aimed at its vast network infrastructure.
Solution: AT&T implemented a sophisticated Intrusion Detection System (IDS) that monitors network traffic to detect suspicious activities. This system enhances network security by identifying potential threats in real time. This system utilizes deep learning algorithms to scrutinize traffic patterns and pinpoint anomalies, effectively detecting potential intrusions. The IDS enhances AT&T’s ability to recognize and respond to security threats, ensuring a more secure network environment.
1. Improved Detection of Network Threats : The IDS significantly enhanced AT&T’s capabilities in identifying and responding to security threats promptly.
2. Strengthened Network Resilience : With the IDS actively monitoring and analyzing network traffic, AT&T improved its overall network security posture, reducing the impact of potential cyber-attacks.
1. Crucial Role of IDS in Network Security : IntrusionDetection Systems are paramount for early detection of threats and maintaining network integrity.
2. Leveraging Deep Learning for Security : Incorporating deep learning algorithms into security systems can improve the accuracy and efficiency of threat detection, adapting to new threats as they evolve.
Related: Generative AI in Cybersecurity
Case Study 22: Enhancing Security through User Behavior Analytics (UBA) (Adobe)
Challenge: Adobe needed to refine its security measures to effectively detect insider threats and unusual user behavior within its vast array of digital services and software platforms.
Solution: Adobe implemented a User Behavior Analytics (UBA) system that collects and analyzes data on user activities across its platforms. This advanced analytics tool utilizes machine learning to identify patterns that easily deviate from normal behavior, indicating potential security threats or data breaches.
1. Improved Insider Threat Detection :The User Behavior Analytics (UBA) system allowed Adobe to identify and respond to insider threats and unusual user behavior more precisely.
2. Enhanced Data Protection : By understanding user behavior patterns, Adobe strengthened its ability to safeguard sensitive information from potential internal risks.
1. Importance of Monitoring User Behavior : Monitoring user behavior is crucial for detecting security threats that traditional tools might not catch.
2. Machine Learning Enhances Security Analytics : Leveraging machine learning in user behavior analytics can significantly improve the detection of complex threats.

Case Study 23: Blockchain-Based Supply Chain Security (Maersk)
Challenge: Maersk, a global leader in container logistics, faced significant challenges in securing its complex supply chain from tampering, fraud, and cyber threats, which could disrupt processes and operations and result in financial losses.
Solution: Maersk introduced a blockchain-based security solution for supply chains, ensuring transparent and tamper-proof tracking of goods from origin to destination. This decentralized ledger provides all parties with access to real-time data, securing and preserving the integrity of information throughout the supply chain.
1. Increased Transparency and Security : The blockchain solution enhanced the security and transparency of Maersk’s supply chain, significantly reducing the risk of fraud and tampering.
2. Improved Efficiency and Trust : By providing a single source of truth, blockchain technology streamlined operations and build trust among partners and customers.
1. Blockchain as a Security Tool in Supply Chains : Blockchain technology can greatly enhance security and transparency in complex supply chains.
2. Improving Supply Chain Integrity : Adopting blockchain can prevent tampering and fraud, ensuring integrity throughout logistics.
Related: Cybersecurity Budget Allocation Tips
Case Study 24: Advanced Anomaly Detection in Financial Transactions (Citibank)
Challenge: Citibank faced increasing incidents of sophisticated financial fraud, including money laundering and identity theft, which traditional security measures struggled to address effectively.
Solution: Citibank implemented an advanced anomaly detection system that utilizes artificial intelligence to easily monitor and analyze real-time financial transactions. This system is designed to detect unusual transaction patterns that may indicate fraudulent activities, significantly improving the accuracy and speed of fraud detection.
1. Reduced Financial Fraud : Implementing the anomaly detection system significantly reduced fraudulent transactions, safeguarding both the bank and its customers. This enhanced security measure helps maintain trust and protects financial interests.
2. Enhanced Customer Trust : With stronger security measures, customers felt more secure conducting their financial activities, thus enhancing their overall trust in Citibank.
1. Utilizing AI for Fraud Detection : Artificial intelligence is a powerful tool for identifying complex patterns in transaction data that may signify fraudulent activities.
2. Importance of Real-Time Monitoring : Real-time monitoring of transactions is crucial for early detection and prevention of financial fraud.
Case Study 25: Cybersecurity Training and Awareness Programs (Intel)
Challenge: Intel, as a leading technology company, recognized the need to bolster its defenses against cyber threats not just technologically but also by empowering its workforce. The human factor often being a weak link in cybersecurity, there was a critical need for comprehensive security training.
Solution: Intel launched a widespread cybersecurity training and awareness program for all employees. The program includes regular training sessions, phishing and other attack scenario simulations, and continuous updates on the latest security practices and threats.
1. Enhanced Employee Awareness and Responsiveness : The training programs significantly improved employees’ ability to recognize and reply to cyber threats, decreasing the risk of successful attacks.
2. Strengthened Organizational Cyber Resilience : With a more informed and vigilant workforce, Intel strengthened its overall cybersecurity posture, mitigating risks across all levels of the organization.
1. Investing in Human Capital for Cyber Defense : Continuous cybersecurity training is essential for empowering employees and turning them into an active line of defense against cyber threats.
2. Role of Awareness Programs : Comprehensive awareness programs are crucial in maintaining a high level of vigilance and preparedness among employees, which is vital for mitigating human-related security risks.
Related: Ways to Train Employees on Cybersecurity
Navigating through these 15 cybersecurity case studies underscores a vital reality: as cyber threats evolve, so must our defenses. These stories highlight organizational resilience and creativity in combating digital threats, offering valuable lessons in proactive and reactive security measures. As technology progresses, staying ahead of potential threats is paramount. These case studies are guides toward building more secure and resilient digital environments.
- Top 75 Product Management Interview Questions &Answers [2024]
- CTO’s Guide to Navigating Regulatory Compliance [2024]
Team DigitalDefynd
We help you find the best courses, certifications, and tutorials online. Hundreds of experts come together to handpick these recommendations based on decades of collective experience. So far we have served 4 Million+ satisfied learners and counting.
Role of Chief Information Officer in Cyber Security [2024]

Role of CMO in Cyber Security [2024]

What is Cybersecurity Awareness Month? [2024]

Skills required to be a Cybersecurity Leader [2024]

Top 50 Cybersecurity Manager Interview Questions & Answers [2024]

10 Alternative Career Paths for Cyber Security Professionals [2024]
Advancing database security: a comprehensive systematic mapping study of potential challenges
- Original Paper
- Open access
- Published: 17 July 2023
Cite this article
You have full access to this open access article

- Asif Iqbal 1 ,
- Siffat Ullah Khan 1 ,
- Mahmood Niazi 2 , 3 ,
- Mamoona Humayun 4 ,
- Najm Us Sama 5 ,
- Arif Ali Khan 6 &
- Aakash Ahmad 7
3926 Accesses
2 Citations
Explore all metrics
The value of data to a company means that it must be protected. When it comes to safeguarding their local and worldwide databases, businesses face a number of challenges. To systematically review the literature to highlight the difficulties in establishing, implementing, and maintaining secure databases. In order to better understand database system problems, we did a systematic mapping study (SMS). We’ve analyzed 100 research publications from different digital libraries and found 20 issues after adopting inclusion and exclusion criteria. This SMS study aimed to identify the most up-to-date research in database security and the different challenges faced by users/clients using various databases from a software engineering perspective. In total, 20 challenges were identified related to database security. Our results show that “weak authorization system”, “weak access control”, “privacy issues/data leakage”, “lack of NOP security”, and “database attacks” as the most frequently cited critical challenges. Further analyses were performed to show different challenges with respect to different phases of the software development lifecycle, venue of publications, types of database attacks, and active research institutes/universities researching database security. The organizations should implement adequate mitigation strategies to address the identified database challenges. This research will also provide a direction for new research in this area.
Similar content being viewed by others

Database Security: Attacks and Solutions

Reverse Engineering of Database Security Policies

Automated Generation of Multi-tenant Database Systems Based upon System Design Diagrams
Explore related subjects.
- Artificial Intelligence
Avoid common mistakes on your manuscript.
1 Introduction
Companies’ databases (DBs) are repositories of their most significant and high-value data. As DB utilization has surged, so has the frequency of attacks on these databases. A DB attack is characterized as an event that jeopardizes a resource by altering or destroying vital data [ 1 , 2 ]. The common goal of DB attacks is to access critical information. Illicitly acquiring sensitive data such as credit card details, banking data, and personal identifiers is another prevalent motive behind DB hacks. In our interconnected global society, several technologies provide avenues for DB attacks to exploit vulnerabilities in DB architecture, as per common understanding [ 1 , 3 , 4 ].
Many enterprises confront challenges like data piracy, data replication, and denial of service attacks. To infiltrate a company’s DBs, cybercriminals scout for system vulnerabilities and exploit them using specialized tools [ 5 , 6 ].
The aspect of security should be prioritized during the development of information systems, particularly DBs. In terms of software development, security concerns must be addressed at every stage of the development cycle [ 7 ]. As illustrated in Fig. 1 , security breaches, including the loss of critical data, have become commonplace in recent years. Given the importance of data security to numerous businesses, a range of measures and methodologies are required to safeguard the DB [ 8 , 9 , 10 ]. A secure DB is designed to react appropriately in the event of a potential DB attack [ 11 ].
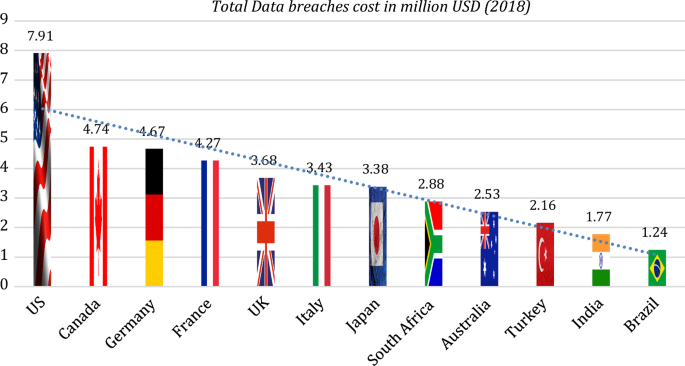
Total data breaches cost in different countries [ 5 ]
In the current world, the impact of cyber-attacks on the commercial landscape must be addressed. To succeed in the globalized environment, businesses must ensure the protection of their vital data. DBs can be safeguarded from unauthorized access [ 12 , 13 , 14 ]. When a DB is outsourced to the cloud, cloud platforms introduce security challenges such as unreliable service providers, malicious cloud employees, data protection, consistency, and scalability. With cloud DBs becoming increasingly susceptible to both external and internal threats, traditional and conventional security measures are insufficient for their protection [ 15 , 16 ].
While extensive work has been done in this field, much of it focuses on a few specific DB platforms or problems, typically explored through standard literature reviews. We aim to provide a more holistic view by conducting a systematic mapping study (SMS) to identify security concerns in DB architecture, development, and maintenance from a software engineering perspective. This SMS will help us identify the ongoing research challenges and priorities.
The following research questions (RQs) will guide our SMS to achieve our study objectives:
RQ1 What is the current state of the art in the development and implementation of secure DBs?
RQ2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
1.1 Paper contribution
The contributions of the intended work are as follows:
The proposed research undertakes a systematic mapping study (SMS) to identify and emphasize the challenges associated with developing and maintaining secure databases.
In addition to showing the difficulties experienced by users using various databases from a software engineering standpoint, our SMS survey sheds light on some of the most current database security studies.
It also highlights the importance of maintaining careful attention to database security and suggests a direction for future research in this field.
1.2 Motivation for the paper
Several research in the literature seeks to give a solution for database security. However, before moving forward with new solutions, it is necessary to synthesize current knowledge to offer security practitioners the most up-to-date information. We must identify the cutting-edge in constructing, implementing, and maintaining dependable databases, as well as security challenges, so BD’s design, development, and maintenance may be secure. The motivation behind this research is to provide in-depth solutions to these problems.
1.3 Paper organization
The remainder of the article is arranged in the following manner.
In Sect. 2 , we discussed the background of DB security, and Sect. 3 , illustrated the research methodology in detail. The results of our conducted SMS are given in Sect. 4 . In Sect. 5 , the Implication of our findings is discussed. Finally, the conclusion and future work are discussed in Sect. 6 . Other supportive information is provided in the rest of the sections at the bottom of this paper.
2 Background
There are a number of studies that look at database security from different angles. In their study [ 17 ], Mai et al. suggest using cloud-based security measures to safeguard power system databases. Using an RSA encryption method, public and private keys are generated for database encryption; a huge prime integer is chosen randomly from the cloud platform’s Simple Storage Service and used as the client key. When the database receives a verification key, it compares it to the public key and private key established by the RSA encryption method. If the database determines that the access is legitimate, it provides feedback on the access. According to the findings of the tests, the database can be protected against threats as the threat situation value is always less than 0.50 once the design technique has been implemented.
A data encryption algorithm was developed by Ibrahim et al., which provides an encryption-based solution for DB security. In this system, information is encrypted using standard ASCII characters. They encrypted all of the data in the database and used three keys to access the primary formula. Numbers and text both work for the data. The suggested formula may restore the data’s original format by combining another coordinator with the aforementioned three keys. In order to achieve a comparable data size to when the data is encrypted at a decent pace, the algorithm prioritizes data size and recording speed [ 18 ].
The article offers a lightweight cryptosystem based on the Rivest Cypher 4 (RC4) algorithm [ 19 ] as a solution to the widespread problem of insecure database transfer between sender and recipient. This cryptosystem safeguards sensitive information by encrypting it before sending it through a network and then decrypting it upon its safe return. Database tables have an encapsulating system that ciphers symbolize hens.
The continual improvements in digitizing have enhanced the prominence of online services. Enterprises must store essential data in corporate DB systems, including bank records, activities, the history of patient paperwork, personal data, agreements, etc. The institutions also must maintain the data’s authenticity, privacy, and availability. Any intrusion in security procedures or data may cause severe economic loss and damage the company’s reputation [ 20 ]. The remarkable development in the deployment of DB’s is the required architecture to cope with information that can be attributed to the rising big data. Every 1.2 years, according to research, the entire quantity of institutional information doubles [ 21 ].
Most of the latest studies provide encryption-based solutions for DB security. However, before proceeding towards these solutions, there is a need to find out the flaws that lead to security breaches.
One or more of the following sources can lead to a security flaw:
Interior Internal origins of attack originate from inside the corporation. Human resources—organization supervisors, admins, workers, and interns—all fall within this category of insiders. Almost all insiders are recognized in a particular way, and just a few IT professionals have significant access levels.
Exterior Exterior attacks originate from entities outside the organization instance, cybercriminals, illegal parties of established ways, and government agencies. Usually, no confidence and trust, or benefit is offered for external sources.
Collaborator Any third party involved in a business connection with the organization, firm, or group is considered a partner in many companies. This significant collection of partners, distributors, vendors, contractual labor, and customers is known as the entire enterprise. There must be some level of confidence and privilege of accessibility or record among colleagues in the entire enterprise; therefore, this is often advised.
2.1 Secure databases
With incredibly high secure data and an expanded online presence, the worries concerning DB security are high at all-time. As more systems are connected and brought online to improve access, the sensitivity towards attacks is also increased, estimated to be about $1.3 million in massive financial losses; these mischievous attacks are also liable for public reputation and client relations with the association [ 21 , 22 ]. All users can boundlessly get information from the DB server in an un-secure DB system. All hosts are allowed to associate with the server from any IP address and link with the DB server, making everyone’s information accessible in the storage engine [ 23 , 24 ].
Hence, the DB system is retained with numerous security mechanisms which contain anticipation of unauthorized access to data from an insider or outsider of an organization. Proper encryption techniques should be applied to secure the DB’s [ 25 ]. The most comprehensive secure DB model is the multilevel model, which allows the arrangement of information according to its privacy and deals with mandatory access control MAC [ 7 ]. DB services are intended to ensure that client DB’s are secure by implementing backup and recovery techniques [ 26 ].
The DB can be protected from the third party, which is not authorized by the procedure called cryptography and utilizing other related techniques. The primary motivation behind DB security is ensuring data privacy from unauthorized outsiders. The essential techniques in DB security are authentication, confidentiality, and integrity, which are utilized to secure the DB’s [ 27 ]. DB construction, in particular, must consider security as the main goal while developing a data system. In this respect, security should be addressed at all stages of the software development process [ 7 , 28 , 29 , 30 ].
2.2 Related work
Various articles examine the importance of security controls from the perspective of software engineering [ 31 ]. For instance, MÁRQUEZ et al. [ 32 ] conducted a systematic survey concentrating on the telemedicine platform’s safety from the software engineering viewpoint. The key focus of this article is investigating how Software development assists in designing a reliable telehealth platform. However, the proposed work is just restricted to, particularly telehealth systems.
Al-Sayid et al. [ 1 ] notably studied the challenges of data stores and proposed DB security issues. To prevent unauthorized access to or alteration of the DB’s critical material, they observed a wide variety of DB security issues. Another research by Zeb focuses on identifying potential attacks on the DB system using a standard research study. Mousa et al. [ 33 ] discover the various risks to DB safety in their analysis through the unstructured research study. Moghadam et al. [ 15 ] did an investigation on cloud servers to figure out all conceivable threats.
Nevertheless, this analysis is solely restricted to the cloud DB environment. The researchers Segundo Toapanta et al. [ 5 ] uncovered real-world examples of cybercrime. Apart from that, their research is restricted to cyberattacks.
The authors in [ 21 ] have suggested an innovative technique for spotting distinct threats to DB systems by assessing the risk for incoming new activities. Their research discovered various harmful attacks that could harm the DB system. The emphasis of their research is only confined to security assessment involving DB’s. Experts in [ 32 ] present a comprehensive mapping analysis, and their observations are only limited to the Telehealth system’s privacy from the software engineering point of view. They did not define the security problems in creating, implementing, and managing safe DB’s. Furthermore, with the rapid development of ICTs, it is essential to be up to date on the most recent developments in this field.
The primary goal of this research is to gain a greater understanding of this topic by conducting a Systematic Mapping Survey to identify the problems in building, managing, and sustaining reliable DB’s.
3 Research methodology
The goal of this study was accomplished by evaluating the current state of DB privacy and suggesting areas that needed further research work. With the SMS, researchers may better connect the data from literary research to a series of questions [ 34 , 35 ]. SMS is a descriptive investigation that involves picking and putting combine all published research articles associated with a particular challenge and gives a broad summery of existing materials relating to the particular questions. In the near future, software engineers will benefit significantly from SMS because it provides a comprehensive overview of the research in the field. Figure 2 outlines the process that was followed to conduct the mapping study.
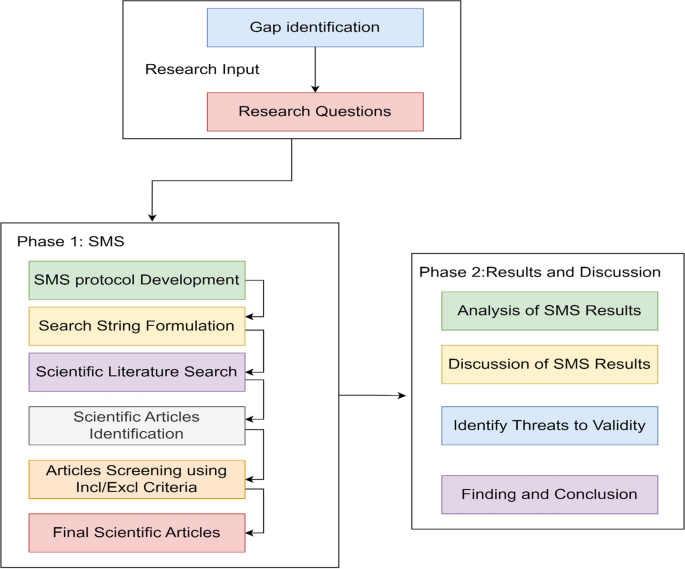
SMS process
3.1 Research questions
Our primary objective is to find the obstacles in planning, creating, and managing data protection. To achieve this objective, relevant study questions have been devised.
RQ 1 What is the current state of the art in the development and implementation of secure DBs?
To address RQ1, we have studied the material depending on the sub-questions mentioned above:
RQ 1.1 n terms of reliable data modeling, development, and maintenance, which stage has received the most attention in the research?
RQ 1.2 What are the primary sites for robust DB design?
RQ 1.3 What are the ongoing research organizations working in robust data modeling?
RQ 1.4 What kinds of DB attacks have been described in the research?
RQ 1.5 According to the research, what are the various categories of DB's?
RQ 1.6 What kinds of DBMS platforms are often employed, as stated in the literature.
RQ 2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
3.2 Search strategy
The scholars in [ 36 , 37 , 38 ] employed the PICO (Population, Intervention, Comparison, and Outcomes) framework to develop a list of terms and then drew search terms from research questions.
Population DB’s and software development in general.
Intervention Security Strategies.
Comparison No assessments proceed for the ongoing investigation.
Outcomes Reliable DB’s.
3.3 Search strings
After several tries, the following two search terms were selected to link the PICO aspects by utilizing Boolean connector (AND):
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database intrusion” OR “Database prevention”) AND (“Security Mechanisms” OR “Security Models” OR “Security methods” OR “Security policies” OR “Security techniques” OR “Security Guidelines”)).
For Science Direct online repository, we compressed the above search term due to space limits. As a result, the accompanying keywords were entered into the ScienceDirect database:
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database prevention”) AND (“Security Mechanisms” OR “Security methods” OR “Security techniques” OR “Security guidelines”)).
3.4 Literature resources
We choose below digital repositories (A to F) to do our SMS and execute the search stings for acquiring publications.
IEEE xplore–B
Springer link–C
AIS electronic library (AiSel)–D
Science direct–E
Wiley online library–F
3.5 Research evaluation criteria
Titles, abstracts, entire readings, and quality assessments were all factors in our selection of research publications. The primary goal of the selection process is to compile an appropriate collection of papers by imposing inclusion and exclusion standards on submissions. We have set the accompanying inclusion and exclusion criteria to perform our SMS effectively. The same inclusion and exclusion criteria have been used in other studies [ 39 , 40 , 41 ]
3.5.1 Inclusion criteria
Only articles that meet one or more of the below criteria were considered for inclusion in our collection.
I1 Research involving the design and implementation of database security measures.
I2 Research that explains how to protect DB’s.
I3 Research the difficulties and dangers of creating, implementing, and maintaining safe DB’s.
I4 Research on the planning, development, and management of reliable DB's included in this category.
3.5.2 Exclusion criteria
The preceding exclusion criteria were considered to find relevant articles.
E1 Publications that are not published in the English language.
E2 No consideration will be given to materials that haven’t been published in any journal, magazine, or conference proceedings, such as unpublished books and grey material.
E3 Books as well as non-peer-reviewed articles, including briefs, proposals, keynotes, evaluations, tutorials, and forum discussions.
E4 Articles that aren’t published in their whole digital.
E5 Publications that don’t meet the inclusion requirements.
E6 Research is only provided as abstracts or PowerPoint slides.
We used the snowballing approach [ 42 , 43 , 44 ] in addition to the previous inclusion/exclusion criteria for our concluding decision. The snowball method was used to choose seven articles from various research repositories. Appendix 1 contains the papers selected using the snowballing approach, from 94 to 100. In the latest research, scholars have employed the same method [ 45 , 46 ].
3.6 Quality evaluation
All articles chosen in the selection have been evaluated for quality. Criteria for quality evaluation include:
To evaluate the papers, we used a three-point Likert scale (yes, partially, no) for every element of the quality evaluation criteria. We awarded each element of quality assessment criteria a score of 2 (yes), 1 (partially), or 0 (no) to achieve notable findings. Including an article in the SMS is permitted if it gained an average standard score of > or = 0.5. Many other scholars [ 45 , 47 , 48 , 49 ] have employed a similar approach. A list of all of the questions from Table 1 is included in the quality ranking.
3.7 Article selection
Employing Afzal et al. tollgate’s technique, we adjusted the key publication selection in our SMS analysis upon executing the search terms (Sect. 3.3 ) and online DB’s (Sect. 3.4 ) [ 50 ]. The five stages of this method are as follows: (Table 2 ).
Stage1 (St-1) Conducting literature searches in digital repositories/DB’s for most relevant articles.
Stage 2 (St-2) A article’s inclusion or removal is based on its title and abstract readings.
Stage 3 (St-3) To determine if an item should be included or not, the introduction and findings must be reviewed.
Stage 4 (St-4) the inclusion and exclusion of data analysis research are based on a full-text review of the research's findings.
In Stage 5 (St-5) most of the original studies that will be included in the SMS study have been vetted and selected for inclusion.
There were 4827 documents collected from the chosen web-based libraries/DB’s by imposing inclusion and exclusion criteria following the initial search string iteration (see Sect. 3.3 ). (Sects. 3.5.1 and 3.5.2 , respectively). The tollgate strategy led to a shortlist of 100 publications that were eventually selected for the research. Quality evaluation criteria were used to evaluate the selected articles (Sect. 3.6 ). Appendix 1 includes a collection of the publications that were ultimately chosen.
3.8 Extracting and synthesizing content
A survey of the articles reviewed is used to obtain the data. In order to address the questions stated in Sect. 3.1 , the entire content of every article has been reviewed, and pertinent data extracted. You can find a precise technique for extracting data in the SMS Protocol.
4 Description of key findings
A comprehensive mapping analysis was used throughout this study to determine current state-of-the-art and privacy issues in data modeling, development, and maintenance. Sections 4.1 , 4.2 , 4.3 , 4.4 , 4.5 and 4.6 contain the facts of our observations.
4.1 The current state of the art
RQ1 has been addressed using the below sub-questions as a reference (Sects. 4.1.1 , 4.1.2 , 4.1.3 , 4.1.4 , 4.1.5 and 4.1.6 ).
4.1.1 Stages in the building of a protected database
RQ 1.1 focuses on a reliable DB’s most frequently studied stages (design, development, and maintenance). As seen in Table 3 , the “design” step was mentioned in most publications at a rate of 27%. There is a 25 percent chance that you’ll hear about the “developing” stage. The “maintenance” stage was only mentioned in 5 of our SMS research findings.
4.1.2 Well-known sources for the building of reliable DB’s
RQ 1.2 is addressed in the second part of this SMS, which concentrates on the location of the papers chosen for this SMS. For venue and provider type analyses, we looked at five repositories, including A, B, C, D, and E. Tables 4 and 5 exhibit the snowballing method, which we refer to as “others.” Several of the papers from these collections were presented at conferences, journals, and workshops/symposia, among other venues. As shown in Table 4 , 45 out of 100 articles were published through the conference venue. Secondly, we found that, with a rate of 37 out of 100, a large percentage of the publications came from the journal channel. Workshops and symposiums accounted for 18% of the articles presented.
Table 4 lists a total of 100 articles spanning a wide range of topics related to DB privacy. This indicates that scholars have devoted a great deal of attention to this topic. “International Journal of Information Security(IJIS)”, “The International Journal on Very Large Data Bases (VLDB)”, “Computers and Security (C&S)”, “Digital Investigation (DI)”, “Journal of Natural Sciences (JNS)” and “Journal of Zhejiang University SCIENCE A (JZUS-A)” were found to be the most popular publications for privacy mechanisms in secure DB designing, as mentioned in Table 5 . We also discovered that the “Annual Computer Security Applications Conference(ACSAC)” and the “International Workshop on Digital Watermarking(IWDW)” are the most often referred articles on the issue of our research. Software engineering and other related domains can benefit greatly from DB privacy studies.
4.1.3 Research institutions participating in the construction of a reliable DB
The institution of the first researcher was utilized to determine and evaluate the highly ongoing researching institutes in the field of protected DB’s. Table 6 shows the findings for RQ 1.3, which reveal that “University of Florida, USA (UOF)” and “CISUC, University of Coimbra, Portugal (UOC)” produced the most research publications on protected DB’s (3 percent, each, out of 100). Ben-Gurion University of the Negev (BGU); RMIT University in Melbourne, Australia; YONSEI University in Seoul; TELECOM Bretagne in Brest, France(ENST); Anna University in Chennai, India (AUC); Huazhong University of Science and Technology in Wuhan (HUST); and George Mason University in Fairfax, Virgin Islands(GMU). BGU has presented two publications for each of the selected research.
4.1.4 The most common kind of DB attacks, according to academic research
RQ 1.4 is concerned with identifying the many kinds of DB attacks that have been recorded. Table 7 shows the three types of incidents: internal, external, and both (internal and external). To effectively understand intrusions, we must combine cyber-attacks with breaches by collaborators. Because both internal and external attacks are mentioned in one article, we refer to this as both (internal and external). Our SMS study’s “Both (Internal & External)” attacks had a rate of 52, according to the assessment in Table 7 . The bulk of the articles in our SMS survey highlighted “External” attacks with a frequency of 35%. In total, 13 papers in our SMS addressed the topic of “internal” attacks.
4.1.5 Database types that have been identified in the literature
To answer RQ 1.5, we must recognize the various DB’s discussed in the literature. Seventeen different DB’s have been documented in the research based on the data we gathered from the articles we included in our SMS. Table 8 shows that of the 100 articles in our SMS survey, 24 papers mentioned the term “Web DB.” Secondly, we found that “Commercial DB” appeared in 11 of the 100 articles in our SMS analysis. According to SMS, “multilevel DB and distributed DB” was mentioned in ten publications.
4.1.6 Kinds of database management systems (DBMS) presented in the research
Data management systems (DBMS) are examined in RQ 1.6. In this research, 11 distinct DBMS types have been documented based on our SMS data, which was gathered from a selection of studies. Most of the articles in our SMS survey mentioned an “Oracle DB system” with a 31 out of 100 rate, as shown in Table 9 . Secondly, “MySQL DB system” was mentioned in most of the publications in our SMS analysis (23 out of 100). Our SMS research found 21 publications that mentioned the term “SQL Server DB system.”
4.2 Issues in databases
As demonstrated in Table 10 and Fig. 3 our existing research into DB privacy has uncovered 20 issues from a pool of 100 studies (see Appendix 1 ).
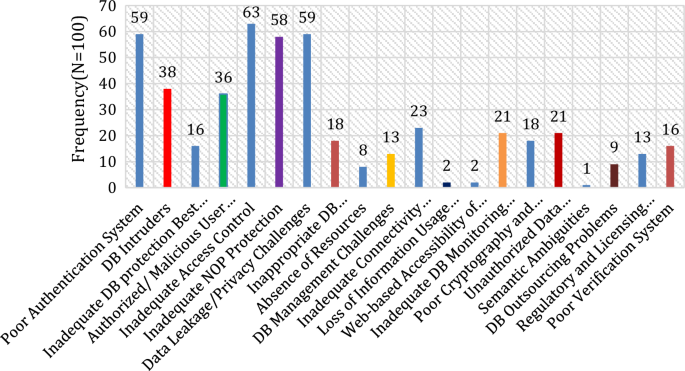
Issues in DB security
CC #1 Poor authentication system An unauthorized individual gains access to a DB, harvests vital information, and allows the hostile attacker to violate the safety of certified DB’s [ 1 , 51 ].
CC #2 Database intruders We are talking about when we say “threat database attacks” Anonymous queries (anomalous query attack), Harmful queries (query flood attack), and Inferential Attacks (polyinstantiation issue, aggregate problem).
CC #3: Inadequate database protection Best Strategies Specifications Engineering, Architectural, Planning, and Development all suffer from the absence of proper security procedures.
CC #4 Authorized/Malicious User Threats An authorized individual, employee, or administrator may collect or disclose critical data [ 52 ].
CC #5 Inadequate access contro Whenever many persons need access to the information, the risk of data fraud and leakage increases. The access should be restricted and regulated [ 1 ]
CC #6 Inadequate NOP protection Inadequate NOP Protection is a shortage of network privacy, operating system privacy, and physical safety.
CC #7 Data leakage/privacy challenges Clients of database systems are increasingly concerned about information security. Attacks on disclosed confidential information, including passwords, emails, and private photographs, triggered this issue. Individuals and database systems cannot stop the propagation of data exploitation and destruction once the content has been leaked [ 53 ].
CC #8 Inappropriate database implementation/configuration/maintenance Numerous DB’s are improperly setup, formatted, and maintained, among the main reasons for database privacy issues [ 54 ].
CC #9 Absence of resources When we talk about a shortage of resources, we are talking about a need of trained employees, a lack of time and budget, a shortage of reliable resources, and an insufficient storage capacity, to name a few things.
CC #10 Database management challenges There are aspects of effectively handling database systems, connectivity, and information at different levels [ 53 ].
CC #11 Inadequate connectivity platforms Presently, the majority of customer, user, and third-party conversations are conducted online. The inclusion of an insecure transmission medium was driven by the Internet’s opportunity to link DB’s [ 1 ].
CC #12 Loss of information usage monitoring Several users are unconcerned regarding their communications but may inadvertently send important information to an unauthorized person or untrustworthy servers. Because of a shortage of supervision of data consumption, they are also lost and destroyed [ 1 ].
CC #13 Web-based accessibility of tools for database attacks Several tools being used for intrusions are accessible in this globally networked domain, allowing intruders to expose weak spots with minimal expertise of the victim DB architecture [ 1 ].
CC #14 Inadequate database monitoring strategy Regulatory risk, discovery, mitigation, and restoration risk are just a few of the dangers posed by a lack of DB auditing [ 1 ].
CC #15 Poor cryptography and anonymization No DB privacy plan, regulation, or technology would be sufficient without cryptography, whether the information is traveling over a network or being kept in the DB system [ 1 ].
CC #16 Unauthorized data alteration/deletion Any type of unauthorized information alteration or deletion can result in substantial economic losses for an organization or corporation [ 55 ].
CC #17 Semantic ambiguities DB issues, including semantic uncertainty, which arises from an absence of semantics or inadequate semantic descriptions, dissemination issues, updating scope constraints, and tuple mistrust, are addressed [ 56 , 57 ].
CC #18: DB outsourcing problems : Because so many DB’s are now being outsourced, there are serious concerns about the data’s accuracy and safety. Clients will have to relinquish management of the information they have outsourced [ 58 , 59 ] .
CC #19 Regulatory and licensing challenges DB’s have many security issues, including policy and licensing concerns. Would the corporation have a consistent and approved policy and licensing from the authorities or organization [ 1 , 60 ]?
#20 Poor verification system A poor verification system allows an attacker to assume the credentials of a legitimate DB and access its data. The invader has a wide range of options for determining the identification of data. Assuming passwords are easy to remember [ 1 ] or using a preset username and password.
4.3 An assessment of database protection issues based on continents
There is much research on various continents in our SMS findings. A comparative analysis of only three continents, i.e., Europe, North America, and Asia, is discussed in this work (See Appendix 2 for more details). We want to find out if these issues are different across continents. We believe that by examining the similarities and distinctions among these problems, we may better prepare ourselves to deal with them on the continent in question. We employed the sequential correlation chi-square test to determine whether there were notable variations among the issues in the three continents listed previously (Martin, 2000). There are many more similarities than distinctions among the issues in the three continents. Poor authentication systems, DB intruders, inadequate DB protection best strategies, and authorized/ malicious user threats are the only major differences found in Table 11 . According to our findings, the most prevalent risks in the three continents are “Inadequate Access Control” (65%, 57%, and 64%), “Inadequate NOP Protection” (59%, 57%, and 60%), “Data Leakage/Privacy Challenges” (49%, 60%, 64%), and “Authorized/Malicious Individuals Threats” (40%, 20%, and 52%). It is not uncommon to see “Authorized/Malicious User Threats,” “Inadequate Access Control,” and “Inadequate NOP Security” across Europe and Asia. Inadequate Connectivity Platforms, Poor Verification Systems, Data Leakage/Privacy Challenges, and Regulatory and Licensing Challenges are some of the problems North American and European clients/users face while creating safe DB’s, as shown in Table 11 . According to our research, the “Poor Verification System” problem affects the most significant number of customers and users in Asia (78 percent). “Data Leakage/Privacy Challenges” is the most common issue faced by European customers and individuals (60 percent). Many customers in North America face “Inadequate Access Control” and “Data Leakage/Privacy Challenges” concerns, respectively (i.e., 64 percent) (Fig. 4 ).
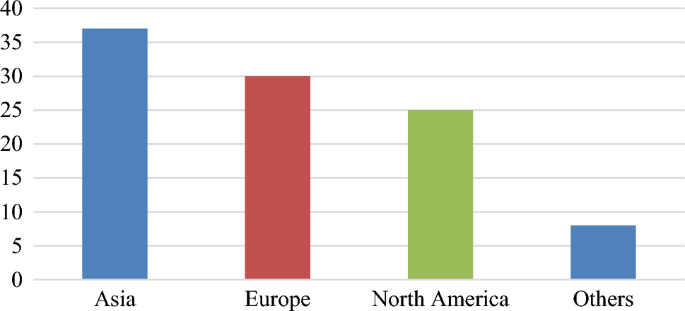
Distribution depending on continents
4.4 Methodological assessment of database privacy issues
Table 12 shows how we divided the different types of difficulties into three distinct approaches. Table 12 shows the three approaches used: tests, Ordinary literature review OLR, and Other/Mixed Approaches as shown in Fig. 5 . Other techniques include writing an experience report, conducting a case study, conducting a survey, and utilizing fuzzy methodologies. When we talk about “many methodologies,” we mean that more than one is employed in a single work. Testing is commonly utilized (39 out of 100 times, according to Table 12 ). The second notable finding in our SMS research is that 31 of the 100 participants used a standard literature review approach. Appendix 2 has further information. Many issues have been revealed by studying the distribution of publications among the three methodologies. Seventeen issues have been detected in relation to OLR, as shown in Table 12 . Two of the Seventeen issues have been mentioned in over 50% of the publications. Inadequate Access Control (74%), and Data Leakage/Privacy Challenges (52%), are two of the most often stated problems. Tests face a total of 18 difficulties. Four of these 18 issues have been quoted more than 50% of the time in at least one of the publications. “Data Leakage/Privacy Challenges—64 percent”, “Inadequate NOP Protection—62 percent”, “Poor Authentication System—56 percent”, and “Inadequate Access Control—56 percent” are among the most often stated difficulties. Other/Mixed Approaches publications have highlighted twenty difficulties. Moreover, half of the publications cited 4 of the 20 issues listed. “Poor Authentication System—73%”, “Inadequate NOP Protection—63%”, “Inadequate Access Control—60%”, and “Data Leakage/Privacy Challenges—60%” are among the most frequently stated problems.
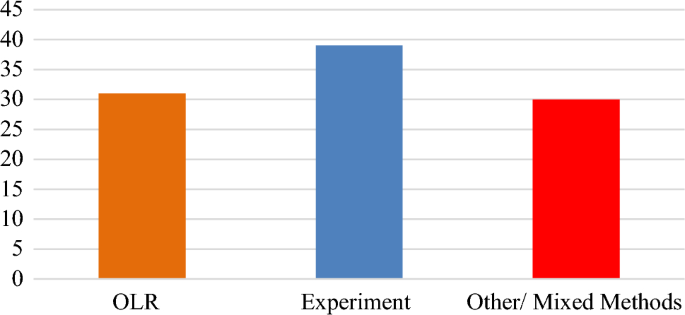
Methodological-based distribution of papers
Table 12 shows that no SMS approach was employed in any studies (n = 0). These findings prove that our study methodology is innovative in this particular field. We performed the Linear-by-Linear Chi-Square test for the earlier research-mentioned techniques and methodologies to establish whether there was a substantial difference between the challenges. “Poor Authentication System” and “Inappropriate DB implementation/configuration/maintenance” are the only notable variances.
4.5 Years-based study of database privacy issues
A comparison of issues over two time periods, 1990–2010 and 2011–2021, is shown in Table 13 and presented in Fig. 6 . More information can be found in Appendix 2 . Within the first phase; we found that 18 issues had been highlighted in the research. Four of the 18 issues have been quoted more than 50% in the publications. Inadequate Access Control (70 percent), Poor Authentication System (65 percent), Inadequate NOP Protection (62 percent), and Data Leakage/Privacy Challenges (52 percent) are the most commonly stated vulnerabilities. Between 1990 and 2010, 70 percent of DB’s had Inadequate Access Control, indicating that designers failed to effectively control access permission throughout implementationcontrol access permission throughout implementation.
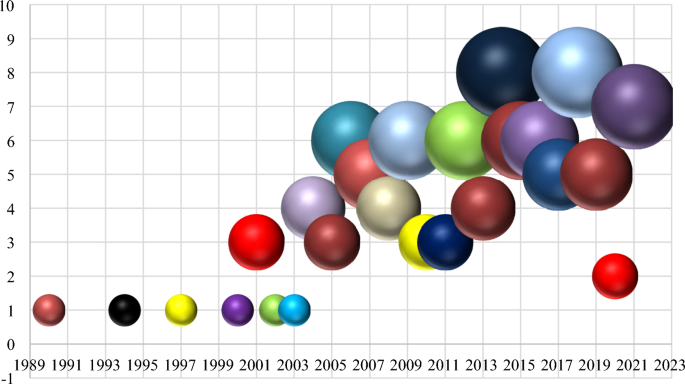
Year-based distribution of publications
Furthermore, admins in an organization are liable for ensuring that data is adequately protected via access permissions. The “Inadequate Access Control” difficulty has dropped to 58 percent in the second period. The literature has revealed 19 problems for the second time period. Four of the 19 obstacles have been referenced in at least half of the publications. “Data Leakage/Privacy Challenges” accounts for 63% of the faults, “Inadequate Access Control” for 58%, “Poor Authentication System” for 55%, and “Inadequate NOP Protection” for 55% of the issues, respectively. We used the Linear-by-Linear Chi-Square analysis and only identified a substantial variation for one problem, “DB Management Challenges, “with a p -value of less than.05.
4.6 Evaluation of articles based on their venue
Table 14 displays a breakdown of the various distribution methods. In addition to Journals, Symposiums, Conferences, and Workshops, we have presented our final articles on extracting data via SMS in various other publications venues as well. Journals, Workshops/Symposiums, and conferences have been classified into three categories for easy study. We found that 45 percent of our comprehensive study of articles was presented at conferences, according to Table 14 and Fig. 7 . Additionally, 37% of the publications in Table 14 were presented in new journals. For further information, please see Appendix 2 at the ending of the study. Many issues have been discovered as a result of distributing papers via these three channels. According to our findings, 18 issues with journals need to be addressed. Four of the 18 challenges have been referenced in at least half of the publications. “Privacy Issues/Data Leakage—84 percent,” “Inadequate Access Control”—59 percent, “Inadequate NOP Protection”—59 percent,” and “Poor Authentication System—54 percent” are the most often stated difficulties. Conferences face a total of 20 obstacles. Three of these 20 difficulties have been quoted more than 50% of the time in at least one publication. “Poor Authentication System—71 percent,” “Inadequate Access Control—69 percent,” and “Inadequate NOP Protection—62 percent” are the most often stated issues. Workshops/Symposiums face a total of 16 difficulties. Two issues have been mentioned in over half of the publications out of the 16 total. “Data Leakage/Privacy Challenges—61 percent” and “Inadequate Access Control—56 percent” are the most commonly reported hurdles. Linear-by-Linear Chi-Squared test has been used to find substantial differences throughout the difficulties. We have found just one big variation between the hurdles “Data Leakage/Privacy Challenges”.
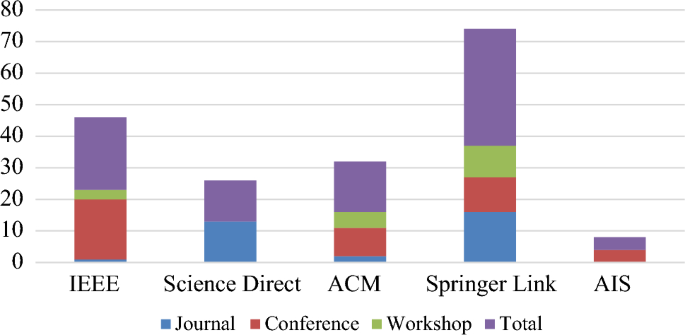
Venue-based distribution of articles
4.7 Comparison with existing studies
A wealth of studies have delved into various aspects of database security. Some of these have centered their attention on securing data transmission from server to client, while others have prioritized the construction of secure databases through secure coding practices. The increasing dependence on geographically dispersed information systems for daily operations might augment productivity and efficiency but simultaneously heightens the risk of security violations. Current security measures ensure data transmission protection, yet a comprehensive security strategy must also encompass mechanisms to enforce diverse access control policies. These policies should consider the content sensitivity, data attributes and traits, and other contextual data such as timing.
The consensus in the field is that effective access control systems should integrate data semantics. Moreover, strategies ensuring data integrity and availability must be customized for databases. Consequently, the database security community has developed an array of strategies and procedures over time to safeguard the privacy, integrity, and accessibility of stored data.
Nonetheless, despite these advancements, fresh challenges persist in the database security landscape. Evolving threats, data access “disintermediation,” and emerging computing paradigms and applications like grid-based computing and on-demand business have all introduced new security demands and innovative contexts where existing methodologies can be employed or extended. Despite a multitude of available solutions, raising awareness about existing security breaches is critical for bolstering database security.
In response, we decided to conduct a Systematic Mapping Study (SMS) on secure databases to offer an up-to-date perspective for both database users and developers. We did not find any comprehensive systematic literature review (SLR) or mapping study on this topic to draw comparisons with. However, we believe this research will offer a strategic roadmap for all database stakeholders.
5 Practical implications of research
The practical implications of this research are manifold and impactful. Initially, the results of this SMS will serve as an invaluable resource for DB privacy professionals and users. By leveraging the insights from this study, experts gain an enhanced understanding of DB privacy issues that need addressing. Consequently, they can prioritize their focus on the most significant security challenges. This, in turn, equips DB users with an awareness of their potential privacy risks. Thus, this study benefits consumers by assisting organizations in developing secure DB systems, mindful of the challenges they face (Table 10 ).
Furthermore, professionals such as DB designers, project managers, and scholars specializing in secure DB design are keen to keep abreast of the latest developments. This research provides DB developers with insights into novel strategies for DB security and the latest advancements in DB technology. Journals such as “VLDB,” “Computers & Security,” “DI,” and “JNS” should be of particular interest to them. Consequently, they would find it beneficial to scrutinize papers available from the “ACSAC” and “IWDW” Conferences and Workshops. The aforementioned venues present optimal resources for studying reliable DB development.
These venues, recognized for their focus on secure DB design, encourage scholars to contribute high-quality academic articles. The outcomes of this study will inform experts’ decision-making processes, providing guidance on where to invest when developing tools and methodologies for safeguarding DB systems. Lastly, it underscores the need for organizations to provide appropriate training for their customers to tackle critical challenges.
Acknowledgements
The authors would like to acknowledge the support provided by the Deanship of Scientific Research via project number DF201007 at King Fahd University of Petroleum and Minerals, Saudi Arabia.
Open Access funding provided by University of Oulu including Oulu University Hospital.
Author information
Authors and affiliations.
Department of Computer Science and IT, Software-Engineering-Research-Group (SERG-UOM), University of Malakand, Chakdara, Pakistan
Asif Iqbal & Siffat Ullah Khan
Information and Computer Science Department, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Mahmood Niazi
Interdisciplinary Research Center for Intelligent Secure Systems, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Department of Information Systems, College of Computer and Information Sciences, Jouf University, Sakaka, 72311, Saudi Arabia
Mamoona Humayun
Faculty of Computer Science and Information Technology, Universiti Malaysia Sarawak, Kota Samarahan, Sarawak, Malaysia
Najm Us Sama
M3S Empirical Software Engineering Research Unit, University of Oulu, Oulu, Finland
Arif Ali Khan
Lancaster University Leipzig, Leipzig, Germany
Aakash Ahmad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Arif Ali Khan .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
See Table 15 .
See Table 16 .
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Iqbal, A., Khan, S.U., Niazi, M. et al. Advancing database security: a comprehensive systematic mapping study of potential challenges. Wireless Netw (2023). https://doi.org/10.1007/s11276-023-03436-z
Download citation
Published : 17 July 2023
DOI : https://doi.org/10.1007/s11276-023-03436-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Database security
- Systematic mapping study
- Secure databases
- Modeling and maintenance of protected databases
- Issues in the development
- Find a journal
- Publish with us
- Track your research
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that’s compromised in most data breaches.
Database security must address and protect the following:
- The data in the database.
- The database management system (DBMS).
- Any associated applications.
- The physical database server or the virtual database server and the underlying hardware.
- The computing or network infrastructure that is used to access the database.
Database security is a complex and challenging endeavor that involves all aspects of information security technologies and practices. It’s also naturally at odds with database usability. The more accessible and usable the database, the more vulnerable it is to security threats; the more invulnerable the database is to threats, the more difficult it is to access and use. This paradox is sometimes referred to as Anderson’s Rule (link resides outside ibm.com).
Get insights to better manage the risk of a data breach with the latest Cost of a Data Breach report.
Register for the X-Force Threat Intelligence Index
By definition, a data breach is a failure to maintain the confidentiality of data in a database. How much harm a data breach inflicts on your enterprise depends on various consequences or factors:
- Compromised intellectual property: Your intellectual property—trade secrets, inventions, proprietary practices—can be critical to your ability to maintain a competitive advantage in your market. If that intellectual property is stolen or exposed, your competitive advantage can be difficult or impossible to maintain or recover.
- Damage to brand reputation: Customers or partners might be unwilling to buy your products or services (or do business with your company) if they don’t feel they can trust you to protect your data or theirs.
- Business continuity ( or lack thereof): Some businesses cannot continue to operate until a breach is resolved.
- Fines or penalties for non-compliance: The financial impact for failing to comply with global regulations such as the Sarbannes-Oxley Act (SAO) or Payment Card Industry Data Security Standard (PCI DSS), industry-specific data privacy regulations such as HIPAA, or regional data privacy regulations, such as Europe’s General Data Protection Regulation (GDPR) can be devastating, with fines in the worst cases exceeding several million dollars per violation .
- Costs of repairing breaches and notifying customers: In addition to the cost of communicating a breach to customer, a breached organization must pay for forensic and investigative activities, crisis management, triage, repair of the affected systems and more.
Many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. The following are among the most common types or causes of database security attacks.
Insider threats
An insider threat is a security threat from any one of three sources with privileged access to the database:
- A malicious insider who intends to do harm.
- A negligent insider who makes errors that make the database vulnerable to attack.
- An infiltrator, an outsider who somehow obtains credentials via a scheme, such as phishing or by gaining access to the credential database itself.
Insider threats are among the most common causes of database security breaches and are often the result of allowing too many employees to hold privileged user access credentials.
Human error
Accidents, weak passwords, password sharing and other unwise or uninformed user behaviors continue to be the cause of nearly half (49%) of all reported data breaches .
Exploitation of database software vulnerabilities
Hackers make their living by finding and targeting vulnerabilities in all kinds of software, including database management software. All major commercial database software vendors and open source database management platforms issue regular security patches to address these vulnerabilities, but failure to apply these patches in a timely fashion can increase your exposure.
SQL or NoSQL injection attacks
A database-specific threat, these involve the insertion of arbitrary SQL or non-SQL attack strings into database queries that are served by web applications or HTTP headers. Organizations that don’t follow secure web application coding practices and perform regular vulnerability testing are open to these attacks.
Buffer overflow exploitation
Buffer overflow occurs when a process attempts to write more data to a fixed-length block of memory than it is allowed to hold. Attackers can use the excess data, which is stored in adjacent memory addresses, as a foundation from which to start attacks.
Malware is software that is written specifically to take advantage of vulnerabilities or otherwise cause damage to the database. Malware can arrive via any endpoint device connecting to the database’s network.
Attacks on backups
Organizations that fail to protect backup data with the same stringent controls that are used to protect the database itself can be vulnerable to attacks on backups.
These threats are exacerbated by the following:
- Growing data volumes: Data capture, storage and processing continues to grow exponentially across nearly all organizations. Any data security tools or practices need to be highly scalable to meet near and distant future needs.
- Infrastructure sprawl : Network environments are becoming increasingly complex, particularly as businesses move workloads to multicloud or hybrid cloud architectures, making the choice, deployment and management of security solutions ever more challenging.
- Increasingly stringent regulatory requirements: The worldwide regulatory compliance landscape continues to grow in complexity, making adhering to all mandates more difficult.
- Cybersecurity skills shortage: Experts predict there might be as many as 8 million unfilled cybersecurity positions by 2022 .
Denial of service (DoS and DDoS) attacks
In a denial of service (DoS) attack, the attacker deluges the target server—in this case the database server—with so many requests that the server can no longer fulfill legitimate requests from actual users, and, often, the server becomes unstable or crashes.
In a distributed denial of service attack (DDoS), the deluge comes from multiple servers, making it more difficult to stop the attack.
Because databases are network-accessible, any security threat to any component within or portion of the network infrastructure is also a threat to the database, and any attack impacting a user’s device or workstation can threaten the database. Thus, database security must extend far beyond the confines of the database alone.
When evaluating database security in your environment to decide on your team’s top priorities, consider each of the following areas:
- Physical security: Whether your database server is on-premises or in a cloud data center, it must be located within a secure, climate-controlled environment. If your database server is in a cloud data center, your cloud provider takes care of this for you.
- Administrative and network access controls: The practical minimum number of users should have access to the database, and their permissions should be restricted to the minimum levels necessary for them to do their jobs. Likewise, network access should be limited to the minimum level of permissions necessary.
- User account and device security: Always be aware of who is accessing the database and when and how the data is being used. Data monitoring solutions can alert you if data activities are unusual or appear risky. All user devices connecting to the network housing the database should be physically secure (in the hands of the right user only) and subject to security controls at all times.
- Encryption: All data, including data in the database and credential data, should be protected with best-in-class encryption while at rest and in transit. All encryption keys should be handled in accordance with best practice guidelines.
- Database software security: Always use the latest version of your database management software, and apply all patches when they are issued.
- Application and web server security: Any application or web server that interacts with the database can be a channel for attack and should be subject to ongoing security testing and best practice management.
- Backup security: All backups, copies or images of the database must be subject to the same (or equally stringent) security controls as the database itself.
- Auditing: Record all logins to the database server and operating system, and log all operations that are performed on sensitive data as well. Database security standard audits should be performed regularly.
In addition to implementing layered security controls across your entire network environment, database security requires you to establish the correct controls and policies for access to the database itself. These include:
- Administrative controls to govern installation, change and configuration management for the database.
- Preventive controls to govern access, encryption, tokenization and masking.
- Detective controls to monitor database activity monitoring and data loss prevention tools. These solutions make it possible to identify and alert on anomalous or suspicious activities.
Database security policies should be integrated with and support your overall business goals, such as protection of critical intellectual property and your cybersecurity policies and cloud security policies . Ensure that you have designated responsibility for maintaining and auditing security controls within your organization and that your policies complement those of your cloud provider in shared responsibility agreements. Security controls, security awareness training and education programs, and penetration testing and vulnerability assessment strategies should all be established in support of your formal security policies.
Today, a wide array of vendors offer data protection tools and platforms. A full-scale solution should include all of the following capabilities:
- Discovery: Look for a tool that can scan for and classify vulnerabilities across all your databases—whether they’re hosted in the cloud or on-premises—and offer recommendations for remediating any vulnerabilities that are identified. Discovery capabilities are often required to conform to regulatory compliance mandates.
- Data activity monitoring: The solution should be able to monitor and audit all data activities across all databases, regardless of whether your deployment is on-premises, in the cloud, or in a container . It should alert you to suspicious activities in real-time so that you can respond to threats more quickly. You’ll also want a solution that can enforce rules, policies and separation of duties and that offers visibility into the status of your data through a comprehensive and unified user interface. Make sure that any solution you choose can generate the reports you need to meet compliance requirements.
- Encryption and tokenization capabilities: Upon a breach, encryption offers a final line of defense against compromise. Any tool that you choose should include flexible encryption capabilities that can safeguard data in on-premises, cloud, hybrid or multicloud environments. Look for a tool with file, volume and application encryption capabilities that conform to your industry’s compliance requirements, which might demand tokenization (data masking) or advanced security key management capabilities.
- Data security optimization and risk analysis: A tool that can generate contextual insights by combining data security information with advanced analytics will enable you to accomplish optimization, risk analysis and reporting with ease. Choose a solution that can retain and synthesize large quantities of historical and recent data about the status and security of your databases, and look for one that offers data exploration, auditing and reporting capabilities through a comprehensive but user-friendly self-service dashboard.
Continuous edge-to-edge cloud protection for your data and applications with regulatory compliance.
Wide visibility, compliance and protection throughout the data security lifecycle.
Comprehensive data protection for the most critical enterprise data.
Learn more about data organization in the cloud.
Now in its 17th year, the 2022 Cost of a Data Breach report shares the latest insights into the expanding threat landscape and offers recommendations for how to save time and limit losses.
In this introduction to networking, learn how computer networks work, the architecture used to design networks, and how to keep them secure.
Learn how the IBM Security Guardium family of products can help your organization meet the changing threat landscape with advanced analytics, real-time alerts, streamlined compliance, automated data discovery classification and posture management.

COMMENTS
A rare exception was the data breach of U.S. bank Capital One. The incident, which was the result of an unauthorized access to their cloud-based servers hosted at Amazon Web Service (AWS), took place on March 22 and 23, 2019.
Here is a brief review of seven well-known data breaches caused by human error. 1. Equifax data breach—Expired certificates delayed breach detection. In the spring of 2017, the U.S. Department of Homeland Security's Computer Emergency Readiness Team (CERT) sent consumer credit reporting agency Equifax a notice about a vulnerability affecting ...
The 15 biggest data breaches of the 21st century. Analysis. Nov 08, 2022 15 mins. Application Security Cybercrime Data and Information Security. Data breaches affecting millions of users...
Data Security in Databases: Exploring Case Studies. In today's digital world, the security of data stored in databases has become a critical concern for organizations and individuals alike.
In our digital world, robust cybersecurity is critical. Each of the 15 case studies in this collection explores the challenges, strategies, and results of securing digital assets against cyber threats.
Our results show that “weak authorization system”, “weak access control”, “privacy issues/data leakage”, “lack of NOP security”, and “database attacks” as the most frequently cited critical challenges.
The Deep Dive connects the dots between CSA Top Threats through the use of nine real-world attacks and breaches. Pulling from one of the case studies, this article provides a security analysis overview of the Amazon Ring data breach.
Figures (1) Abstract and Figures. In this paper, we review security and usability scenarios. We propose security enhancements without losing usability and apply a new approach to popular...
Usability and Security Go Together: A Case Study on Database. Publisher: IEEE. Cite This. PDF. Yong Wang; Bharat Rawal; Qiang Duan; Ping Zhang. All Authors. 4. Cites in. Papers. 531. Full. Text Views. Abstract.
What is database security? Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that’s compromised in most data breaches. Database security must address and protect the following: The data in the database.